When should I use site to site VPN?
Summary
In this article, I will be discussing site-to-site VPNs and their benefits. I will cover the differences between site-to-site VPNs and other types of VPNs, their limitations, and their use cases. Additionally, I will address common questions about site-to-site VPNs and provide answers to help clarify any confusion.
Main Thought
Site-to-site VPNs offer enhanced security compared to other VPN types. With IPsec protocols, all traffic is encrypted in transit through the VPN tunnel, preventing any interception attempts from outsiders.
Main Thought
It is important to understand the difference between point-to-site VPNs and site-to-site VPNs. While site-to-site VPNs enable applications across an entire external network to access resources seamlessly, point-to-site VPNs are specific to individual client computers that are external to the network.
Key Points
1. Scalability is one of the limitations of site-to-site VPNs. As each connected site requires a unique connection, the number of VPNs needed for a fully-connected network grows exponentially with the number of sites.
2. The performance of site-to-site VPNs can vary depending on multiple factors, such as network conditions and configurations. Maximum performance can reach up to 1.25 gigabits per second (Gbps) and 140,000 packets per second (PPS) per tunnel.
3. When choosing between remote access VPNs and site-to-site VPNs, consider the use case. Site-to-site VPNs are commonly used in office LANs to connect branch offices to headquarters, while remote access VPNs are utilized by roaming users who need secure access to resources.
4. Site-to-site VPNs rely on IPSec protocols, which encrypt IP traffic and ensure secure communication between on-premises networks and virtual cloud networks (VCNs).
5. An example of a site-to-site VPN is connecting a company’s headquarters in one location to a smaller branch office in another location. This technology is particularly useful for secure information sharing in remote work and eLearning scenarios.
6. Setting up a site-to-site VPN in OCI (Oracle Cloud Infrastructure) offers benefits such as consistent network experience, redundant VPN tunnels, and configurable routing options.
7. It is important to consider the limitations and potential drawbacks of using VPNs all the time. VPNs might reduce connection speeds, increase mobile data usage, and be considered an offense in some countries.
Questions and Answers
1. Question: When should I use site-to-site VPN?
Answer: Site-to-site VPNs are best suited for connecting multiple office locations securely.
2. Question: What is the difference between site-to-site VPN and IPSec?
Answer: Site-to-site VPNs utilize IPSec protocols to establish secure connections between networks and ensure encrypted data transfer.
3. Question: What are the two types of site-to-site VPNs?
Answer: Intranet-based VPNs connect offices within the same company, while extranet-based VPNs connect offices between different companies.
4. Question: What are the key benefits of setting up a site-to-site VPN in OCI (Oracle Cloud Infrastructure)?
Answer: Benefits include consistent network experience, redundant VPN tunnels, and the ability to configure static or dynamic routing (BGP).
5. Question: What is the difference between IPSec and VPN site-to-site?
Answer: IPsec VPNs securely connect entire networks or remote users, providing site-to-site or point-to-site connectivity.
6. Question: Can you use a site-to-site VPN for multiple external networks?
Answer: Yes, site-to-site VPNs can connect multiple external networks securely.
Conclusion
Site-to-site VPNs offer enhanced security and connectivity for organizations with multiple office locations. They use IPSec protocols to encrypt data in transit and ensure secure communication. Understanding the differences between site-to-site VPNs and other VPN types, their limitations, and best use cases can help organizations make informed decisions about their network security needs.
