Why use TrustZone?
Summary
Contents
- 1 Summary
- 2 What is the difference between TEE and TrustZone
- 3 Is TrustZone a TPM
- 4 What is the TrustZone in the ARM Cortex
- 5 What is Qualcomm TrustZone
- 6 How TrustZone works
- 7 What is the difference between Hypervisor and TrustZone
- 8 What is the difference between Intel Platform Trust and TPM
- 9 What is TrustZone technology for ARMv8-M architecture
- 10 What is the use of TrustZone in Android
- 11 Is TrustZone a good VPN
- 12 Difference between TrustZone and TrustZone-M
- 13 Types of server virtualization
- 14 Most commonly used hypervisor in server virtualization
In this article, I will be discussing TrustZone technology and its applications. TrustZone is a hardware-based security feature built into modern ARM processors, which aims to provide a secure execution environment. It allows for the isolation of code and data from the rest of the operating system, providing a Trusted Execution Environment (TEE).
What is the difference between TEE and TrustZone
TrustZone is one of many hardware features that can be used to build a TEE. It provides hardware and memory isolation, separating computer resources between two execution worlds: the normal world and the secure world.
Is TrustZone a TPM
While TrustZone is a mandatory feature for all ARMv8 devices, it does not implement the TPM specification. However, software running inside the SecureWorld can implement TPM protocols, as TrustZone provides a location for secure computation.
What is the TrustZone in the ARM Cortex
ARM TrustZone is a hardware security extension technology that splits computer resources between the normal world and the secure world. It aims to create a secure execution environment by providing secure and non-secure worlds that are hardware separated.
What is Qualcomm TrustZone
Qualcomm TrustZone is a TEE that allows running a secure OS, known as the Secure World, alongside the normal OS, which is the Normal World.
How TrustZone works
TrustZone works by creating secure and non-secure worlds that are hardware separated. Non-secure software is blocked from accessing secure resources directly, enhancing security and preventing unauthorized access.
What is the difference between Hypervisor and TrustZone
While TrustZone is limited to two worlds, the secure and normal worlds, a hypervisor can host any number of operating systems. TrustZone offers secure and non-secure worlds, each with their own supervisor OS, while a hypervisor allows for multiple OS instances.
What is the difference between Intel Platform Trust and TPM
Intel Platform Trust Technology (PTT) implements TPM in system firmware, allowing it to act as a TPM to the operating system and applications. The difference is that computers with Intel PTT do not require a dedicated processor or memory for TPM functionality.
What is TrustZone technology for ARMv8-M architecture
TrustZone technology for ARMv8-M supports multiple Secure function entry points, whereas TrustZone technology for Cortex-A processors only has a single entry point called the Secure Monitor handler. Non-secure interrupts can be serviced while executing a Secure function.
What is the use of TrustZone in Android
TrustZone is a hardware-based security feature in every modern ARM processor, providing hardware support for creating a separated secure environment. It allows for the secure placement and use of private assets in Android applications.
Is TrustZone a good VPN
TrustZone is a VPN service that offers good performance and decent features at an affordable price. It performs well in tests and provides VPN apps for Windows, Android, and iOS.
Difference between TrustZone and TrustZone-M
TrustZone-M is memory map-based, where memory areas and other critical resources are marked as secure and can only be accessed when the processor is executing in secure state. TrustZone-A, on the other hand, provides hardware separation between the secure and normal worlds.
Types of server virtualization
There are three main types of server virtualization: full-virtualization, para-virtualization, and OS-level virtualization. Each type offers different approaches and benefits for virtualized server environments.
Most commonly used hypervisor in server virtualization
The most commonly deployed type 1 or bare-metal hypervisor is widely used in server virtualization. It is installed directly on the hardware, separate from the operating system, offering enhanced security by isolating the hypervisor from potential attacks.
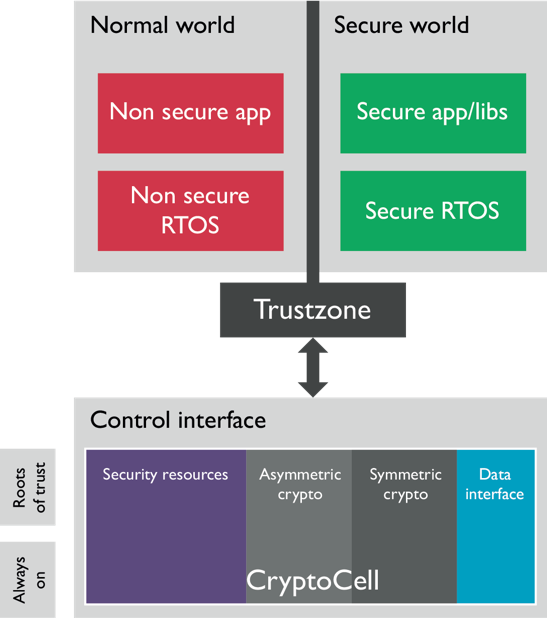
What is the difference between TEE and TrustZone
TrustZone is one of many hardware features that can be used to build a “Trusted Execution Environment” (TEE), aiming to provide hardware and memory isolation of code and data from the rest of the operating system.
Is TrustZone a TPM
All arm v8 devices must implement TrustZone as part of its specification. TrustZone does not implement the tpm specification. However, since it provides a location for secure computation, software can implement tpm protocols safely while running inside the SecureWorld.
