What type of VPN does Meraki use?
Summary
Contents
- 1 Summary
- 2 Main Thought
- 3 Key Points
- 4 1. Meraki VPN Overview
- 5 2. Meraki and IPsec
- 6 3. Meraki VPN Authentication Method
- 7 4. IKEv2 VPN
- 8 5. SSL VPN
- 9 6. Limitations of Meraki VPN
- 10 7. How Meraki Network Works
- 11 8. DHCP or Static IP
- 12 9. IPsec vs. VPN
- 13 10. Meraki VPN and IKEv2
- 14 11. Meraki Authentication
- 15 Choosing between IKEv2 and OpenVPN
- 16 Is IKEv2 the same as IPsec?
- 17 Conclusion
- 18 Questions and Answers
- 18.1 1. What type of VPN does Meraki use?
- 18.2 2. Does Meraki have VPN capabilities?
- 18.3 3. What authentication method does Meraki VPN use?
- 18.4 4. What type of VPN is IKEv2?
- 18.5 5. What type of VPN is SSL VPN?
- 18.6 6. What are the limitations of Meraki VPN?
- 18.7 7. How does a Meraki network work?
- 18.8 8. Does Meraki use DHCP or static IP?
- 18.9 9. Is IPsec the same as VPN?
- 18.10 10. Does Meraki VPN support IKEv2?
- 18.11 11. How does Meraki authentication work?
- 18.12 12. Should I use IKEv2 or OpenVPN?
- 18.13 13. Is IKEv2 the same as IPsec?
In this article, we will discuss various aspects of VPNs, specifically focusing on Meraki VPN. We will explore the type of VPN used by Meraki, its authentication method, and other related questions.
Main Thought
Meraki is a popular VPN service that offers secure connections for users. It utilizes the password authentication protocol (PAP) to transmit and authenticate credentials. PAP authentication is always transmitted inside an IPsec tunnel between the client device and the MX security appliance using strong encryption.
Key Points
1. Meraki VPN Overview
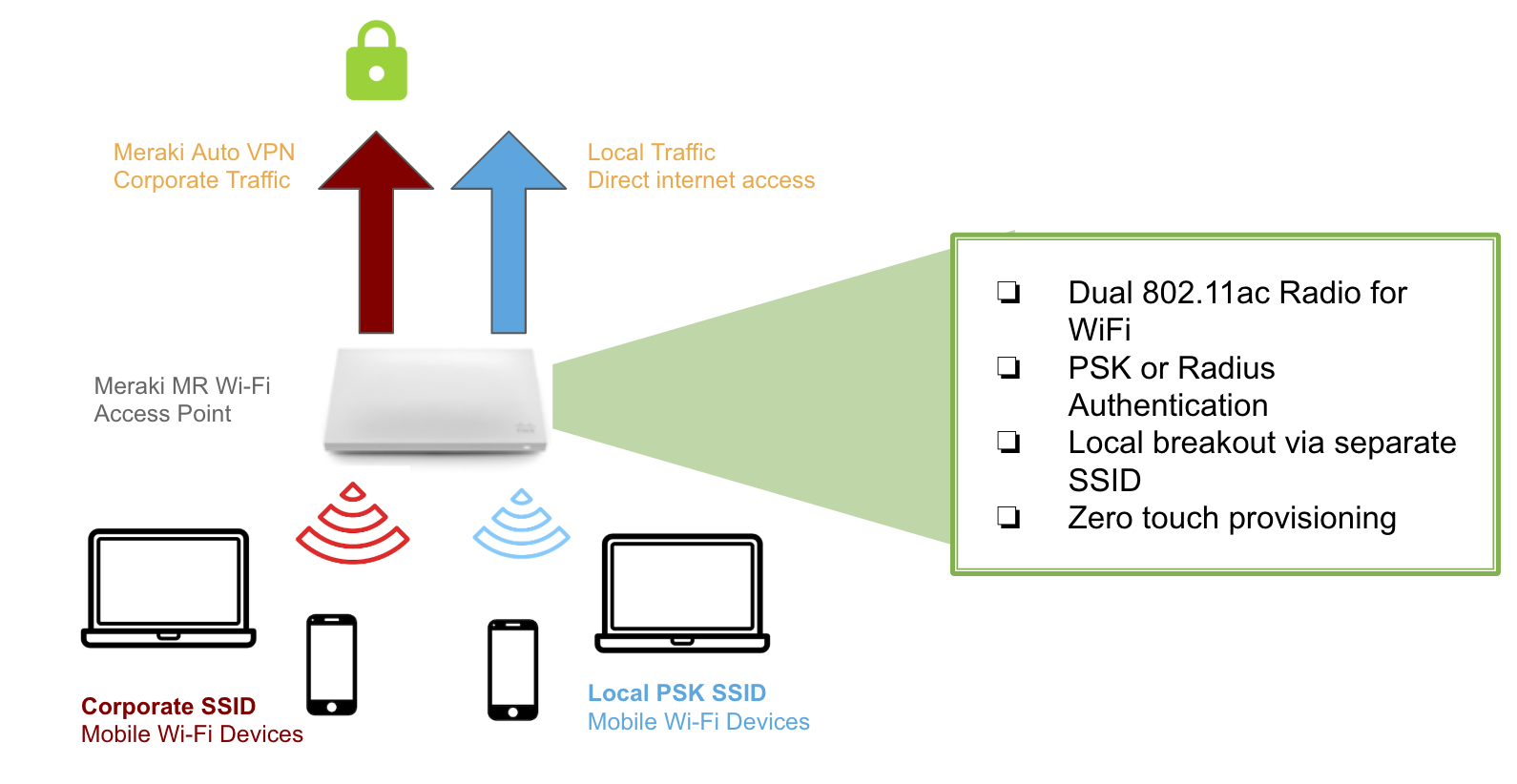
Meraki provides a proprietary technology called Auto VPN that allows users to quickly build VPN tunnels between Meraki MX devices at separate network branches with just a few clicks. This simplifies the manual VPN configuration process with a cloud-based approach.
2. Meraki and IPsec
Meraki uses IPsec as the underlying protocol for establishing VPN tunnels. It establishes all the necessary information to create an IPSec tunnel through a mutually trusted source. It also utilizes UDP holepunching to create these VPN tunnels.
3. Meraki VPN Authentication Method
Meraki supports various authentication methods for its client VPN. These include mobile token authentication using tools like Authy Authenticator, SMS-based authentication, SMS with link, and email-based authentication using OTP over email.
