Is SSH obsolete?
Summary
Contents
SSH (Secure Shell) is still relevant in today’s cloud computing environment as it provides a secure way to solve connectivity problems and protect virtual machines from security threats. However, there are alternatives to SSH for remote access, such as Telnet, Mosh, and VPN.
Main Thought
I personally believe that SSH is an essential tool for secure remote access and data transfer in cloud computing.
Key Points
1. SSH in Cloud Computing
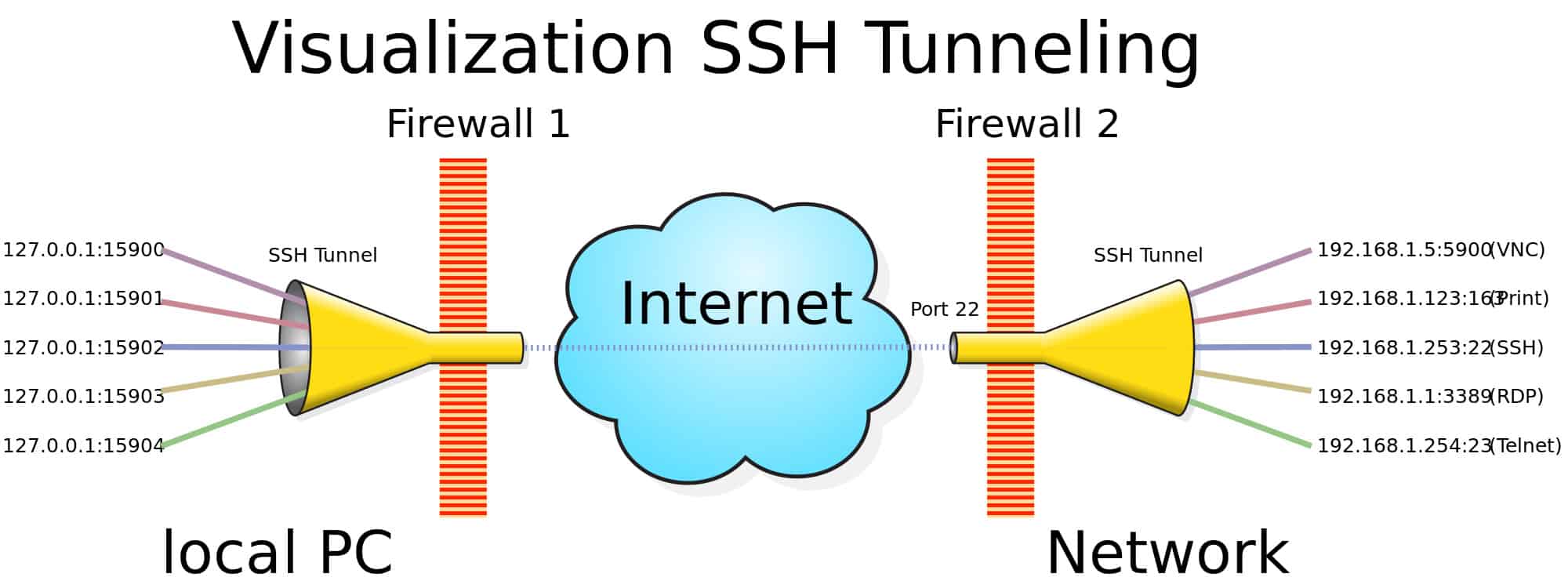
SSH is important in cloud computing to solve connectivity problems, avoiding the security issues of exposing a cloud-based virtual machine directly on the Internet. An SSH tunnel can provide a secure path over the Internet, through a firewall to a virtual machine.
2. Alternatives to SSH
There are alternatives to SSH for remote access. Telnet is an old method that lacks security but still has some uses. Mosh makes SSH connections more reliable over wireless connections, and VPN offers access to intranet resources remotely with less need for technical knowledge.
3. Insecurity of SSH
SSH may be considered insecure because your organization may not have policies in place to control credentials. Over time, employees come and go, and they may also change roles. If there is no mechanism to disable SSH access when needed, SSH would be insecure.
4. How SSH is Used Today
SSH is often used to “login” and perform operations on remote computers, but it can also be used for transferring data securely.
Questions and Answers
1. Is SSH still relevant in cloud computing?
Yes, SSH is still relevant in cloud computing as it provides a secure way to solve connectivity problems and protect virtual machines from security threats.
2. Are there alternatives to SSH for remote access?
Yes, there are alternatives to SSH for remote access, such as Telnet, Mosh, and VPN.
3. Why is SSH considered insecure?
SSH may be considered insecure if there are no policies in place to control credentials and disable SSH access when needed.
4. How is SSH used today?
SSH is often used to “login” and perform operations on remote computers, as well as securely transfer data.
5. What are the disadvantages of using SSH?
Disadvantages of SSH include the need for knowledge and skills to use it properly, such as generating and managing keys, troubleshooting errors, and its potential slowness compared to Telnet due to encryption and authentication overhead.
6. Is VPN better than SSH?
A VPN and SSH serve different purposes. A VPN encrypts and protects all data exchanged, while SSH works on an application level. The choice depends on the specific needs and use case.
7. Is SSH a vulnerability?
Inefficient management of SSH keys can expose organizational networks to security vulnerabilities, compromising data confidentiality and integrity.
Overall, SSH remains a valuable tool for secure remote access and data transfer, but organizations need to implement proper policies and practices to ensure its security.
Is SSH still relevant
SSH is important in cloud computing to solve connectivity problems, avoiding the security issues of exposing a cloud-based virtual machine directly on the Internet. An SSH tunnel can provide a secure path over the Internet, through a firewall to a virtual machine.
