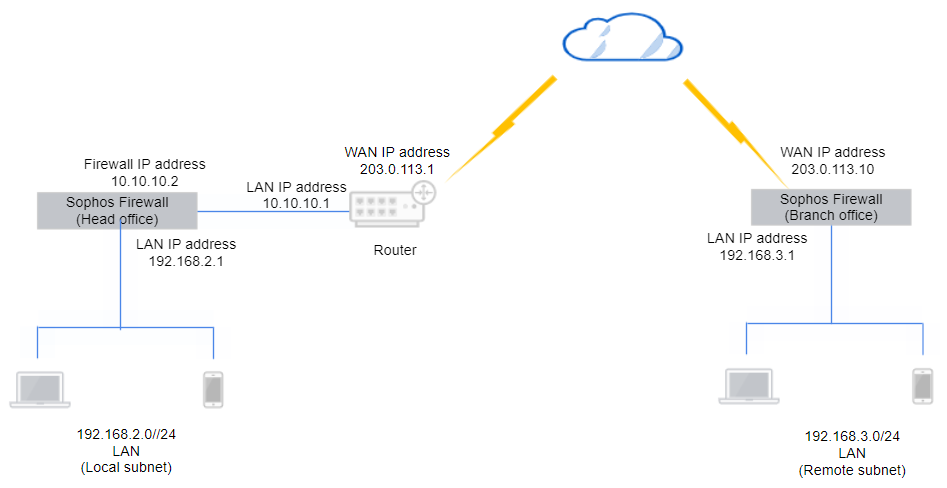
What ports are required for site-to-site VPN?
Summary
Contents
- 1 Summary
- 2 Personal Experience
- 3 Key Points
- 4 1. What ports are required for L2TP?
- 5 2. What ports need to be open for IPSec?
- 6 3. What is UDP port 4500 used for?
- 7 4. Does IPSec use TCP or UDP?
- 8 5. What protocol does L2TP use?
- 9 6. How do I connect to L2TP VPN?
- 10 7. What are the 3 main protocols that IPsec uses?
- 11 8. Which VPN protocol is best for IPsec?
- 12 9. Is IPSec port 500 or 4500?
- 13 10. What is UDP port 1521 used for?
- 14 11. What are the 3 protocols used in IPSec?
- 15 Questions and Answers
- 15.1 1. What ports are required for site-to-site VPN?
- 15.2 2. What ports are required for L2TP?
- 15.3 3. What ports need to be open for IPSec?
- 15.4 4. What is UDP port 4500 used for?
- 15.5 5. Does IPSec use TCP or UDP?
- 15.6 6. What protocol does L2TP use?
- 15.7 7. How do I connect to L2TP VPN?
- 15.8 8. What are the 3 main protocols that IPsec uses?
- 15.9 9. Which VPN protocol is best for IPsec?
- 15.10 10. Is IPSec port 500 or 4500?
- 15.11 11. What is UDP port 1521 used for?
- 15.12 12. What are the 3 protocols used in IPSec?
- 15.13 13. Is L2TP a layer 2 or 3?
- 15.14 14. Is L2TP a SSL VPN?
- 15.15 15. How to setup L2TP over IPsec?
Personal Experience
When it comes to setting up a VPN, one of the most common questions is about the ports that are required for different protocols. In my experience, understanding these ports is crucial for ensuring a smooth and secure VPN connection. In this article, I will share my knowledge on the ports required for L2TP and IPSec, as well as other related questions that often arise.
Key Points
1. What ports are required for L2TP?
L2TP uses IPSec, which requires UDP ports 500 and 4500, and ESP IP Protocol 50. However, if you disable IPSec, L2TP only requires UDP port 1701. Most environments allow this type of L2TP configuration unless there are strict network restrictions.
2. What ports need to be open for IPSec?
For L2TP/IPSec VPN connections, you need to open UDP port 500 for Internet Key Exchange (IKE) traffic, UDP port 4500 for IPsec control path, and UDP port 1701 for L2TP traffic. Additionally, IPsec ESP traffic uses IP protocol 50. It’s important to note that PPTP does not use Port 47, but rather Protocol 47 for GRE.