4. IKEv2 VPN
IKEv2 VPN is a widely used VPN protocol that combines the IKEv2 key management protocol and the IPsec protocol. It provides secure tunneling and data transportation between devices and VPN servers.
5. SSL VPN
SSL VPN is another type of VPN that enables individual users to access an organization’s network, client-server applications, and internal network utilities without the need for specialized software. It utilizes the SSL/TLS protocol for secure connections.
6. Limitations of Meraki VPN
Meraki’s VPN product line designed for small branch offices has certain limitations. It supports VPN throughput of 100-200 Mbps depending on the model and recommends a maximum of 50 client devices connecting through these appliances.
7. How Meraki Network Works
In a Meraki network, the cloud infrastructure takes the role of the initiator, allowing configurations to be executed in the cloud before the devices are online or physically deployed. Meraki hardware devices act as the server/receiver, receiving calls from the cloud for data collection and configuration deployment.
8. DHCP or Static IP
Cisco Meraki Access Points can either be configured with dynamic (DHCP) or static IP addresses to connect to a network. DHCP is recommended, but you can configure a static IP address either from the Dashboard or locally on the device.
9. IPsec vs. VPN
While many VPNs use the IPsec protocol suite to establish encrypted connections, not all VPNs rely on IPsec. SSL/TLS is an alternative protocol for VPNs that operates on a different layer of the OSI model.
10. Meraki VPN and IKEv2
Meraki supports both IKEv1 and IKEv2 for the IPsec tunnels it creates.
11. Meraki Authentication
Meraki supports MAC-based Access Control for authentication, where the RADIUS server admits or denies devices based on MAC addresses. This method requires no client-side configuration.
Choosing between IKEv2 and OpenVPN
When deciding between IKEv2 and OpenVPN, it depends on the specific requirements. OpenVPN is considered secure, versatile, and cost-efficient, whereas IKEv2 offers faster speeds and better mobile support.
Is IKEv2 the same as IPsec?
IKEv2 is a tunneling protocol that establishes a secure VPN communication between devices and defines negotiation and authentication processes for IPsec security associations (SAs). While IKEv2 is based on IPsec, they are not the same entity.