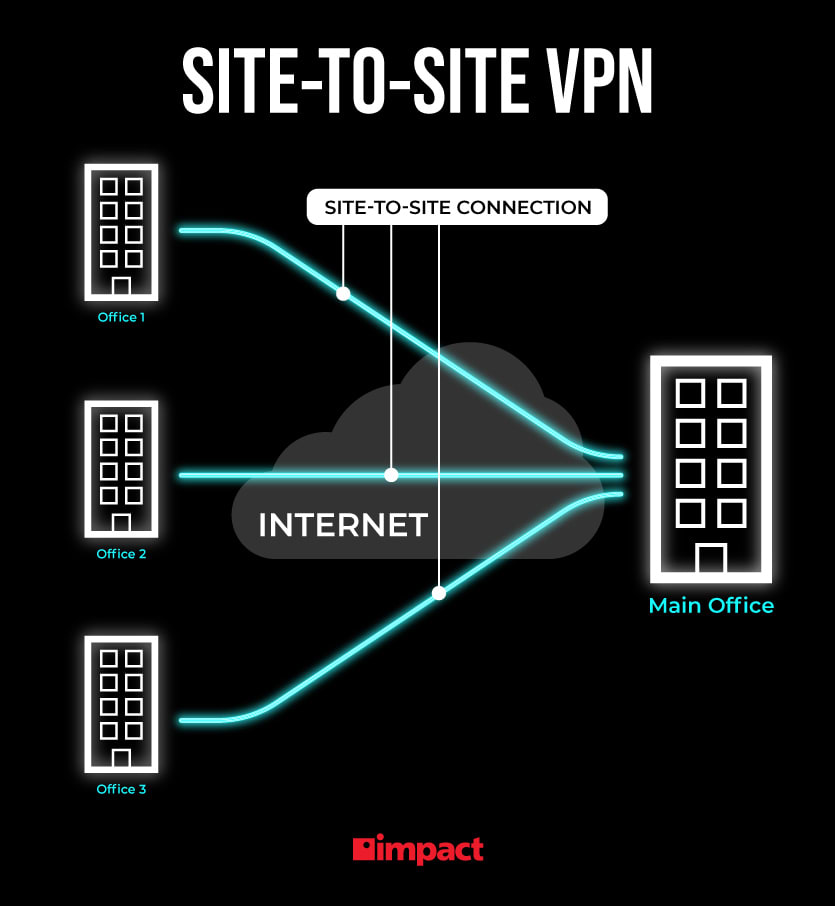
Why is site-to-site VPN better
Site-to-site VPN security is the most important benefit, as IPsec protocols will ensure all traffic is encrypted in transit through the VPN tunnel. The site-to-site VPN tunnel only allows traffic from one end to the other, blocking any attempts to intercept the traffic from the outside.
What is the difference between point to site VPN and site-to-site VPN
A site-to-site VPN connection enables applications running in an entire external network to seamlessly access the Azure SQL databases. A point-to-site VPN connection is specific to an individual client computer that is external to Azure.
What are the limitations of site-to-site VPN
Limitations of Site-to-Site VPN
Limited Scalability: A VPN provides point-to-point connectivity, meaning that a unique connection is required for each pair of connected sites. As a result, the number of VPNs required for a fully-connected network grows exponentially with the number of sites.
Is site-to-site VPN fast
If you've read the Site-to-Site VPN FAQ or quotas pages, then you may have seen a maximum performance of up to 1.25 gigabits per second (Gbps) and 140,000 packets per second (PPS) per tunnel. These are estimated maximums based on our experience, but the maximums are dependent on several factors.
Which is better remote access VPN or site to site VPN
Site-to-Site VPN is widely used in Office LAN users of branch offices that need to connect to servers located at the headquarters. Remote Access VPN is used for Roaming users who want to access resources/servers securely.
What is the difference between site to site VPN and IPSec
Site-to-Site VPN provides a site-to-site IPSec connection between your on-premises network and your virtual cloud network (VCN). The IPSec protocol suite encrypts IP traffic before the packets are transferred from the source to the destination and decrypts the traffic when it arrives.
What is an example of a site to site VPN
For example, a site-to site VPN would allow a company's headquarters in Chicago to connect to a smaller branch in Long Beach, California. Due to the rise of remote work and eLearning, businesses take advantage of this tech to share information securely.
Which is better site to site VPN or remote access VPN
Site-to-Site VPN is widely used in Office LAN users of branch offices that need to connect to servers located at the headquarters. Remote Access VPN is used for Roaming users who want to access resources/servers securely.
Why you shouldn’t use VPN all the time
Why shouldn't I use a VPN A VPN might reduce your connection speed even if your internet service provider isn't throttling your speed; Using a VPN on mobile will increase your mobile data usage; Using a VPN is considered an offense in some countries, and you can get fined or even be incarcerated for it.
What are the two types of site to site VPN
2. Site to Site VPNIntranet based VPN: When several offices of the same company are connected using Site-to-Site VPN type, it is called as Intranet based VPN.Extranet based VPN: When companies use Site-to-site VPN type to connect to the office of another company, it is called as Extranet based VPN.