Cached
What is the replacement for SSH
There are alternatives to SSH for remote access. Telnet is an old method that lacks security but still has some uses. Mosh makes SSH connections more reliable over wireless connections and VPN offers access to intranet resources remotely with less need for technical knowledge.
Why SSH is not recommended
SSH may be considered insecure because your organization may not have policies in place to control credentials. Over time employees come and go. They may also change roles. If there is no mechanism to disable SSH access when needed, SSH would be insecure.
How is SSH used today
SSH is often used to "login" and perform operations on remote computers but it may also be used for transferring data.
What is a disadvantage to using SSH
Disadvantages of SSH
SSH also requires some knowledge and skills to use properly, such as generating and managing keys, choosing encryption algorithms, or troubleshooting errors. SSH can also be slower than telnet, since it has some encryption and authentication overhead.
Which is better SSH or VPN
VPNs and SSH systems both create secure “tunnels” for your data to travel through. These tunnels ensure that nobody other than the intended recipient can view or alter your data. However, while an SSH connection only works on an application level, a VPN connection encrypts and protects all your data.
Can I use PuTTY instead of SSH
Secure Shell (SSH) is a network protocol used to allow secure access to a UNIX terminal. PuTTY is the recommended application to use for SSH connections from a Windows operating system. PuTTY allows you to access your files and email stored on the engineering servers.
What is faster than SSH
Speed: FTP is generally considered to be the fastest protocol for file transfer because it does not have the encryption overhead that SSH and SFTP have. However, the speed of file transfer can also depend on other factors, such as the network speed and the size of the files being transferred.
What is the SSH vulnerability 2023
What is CVE-2023-38408 CVE-2023-38408 is a vulnerability that enables remote code execution and resides in the SSH-agent's forwarded feature, particularly in relation to the PKCS#11 providers.
What is more secure than SSH
However, while an SSH connection only works on an application level, a VPN connection encrypts and protects all your data. In other words, SSH tunneling will secure data exchanged between you and a remote server you have access to, while a VPN works to encrypt your entire network.
What is the difference between SSL and SSH
SSH is primarily used for secure remote access to servers and devices, while SSL is primarily used for securing web-based communications. They use different encryption algorithms, run on different port numbers, and provide different levels of authentication and implementation.
Why do you think anyone ever need to use SSH
You probably see SSH commonly used for:
Administrating a server remotely (with OpenSSH) Authorizing remote processes, SCP for example, which allows you to send files via an SSH tunnel so the data is encrypted in transit. Providing secure access for users. Securely mounting a directory on a remote server as a file …
Is A VPN better than SSH
A VPN is easier to set up and will provide more security to businesses and a vast majority of casual users, while an SSH offers a good safe-browsing option for tech-savvy individuals within their private networks.
Is SSH a vulnerability
Inefficient management of SSH keys exposes your organizational networks to critical security vulnerabilities, compromising data confidentiality and integrity.
What are the cons of SSH
Disadvantages of SSH
SSH requires some software and settings to use, and it may not be compatible with some older or simpler devices. SSH also requires some knowledge and skills to use properly, such as generating and managing keys, choosing encryption algorithms, or troubleshooting errors.
Is SSH more secure than Remote Desktop
Though they are quite similar, there are fundamental differences between them. SSH is considered more secure because it does not require additional tools such as a Virtual Private Network (VPN) or Multi-factor authentication (MFA) as RDP does.
Why use PuTTY over SSH
PuTTY is the recommended application to use for SSH connections from a Windows operating system. PuTTY allows you to access your files and email stored on the engineering servers. It also provides a UNIX environment to run programs that some courses require.
Why do people still use PuTTY
While you can bind an address with OpenSSH on Windows, you're limited by the number of addresses you can save. There is a reason why PuTTY remains popular. Not only does it allow you to save (and name) your connections, the app also supports connections over Telnet, Serial, and other protocols.
Is PuTTY better than SSH
Secure Shell (SSH) is a network protocol used to allow secure access to a UNIX terminal. PuTTY is the recommended application to use for SSH connections from a Windows operating system. PuTTY allows you to access your files and email stored on the engineering servers.
Which is better SFTP or SSH
Simplicity: SFTP is easier to set up and configure than SSH, especially for users with little technical expertise. File Management: SFTP provides file management capabilities, including the ability to rename, delete, and move files on remote servers.
Is SSH a security risk
Although the protocol is inherently secure, the authentication mechanism, client-server configuration and machine identities — SSH keys — used to secure remote connections are open to abuse. The top six SSH risks are the following: password authentication. untracked and unmanaged keys.
Is SSH over the Internet
SSH services may be exposed directly to the Internet in some networks such as cloud environments.
Which is better SSH or SSL
SSH, or Secure Shell, is similar to SSL in that they're both PKI based and both form encrypted communication tunnels. But whereas SSL is designed for the transmission of information, SSH is designed to execute commands. You generally see SSH when you want to log in to some part of a network remotely.
Should I use SSH or HTTPS
Use SSH as a more secure option and HTTPS for basic, password-based Git usage. Since SSH is more secure than entering credentials over HTTPS, it is recommended for businesses dealing with sensitive and critical data. Once you generate the SSH keys, only the machines with the key file on disk can access the repository.
Why use SFTP instead of SSH
SSH is primarily used for remote command-line access to a system, while SFTP is designed specifically for file transfer. SSH uses public key cryptography for authentication, while SFTP uses a username and password. SSH uses port 22 for communication, while SFTP can use port 22 or 115.