What is the TrustZone in the arm cortex
Abstract—ARM TrustZone is a hardware security extension technology, which aims to provide secure execution environment by splitting computer resources between two execution worlds, namely normal world and secure world.
Cached
What is Qualcomm TrustZone
The Arm TrustZone is a TEE which allows running a secure OS (Secure World) along the normal OS (Normal World).
How TrustZone works
How Does TrustZone for Cortex-A Work At the heart of the TrustZone approach is the concept of secure and non-secure worlds that are hardware separated, with non-secure software blocked from accessing secure resources directly.
What is the difference between Hypervisor and TrustZone
In contrast, a Hypervisor is rarely limited to two worlds. Hypervisors host any number of OS's. TrustZone only has two worlds; secure and normal. Although each world can have a controlling supervisor OS, with many separate threads, tasks, or processes as the OS permits.
What is the difference between Intel platform trust and TPM
Intel Platform Trust Technology (PTT) architecture implements TPM in system firmware. To your operating system and applications, PTT looks and acts like TPM. However, the difference between PTT vs TPM is that computers with Intel PTT don't require a dedicated processor or memory.
How does TrustZone work
TrustZone technology for Arm Cortex-M processors enables robust levels of protection at all cost points for IoT devices. The technology reduces the potential for attack by isolating the critical security firmware, assets and private information from the rest of the application.
What is TrustZone technology for ARM v8 M architecture
TrustZone technology for ARMv8-M supports multiple Secure function entry points, whereas in TrustZone technology for Cortex-A processors, the Secure Monitor handler is the sole entry point. Non-secure interrupts can still be serviced when executing a Secure function.
What is the use of TrustZone in Android
TrustZone is a hardware-based security feature built into every modern ARM processor. Using TrustZone, you have hardware support for creating a separated secure environment to place and use in your private assets.
Is Trust zone a good VPN
Zone is one of the cheapest VPN services on the market that still performs well. It offers good performance, some decent features, and good basic VPN apps for Windows, Android, and iOS. We found that Trust. Zone did well in all of the tests we conducted for this review.
What is the difference between TrustZone and TrustZone M
Unlike in TrustZone-A, TrustZone-M is memory map based: Memory areas and other critical resources are marked as secure and then can only be accessed when the core is executing in secure state. The program address, the address of the instruction currently executed, determines the security state of the processor.
What are the three types of server virtualization
There are three main types of server virtualization: full-virtualization, para-virtualization, and OS-level virtualization.
What type of hypervisor is most commonly used in server virtualization
The most commonly deployed type of hypervisor is the type 1 or bare-metal hypervisor, where virtualization software is installed directly on the hardware where the operating system is normally installed. Because bare-metal hypervisors are isolated from the attack-prone operating system, they are extremely secure.
What is the downside of TPM
Disadvantages of TPM
Management is not willing to initiate a continuous improvement process with a long ROI, in which all employees contribute their knowledge and skills to sustainably increase value creation. Management is not willing to invest a lot of time in training and education of their employees.
Is TPM actually useful
TPM Overview. The TPM is a cryptographic module that enhances computer security and privacy. Protecting data through encryption and decryption, protecting authentication credentials, and proving which software is running on a system are basic functionalities associated with computer security.
Is Trust zone VPN legit
zone is a good VPN service. However, it's good as long as you need to become more secure online. This VPN uses advanced encryption, has a kill switch, and it's possible to use the WireGuard tunnel.
What is STM32 TrustZone
The STM32 MPU is based on the Arm® Cortex®-A core, which is using the Arm® TrustZone architecture that enables context isolation: the normal world holds the applications whereas the secure world isolates all the trusted applications and core secure services so that they can safely manipulate platform secret data.
What is Samsung Trust Zone
Generally, TrustZone is used to access hardware-backed features and to perform sensitive operations in a supervised manner (e.g. cryptographic engine, credentials storage, etc.). Samsung heavily uses TrustZone for Samsung Knox, a system-wide security toolbox developed by Samsung.
How do I disable TrustZone
To disable TrustZone®, you have to:Step 1: Connect Boot0 to VDD on your board:Step 2: Connect your board with STM32CubeProgrammer in "hot plug" Mode.Step 3: Switch RDP value in “readout protection” to level 1, then click on apply.Switch RDP value to level 0.Step 5: Then click on apply to program the option bytes.
What is the safest VPN to use
The Best VPNs of 2023NordVPN: Best Overall.TorGuard VPN: Most Customizable VPN.TunnelBear: Best for Beginners.Private Internet Access: Best for Customizable Security.ProtonVPN: Best for Tor Integrations.hide.me: Best for Wi-Fi Security.Surfshark: Best for Unlimited Connections.
How does trust zone work
How Does TrustZone for Cortex-A Work At the heart of the TrustZone approach is the concept of secure and non-secure worlds that are hardware separated, with non-secure software blocked from accessing secure resources directly.
What are 3 benefits of server virtualization
Improved server reliability and availability, Lower total operational cost. More efficient utilization of physical servers. More efficient utilization of power.
What are the 4 major virtualization areas
It's time to get this straight.Network virtualization. Network virtualization takes the available resources on a network and breaks the bandwidth into discrete channels.Storage virtualization.Desktop virtualization.Application virtualization.
Which type of hypervisor is more efficient
Type 1 hypervisors are highly efficient because they have direct access to physical hardware. This also increases their security, because there is nothing in between them and the CPU that an attacker could compromise.