3. What is UDP port 4500 used for?
UDP port 4500 is used for NAT Traversal traffic in IPSec. When NAT addresses are available, it is possible to use NAT for both ends or only one end and set up the VPN with hide NAT behind the gateway.
4. Does IPSec use TCP or UDP?
IPSec uses UDP as its transport protocol for encrypted traffic. Regular IP traffic typically uses TCP, but IPsec traffic differentiates by using UDP for enhanced security.
5. What protocol does L2TP use?
L2TP is a variation of IP encapsulated protocol. It creates an L2TP tunnel by encapsulating an L2TP frame inside a UDP packet, which is then encapsulated inside an IP packet. The source and destination addresses of this IP packet define the endpoints of the connection.
6. How do I connect to L2TP VPN?
To connect to an L2TP VPN, you need to configure the L2TP connection on your device. In Windows 10, you can do this from the Settings menu. Click on Network & Internet, select VPN, and then add a VPN connection. Choose Windows (built-in) as the VPN provider and fill in the necessary details.
7. What are the 3 main protocols that IPsec uses?
The three main protocols of IPsec are Authentication Header (AH), Encapsulating Security Payload (ESP), and Internet Key Exchange (IKE). These protocols ensure the security and authentication of the IPsec VPN connection.
8. Which VPN protocol is best for IPsec?
IKEv2/IPsec is considered the most stable VPN protocol for mobile devices. It provides a strong connection and allows users to switch between networks without compromising security. Additionally, it can bypass firewalls and restrictions.
9. Is IPSec port 500 or 4500?
IPSec VPN communicates over IP protocol 50 (Encapsulating Security Payload – ESP). It can also require UDP port 500 for Internet Key Exchange (IKE) to manage encryption keys and UDP port 4500 for IPSec NAT-Traversal (NAT-T).
10. What is UDP port 1521 used for?
UDP port 1521 is the default client connection port for Oracle databases. While the default SSL port for secured Oracle client connections is not 1521, you can configure another TCP port using the Oracle configuration and administration tools.
11. What are the 3 protocols used in IPSec?
IPSec relies on three main protocols: Authentication Header (AH), Encapsulating Security Payload (ESP), and Internet Key Exchange (IKE). These protocols work together to establish and maintain a secure connection.
Questions and Answers
1. What ports are required for site-to-site VPN?
2. What ports are required for L2TP?
3. What ports need to be open for IPSec?
By default, L2TP uses IPSec, which requires UDP ports 500 and 4500, and ESP IP Protocol 50. If you disable IPSec, Mobile VPN with L2TP requires only UDP port 1701. This type of L2TP configuration should be allowed in most environments unless the network is configured to be extremely restrictive.
4. What is UDP port 4500 used for?
As port 4500 is used for NAT Traversal traffic, you can either use NAT for both ends or set up VPN on only one end by using hide NAT behind the gateway.
5. Does IPSec use TCP or UDP?
UDP
6. What protocol does L2TP use?
L2TP is a variation of an IP encapsulation protocol. The L2TP tunnel is created by encapsulating an L2TP frame inside a User Datagram Protocol (UDP) packet, which in turn is encapsulated inside an IP packet. The source and destination addresses of this IP packet define the endpoints of the connection.
7. How do I connect to L2TP VPN?
Configure the L2TP Connection by navigating to the VPN settings in Windows 10. Select the L2TP over IPSec Client Scenario, configure the VPN details, and save the configuration.
8. What are the 3 main protocols that IPsec uses?
The three main protocols comprising IPsec are: Authentication Header (AH), Encapsulating Security Payload (ESP), and Internet Key Exchange (IKE).
9. Which VPN protocol is best for IPsec?
IKEv2/IPsec provides a strong connection over mobile devices and allows users to switch between networks without risking their security. This makes it the most stable VPN protocol for mobile devices. Bypassing firewalls and restrictions.