Conclusion
In conclusion, Meraki VPN offers robust and secure VPN functionalities, utilizing IPsec as the underlying protocol. With its easy-to-use interface and various authentication methods, it provides a seamless VPN experience for users. Understanding the differences between VPN protocols like IKEv2 and SSL/TLS can help in making informed decisions when choosing a VPN service.
Questions and Answers
1. What type of VPN does Meraki use?
Meraki uses IPsec as the underlying protocol for its VPN. It establishes secure tunnels using the password authentication protocol (PAP) and strong encryption.
2. Does Meraki have VPN capabilities?
Yes, Meraki offers VPN capabilities through its proprietary technology called Auto VPN. It simplifies the process of creating VPN tunnels between Meraki MX devices at separate network branches.
3. What authentication method does Meraki VPN use?
Meraki VPN supports various authentication methods, including mobile token authentication, SMS-based authentication, SMS with a link, and email-based authentication using OTP over email.
4. What type of VPN is IKEv2?
IKEv2 VPN is a widely used VPN protocol that combines the IKEv2 key management protocol and the IPsec protocol. It provides secure tunneling and data transportation between devices and VPN servers.
5. What type of VPN is SSL VPN?
SSL VPNs utilize the SSL/TLS protocol to establish secure connections, enabling users to access an organization’s network and applications without specialized software.
6. What are the limitations of Meraki VPN?
Meraki VPN’s product line designed for small branch offices has limitations in terms of VPN throughput and the number of client devices that can connect through the appliances. It is recommended to check the specifications of the specific model being used.
7. How does a Meraki network work?
In a Meraki network, the cloud infrastructure takes the initiative in calling Meraki hardware devices for data collection and configuration deployment. The devices act as server/receiver components in this process.
8. Does Meraki use DHCP or static IP?
Meraki Access Points can be configured with either dynamic (DHCP) or static IP addresses. DHCP is recommended, but it is possible to configure static IPs from the Dashboard or locally on the device.
9. Is IPsec the same as VPN?
No, IPsec is a protocol suite utilized by many VPNs to establish encrypted connections. However, there are other VPN protocols, such as SSL/TLS, which operate differently.
10. Does Meraki VPN support IKEv2?
Yes, Meraki supports both IKEv1 and IKEv2 for the IPsec tunnels it establishes.
11. How does Meraki authentication work?
Meraki provides MAC-based access control, where devices are admitted or denied based on their MAC addresses. This authentication method does not require any client-side configuration.
12. Should I use IKEv2 or OpenVPN?
The choice between IKEv2 and OpenVPN depends on the specific requirements. OpenVPN is versatile, secure, and cost-efficient, while IKEv2 provides faster speeds and better mobile support.
13. Is IKEv2 the same as IPsec?
IKEv2 is a tunneling protocol based on IPsec. While IKEv2 relies on IPsec, they are not the same entity. IKEv2 defines negotiation and authentication processes for IPsec security associations (SAs).
What type of VPN is Meraki
Meraki client VPN uses the password authentication protocol (PAP) to transmit and authenticate credentials. PAP authentication is always transmitted inside an IPsec tunnel between the client device and the MX security appliance using strong encryption.
Does Meraki have VPN
Overview. Auto VPN is a proprietary technology developed by Meraki that allows you to quickly and easily build VPN tunnels between Meraki MX devices at your separate network branches with just a few clicks. Auto VPN performs the work normally required for manual VPN configurations with a simple cloud based process.
Does Meraki use IPsec
This allows Cisco Meraki devices to establish all information needed to create an IPSec tunnel through this mutually trusted source. A method known as UDP holepunching is then used to create these VPN tunnels.
What authentication method does Meraki VPN use
What are different 2FA/MFA methods for Cisco Meraki Client VPN supported by miniOrange
| Authentication Type | Method |
|---|---|
| Mobile Token | Authy Authenticator |
| SMS | OTP Over SMS |
| SMS with Link | |
| OTP Over Email |
What type of VPN is IKEv2
IKEv2 VPN is a shorthand for an IKEv2/IPsec VPN protocol one of the most popular in the world. It's a combination of an IKEv2 key management protocol (helps your device and a VPN server recognize each other) and an IPsec protocol (provides security when tunneling and transporting data).
What type of VPN is SSL VPN
SSL VPN Explained
A secure sockets layer VPN (SSL VPN) enables individual users to access an organization's network, client-server applications, and internal network utilities and directories without the need for specialized software.
What are the limitations of Meraki VPN
Meraki's product line designed for small branch offices is limited to 100 – 200 Mbps of VPN throughput, depending on the model, and Meraki recommends no more than 50 client devices connecting through these appliances.