Which two are key benefits of setting up site to site VPN on OCI
A. When setting up Site-to-Site VPN, it creates a private connection that provides consistent network experience.B.When setting up Site-to-Site VPN, OCI provisions redundant VPN tunnels.When setting up Site-to-Site VPN, customers can configure it to use static or dynamic routing (BGP).
What is site to site VPN vs IPSec
Site-to-Site VPN provides a site-to-site IPSec connection between your on-premises network and your virtual cloud network (VCN). The IPSec protocol suite encrypts IP traffic before the packets are transferred from the source to the destination and decrypts the traffic when it arrives.
What is the difference between IPSec and VPN site to site
IPsec VPN securely interconnects entire networks (site-to-site VPN) OR remote users with a particular protected area such as a local network, application, or the cloud. SSL VPN creates a secure tunnel from the host's web browser to a particular application.
Is there a downside to VPN
One reason why you may not want to use a VPN is because it could slow down your internet connection speed significantly. There are several factors that affect your internet speeds when using a VPN, including the fact that a VPN encrypts your data and routes it through different servers, which slows down the process.
Is it OK to be connected to VPN all the time
VPN can be kept on all the time
To sum it up, keeping your VPN on all the time is not only perfectly safe but actually recommended. It can keep your online identity anonymous, protect you from attacks associated with unsecured public Wi-Fi networks and help you bypass various artificial restrictions.
What is the difference between site to site VPN and peering
While VPN is used to connect networks over the internet, VPC peering is a quick and affordable solution to link VPCs located in the same or different Amazon accounts. Both offer a safe means of sending data across a network, but they are different in terms of network design, security, cost, and complexity.
What is the difference between IPsec and VPN site to site
IPsec VPN securely interconnects entire networks (site-to-site VPN) OR remote users with a particular protected area such as a local network, application, or the cloud. SSL VPN creates a secure tunnel from the host's web browser to a particular application.
What is the difference between site to site VPN and FastConnect OCI
Site-to-site VPN: Provides a site-to-site IPSec VPN between your on-premises network and your VCN over a secure, encrypted connection. See Site-to-Site VPN. FastConnect: Provides a dedicated private connection between your data center and Oracle Cloud Infrastructure.
What is the difference between site to site and IPSec VPN
Site-to-Site VPN provides a site-to-site IPSec connection between your on-premises network and your virtual cloud network (VCN). The IPSec protocol suite encrypts IP traffic before the packets are transferred from the source to the destination and decrypts the traffic when it arrives.
What will a VPN not protect you from
It's important to remember that VPNs do not work in the same way as comprehensive anti-virus software. While they will protect your IP and encrypt your internet history, but that is as much as they can do. They won't keep you safe, for instance, if you visit phishing websites or download compromised files.
Can your internet provider see your history with a VPN
Your ISP can't see your browsing history when you use a VPN. Everything you do stays private when you connect to a VPN server. Premium VPNs, like PIA, reroute your traffic through their own DNS servers, which conceals your DNS requests from your ISP.
How long should you stay connected to VPN
But if you're using a VPN for privacy reasons or to keep yourself anonymous online, then you should keep it on all the time. Since your VPN is your best form of protection against hackers and helps keep your information private, it's best to leave your VPN on whenever you're on the internet.
When should I use a VPN on my phone
All data traveling between your computer, smartphone or tablet and the VPN server is securely encrypted. The most typical scenario where you might use a VPN is if you're working remotely and using your laptop to connect to a specific private network, thus protecting your sensitive data.
Can the police track a VPN
With a VPN on, the user's online activities and data are encrypted. But, if the VPN software has security flaws and vulnerabilities, the police (or any other third party, for that matter) can use them to “break into” the VPN and see what data is being sent and received. So technically, the policy could track a VPN.
Can my ISP see what sites I visit with VPN
VPNs encrypt all internet traffic, effectively hiding your browsing history from your ISP. However, that doesn't mean the ISP is blind to your activities. They may be able to tell that you're connected to a VPN and for how long, based on the fact that the encrypted traffic is headed to an IP address of a VPN server.