10. Is IPSec port 500 or 4500?
IPSec VPN is a layer 3 protocol that communicates over IP protocol 50, Encapsulating Security Payload (ESP). It might also require UDP port 500 for Internet Key Exchange (IKE) to manage encryption keys, and UDP port 4500 for IPSec NAT-Traversal (NAT-T).
11. What is UDP port 1521 used for?
Port 1521 is the default client connections port, however, you can configure another TCP port via the Oracle configuration and administration tools. The default SSL port for secured Oracle client connections to the database via the Oracle’s SQL*Net protocol. Open this port if you need secure connection.
12. What are the 3 protocols used in IPSec?
Some IPSec protocols are given below. Authentication header (AH), Encapsulating security payload (ESP), Internet key exchange (IKE)
13. Is L2TP a layer 2 or 3?
L2TP offers layer 2 tunneling between networks and devices. It has many uses as a bridge between LANs, while L2TP is also a popular component of Virtual Private Network services when paired with IPSec.
14. Is L2TP a SSL VPN?
Unlike other tunneling security protocols, such as Layer 2 Tunneling Protocol (L2TP) or IP security (IPsec), SSL VPNs only require an updated browser to establish a secure network.
15. How to setup L2TP over IPsec?
Configure L2TP VPN using the built-in wizard. Navigate to the wizard, select the L2TP over IPSec Client Scenario, configure the VPN, and save the configuration.
What ports are required for L2TP
By default, L2TP uses IPSec, which requires UDP ports 500 and 4500, and ESP IP Protocol 50. If you disable IPSec, Mobile VPN with L2TP requires only UDP port 1701. This type of L2TP configuration should be allowed in most environments unless the network is configured to be extremely restrictive.
What ports need to be open for IPSec
For L2TP/IPSEC VPN connections, you need to open UDP port 500 for Internet Key Exchange (IKE) traffic, UDP port 4500 (IPsec control path) and UDP port 1701 for L2TP traffic. IPsec ESP traffic also uses IP protocol 50. PPTP does not use Port 47, but Protocol 47 for GRE. Not the same thing.
Cached
What is UDP port 4500 used for
As port 4500 is used for NAT Traversal traffic you can do 2 things, when you have NAT addresses available you can use NAT for both ends or just one end and only have 1 end setup the VPN, for that one use hide NAT behind the gateway.
Does IPSec use TCP or UDP
UDP
Transmission: Encrypted IPsec packets travel across one or more networks to their destination using a transport protocol. At this stage, IPsec traffic differs from regular IP traffic in that it most often uses UDP as its transport protocol, rather than TCP.
What protocol does L2TP use
L2TP is actually a variation of an IP encapsulation protocol. The L2TP tunnel is created by encapsulating an L2TP frame inside a User Datagram Protocol (UDP) packet, which in turn is encapsulated inside an IP packet. The source and destination addresses of this IP packet define the endpoints of the connection.
How do I connect to L2TP VPN
Configure the L2TP ConnectionFrom the Windows 10 Start Menu, click Settings.Click Network & Internet.On the left navigation menu, select VPN.Click Add a VPN connection.In the VPN provider text box, select Windows (built-in).In the Connection name text box, type a name for the Mobile VPN (such as "L2TP VPN")
What are the 3 main protocols that IPsec uses
The three main protocols comprising IPsec are: Authentication Header (AH), Encapsulating Security Payload (ESP), and Internet Key Exchange (IKE).
Which VPN protocol is best for IPsec
IKEv2/IPsec provides a strong connection over mobile devices and allows users to switch between networks without risking their security. This makes it the most stable VPN protocol for mobile devices. Bypassing firewalls and restrictions.
Is IPSec port 500 or 4500
IPSec VPN is a layer 3 protocol that communicates over IP protocol 50, Encapsulating Security Payload (ESP). It might also require UDP port 500 for Internet Key Exchange (IKE) to manage encryption keys, and UDP port 4500 for IPSec NAT-Traversal (NAT-T).
