Why does L2TP use UDP?
ntroduced and data integrity is crucial. UDP, on the other hand, is preferred in situations where speed and efficiency are prioritized over reliability. This includes applications such as video streaming, online gaming, and VoIP services.
To ensure that data is transmitted smoothly and quickly, UDP does not require acknowledgments of receipt or retransmissions of lost packets. While this means that UDP does not guarantee the delivery of all data, it allows for faster transmission and reduced latency.
Additionally, UDP is less resource-intensive as it does not involve the same level of error checking and retransmission mechanisms as TCP. This makes it a suitable choice for real-time applications that require quick data delivery, where occasional packet loss or out-of-order delivery is acceptable.
Moreover, UDP is commonly used in Voice over Internet Protocol (VoIP) applications, as the overall transmission arriving on time is more important than having every single packet perfectly intact. This allows for smoother audio and video streaming without delay.
In summary, UDP is preferred over TCP in situations where speed and efficiency are crucial and occasional data loss is acceptable. Its use cases include real-time applications, streaming services, and gaming, where a fast and uninterrupted data transmission is prioritized over reliability.
Does L2TP use UDP
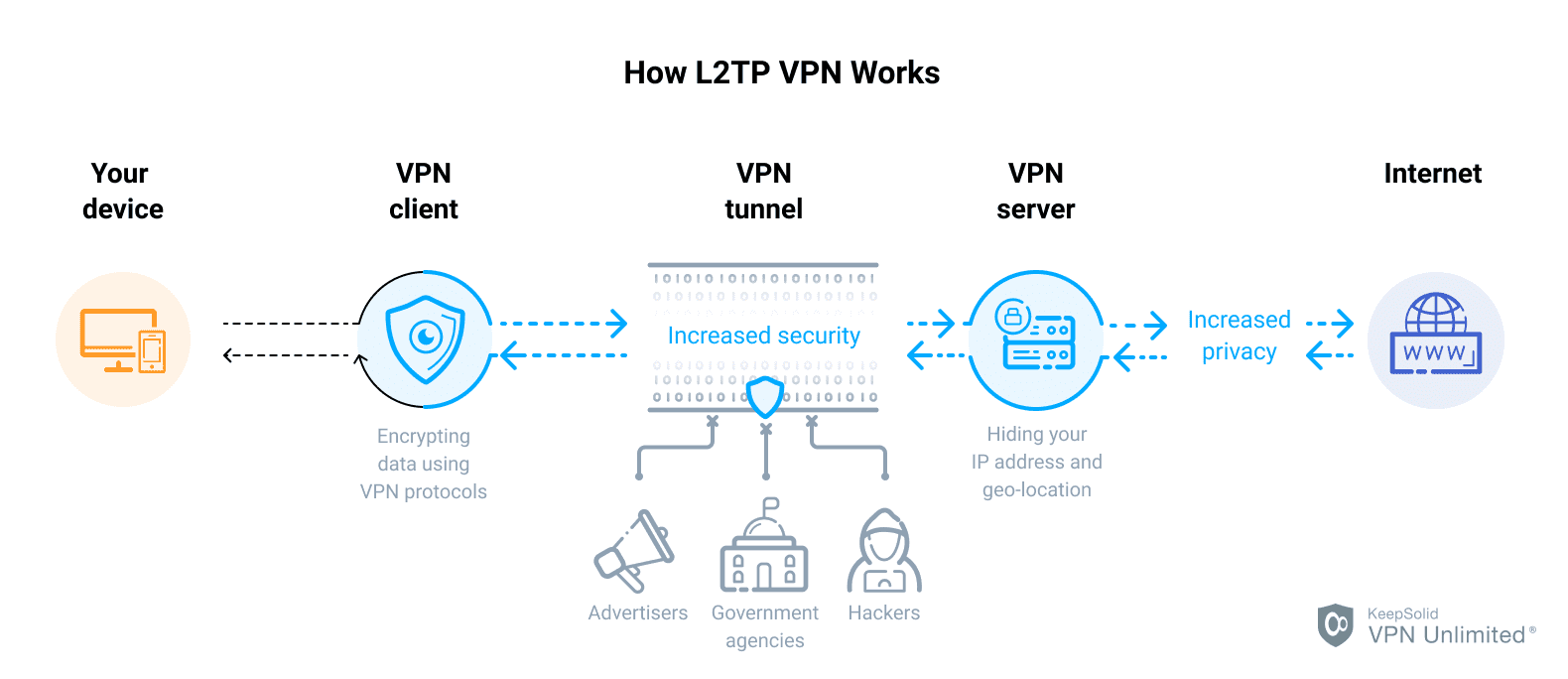
Layer Two Tunneling Protocol (L2TP) uses UDP port 1701 and is an extension of the Point-to-Point Tunneling Protocol. L2TP is often used with IPSec to establish a Virtual Private Network (VPN). Point-to-Point Tunneling Protocol (PPTP) uses TCP port 1723 and IP protocol 47 Generic Routing Encapsulation (GRE).
Why UDP is used in IPsec
IPsec uses UDP because this allows IPsec packets to get through firewalls. Decryption: At the other end of the communication, the packets are decrypted, and applications (e.g. a browser) can now use the delivered data.