How does a Meraki network work
Meraki hardware devices act as the server/receiver as the Meraki cloud initiates calls to the devices for data collection and configuration deployment. The cloud infrastructure is the initiator, so configurations can be executed in the cloud before the devices are actually online or even physically deployed.
Does Meraki use DHCP or static
Cisco Meraki Access Points can use either dynamic (DHCP) or static IP configuration to connect to a network. Although DHCP is recommended, you may configure a static IP address on a Cisco Meraki AP either from the Dashboard or locally on the device.
Is IPsec the same as VPN
Many VPNs use the IPsec protocol suite to establish and run these encrypted connections. However, not all VPNs use IPsec. Another protocol for VPNs is SSL/TLS, which operates at a different layer in the OSI model than IPsec.
Does Meraki VPN support IKEv2
Meraki supports IKEv1 and IKEv2 for the IPsec tunnels.
How does Meraki authentication work
MAC-based Access Control
The RADIUS server can admit or deny the device based on the MAC address, responding to the Meraki AP with either an Access-Accept message or an Access-Reject message, respectively. This authentication method requires no client-side configuration.
Should I use IKEv2 or OpenVPN
It is open-source, secure, reliable, and cost-efficient. Summing up, if you need a secure and versatile protocol, OpenVPN is a good choice. However, if you care about speed or want to use a mobile VPN client, go for IKEv2.
Is IKEv2 the same as IPsec
Internet Key Exchange version 2 (IKEv2) is a tunneling protocol, based on IPsec, that establishes a secure VPN communication between VPN devices and defines negotiation and authentication processes for IPsec security associations (SAs).
Does VPN use IPsec or SSL
VPN protocols that use IPSec encryption include L2TP, IKEv2, and SSTP. OpenVPN is the most popular protocol that uses SSL encryption, specifically the OpenSSL library. SSL is used in some browser-based VPNs as well.
Is VPN based on IPsec or SSL
IPsec and SSL/TLS function at different layers of the OSI model, but both can be used for VPNs.
What are the disadvantages of Cisco Meraki
If your organization is considering Cisco Meraki for your IT network, keep these two disadvantages in mind:No Patch Management Features. As stated above, Cisco Meraki does not require additional maintenance.Cost Is Expensive For Small Businesses.
Why you shouldn’t use VPN all the time
Why shouldn't I use a VPN A VPN might reduce your connection speed even if your internet service provider isn't throttling your speed; Using a VPN on mobile will increase your mobile data usage; Using a VPN is considered an offense in some countries, and you can get fined or even be incarcerated for it.
Is Meraki a router or firewall
Each Meraki Go Router Firewall comes with 5 ports, and the GX20 Router Firewall includes 1 Power over Ethernet port. You can use these ports to plug in other network devices, such as a Meraki Go GS Switch, or Meraki Go GR Access Point, or plug clients directly in, such as a desktop or POS terminal.
How is Meraki different from Cisco
An Overview of Cisco and Meraki Switches
The Meraki Cloud Platform allows for easy deployment, hardware configuration, and network management. Cisco has many more families and models, whereas Meraki has fewer product options. There are more customization options when configuring Cisco switches.
Does Meraki do DHCP
Wireless clients that connect to the network will be given the following configuration via Meraki DHCP: An IP address in the 10.0. 0.0/8 range. The IP address is created by running the client's MAC address through a hashing algorithm.
How does DHCP work in Meraki
Run a DHCP server – The MX/MS will use its internal DHCP server to provide addressing and other information to clients. If selected, the other options below will become available. Relay DHCP to another server – The MX/MS will forward DHCP messages to a server on a different VLAN or over the site-to-site VPN.
Should I use IPsec or SSL VPN
Once a user is logged into the network, SSL takes the upper hand in security. SSL VPNs work by accessing specific applications whereas IPsec users are treated as full members of the network. It's therefore easier to restrict user access with SSL.
Should I use IKEv2 or IPsec
IPSec is considered secure and reliable, while IKEv2 is extremely fast and stable – IKEV2 offers quick re-connections when switching networks or during sudden drops. Thus, a combination of IKEv2/IPsec forms one of the best VPN protocols that exhibits the advantages of the two.
Does Meraki support SSL VPN
Overview. The Meraki Client VPN RADIUS instructions support push, phone call, or passcode authentication for desktop and mobile client connections that use SSL encryption.