What is UDP port 1521 used for
Port 1521 is the default client connections port, however, you can configure another TCP port via the Oracle configuration and administration tools. The default SSL port for secured Oracle client connections to the database via the Oracle's SQL*Net protocol. Open this port if you need secure connection.
What are the 3 protocols used in IPSec
Some IPSec protocols are given below.Authentication header (AH)Encapsulating security payload (ESP)Internet key exchange (IKE)
Is L2TP a layer 2 or 3
L2TP offers layer 2 tunneling between networks and devices. It has many uses as a bridge between LANs, while L2TP is also a popular component of Virtual Private Network services when paired with IPSec.
Is L2TP a SSL VPN
Unlike other tunneling security protocols, such as Layer 2 Tunneling Protocol (L2TP) or IP security (IPsec), SSL VPNs only require an updated browser to establish a secure network.
How to setup L2TP over IPsec
1. Configure L2TP VPN using built-in Wizard1.1 Navigate to the Wizard. a.1.2 Select the L2TP over IPSec Client Scenario.1.3 Configure VPN Configuration. Enter a preferred Pre-Shared Key and select the corresponding WAN interface.1.4 Configure User Authentication.1.5 Save the Configuration & Download L2TP Configuration.
What is VPN protocol L2TP
The Layer 2 Tunneling Protocol (L2TP) is a virtual private network (VPN) protocol that creates a connection between your device and a VPN server without encrypting your content. Due to its lack of encryption and authentication, L2TP is usually paired with Internet Protocol Security (IPsec) protocol.
What VPN protocol uses IPsec
IPsec VPN uses the Internet Key Exchange (IKE) protocol for key management and authentication. IKE uses the Diffie-Hellman algorithm to generate a shared secret key that is used to encrypt traffic between two hosts. SSL VPN uses Transport Layer Security (TLS) to encrypt traffic.
What are the 3 protocols used in IPsec
Some IPSec protocols are given below.Authentication header (AH)Encapsulating security payload (ESP)Internet key exchange (IKE)
What is port 500 for VPN
Description: Port 500 is used by the Internet key exchange (IKE) that occurs during the establishment of secure VPN tunnels. Users of VPN servers and clients may encounter this port.
What is the TCP port for IPSec
IPSec over TCP – This method tunnels both the IKE negotiation and IPSec data traffic within a pre-defined TCP port. The default port for this traffic is 10000/tcp.
Why do we use UDP port 4500 instead of UDP 500
It might also require UDP port 500 for Internet Key Exchange (IKE) to manage encryption keys, and UDP port 4500 for IPSec NAT-Traversal (NAT-T). Sometimes, if the UDP ports are blocked, VPN devices try to use TCP port 500 and TCP port 4500.
What is UDP port 143 used for
An IMAP server typically listens on port number 143. IMAP over SSL/TLS (IMAPS) is assigned the port number 993. Virtually all modern e-mail clients and servers support IMAP, which along with the earlier POP3 (Post Office Protocol) are the two most prevalent standard protocols for email retrieval.
What are the 2 main protocols used by IPSec
IPsec originally defined two protocols for securing IP packets: Authentication Header (AH) and Encapsulating Security Payload (ESP). The former provides data integrity and anti-replay services, and the latter encrypts and authenticates data.
Which VPN protocol is best for IPSec
IKEv2/IPsec provides a strong connection over mobile devices and allows users to switch between networks without risking their security. This makes it the most stable VPN protocol for mobile devices. Bypassing firewalls and restrictions.
Is L2TP same as IPsec
L2TP is a networking protocol used by the ISPs to enable VPN operations. IPsec. IPsec is a protocol suite for secure IP communications that authenticates and encrypts each IP packet in a communication session. for clients using pre-shared keys, certificates, or EAP.
Is SSL VPN port TCP or UDP
The HTTP, HTTPS, SMTP, POP3 and Microsoft Exchange protocols all use TCP by default. If the majority of the traffic generated by your Mobile VPN with SSL clients is UDP, we recommend that you select TCP as the protocol for the Mobile VPN with SSL.