What protocol does L2TP use
L2TP is actually a variation of an IP encapsulation protocol. The L2TP tunnel is created by encapsulating an L2TP frame inside a User Datagram Protocol (UDP) packet, which in turn is encapsulated inside an IP packet. The source and destination addresses of this IP packet define the endpoints of the connection.
Cached
Does L2TP need port forwarding
L2TP/IPSec requires UDP 500 and UDP 4500 forwarding. Another option is to forward all ports and protocols, which on some routers is called DMZ. A typical example of such a router is a CDCEthernet modem.
What is the weakness of L2TP
The greatest weakness of any L2TP tunnel is that it does not encrypt the traffic it transports. IPSec encryption protocol provides the mechanism necessary to secure tunneled data.
Is UDP safe for VPN
TCP is more reliable, but there are many uses where UDP is preferred and this is usually the default protocol on most VPN services. UDP is a great option if you are gaming, streaming or using VoIP services.
What is the reason to use UDP
UDP is frequently used when communications are time-sensitive. For users, it is better to have the overall transmission arrive on time than wait for it to get there in a near-perfect state. For this reason, UDP is commonly used in Voice over Internet Protocol (VoIP) applications as well.
Why is UDP better for VPN
UDP has a speed advantage because the user doesn't have to allow or acknowledge receipt of the data to be resent. This lets UDP establish connections faster and transfer data faster.
What network ports does L2TP use
L2TP uses UDP port 1701.
Why is L2TP not secure
A pure L2TP VPN is unsafe to use. It means that a VPN reroutes traffic but does not encrypt it. Therefore, users' internet activities are still susceptible to interception and tracking. Double-check if it pairs with IPSec if you're looking for a VPN with L2TP.
Why is L2TP over IPsec not recommended
A pure L2TP VPN is unsafe to use. It means that a VPN reroutes traffic but does not encrypt it. Therefore, users' internet activities are still susceptible to interception and tracking. Double-check if it pairs with IPSec if you're looking for a VPN with L2TP.
Is L2TP outdated
IPsec uses encryption algorithms and cryptographic keys to provide L2TP with the necessary encryption. IPsec also controls data that travels between the endpoints of the created connection tunnel between the end user and a VPN server online. However, L2TP is almost 24 years old, outdated, and not frequently used.
Is UDP a security risk
UDP is a simple protocol, but it has inherent vulnerabilities that make it prone to attacks, such as limited packet verification, IP spoofing and DDoS attacks. Despite its ubiquity in computer networking, User Datagram Protocol is susceptible to security vulnerabilities and attacks.
Why is UDP unreliable
UDP does not provide error correction and is therefore an unreliable protocol. In other words, delivery of packets is not guaranteed. UDP datagrams are transmitted without provision for an acknowledgment. Because there is no virtual connection between sender and receiver, UDP is also said to be connectionless.
Why would you use UDP instead of TCP
TCP is best used for direct communication in which a reliable connection is needed, such as web browsing, email, text messaging, and file transfers. UDP is best used for live and real-time data transmission when speed is more important than reliability.
Why use UDP rather than TCP
TCP is best used for direct communication in which a reliable connection is needed, such as web browsing, email, text messaging, and file transfers. UDP is best used for live and real-time data transmission when speed is more important than reliability.
Why is UDP not secure
Because of the connectionless nature of UDP, it is almost impossible to define a reasonable firewall policy that allows some UDP communications and blocks others. Many of the protocols that are implemented over UDP are easily exploitable.
Is L2TP 1701 TCP or UDP
UDP port 1701
L2TP uses UDP port 1701.
What is UDP port 4500 used for
As port 4500 is used for NAT Traversal traffic you can do 2 things, when you have NAT addresses available you can use NAT for both ends or just one end and only have 1 end setup the VPN, for that one use hide NAT behind the gateway.
What are the disadvantages of L2TP
L2TP also has some drawbacks. These include transmission failure due to mismatched security keys, limited port support and slower speeds.
Is L2TP deprecated
L2TP and PPTP protocols are largely obsolete. Because they are so insecure, they have become incompatible with a key part of our core mission – to provide our users with industry-leading security.
Why is UDP insecure
Because of the connectionless nature of UDP, it is almost impossible to define a reasonable firewall policy that allows some UDP communications and blocks others. Many of the protocols that are implemented over UDP are easily exploitable.
What is the main disadvantage of UDP
Disadvantages of UDP
It's connectionless, which makes data transfer unreliable. There's no system in place to acknowledge a successful data transfer. There's no way to know if data is delivered in its original state, or at all. It has no error control, so it drops packets when errors are detected.
Why is UDP worse than TCP
The difference is that TCP will recognize the loss and identify the lost packet to retransmit the information. UDP has no way to tell if packets are lost in transmission, which ones were lost, or how to resend them. This makes UDP less reliable, despite being more efficient.
Why would anyone use UDP
UDP is commonly used for applications that are “lossy” (can handle some packet loss), such as streaming audio and video. It is also used for query-response applications, such as DNS queries.