What is the difference between ZTNA and firewall?
Summary
Contents
- 1 Summary
- 2 Does Zero Trust Use Firewalls?
- 3 What Are the Three Types of Firewalls?
- 4 What Is the Purpose of ZTNA?
- 5 What Is the Difference Between ZTNA and WAF?
- 6 What Is Zero Day Protection in Firewall?
- 7 What Is the Best No Root Firewall?
- 8 What Are the Four Major Types of Firewalls?
- 9 What Are the Two Main Types of Firewalls?
- 10 What Are Two Functions of ZTNA?
- 11 How Is ZTNA Better Than VPN?
- 12 Do I Need a Firewall If I Have a WAF?
- 13 Does a WAF Replace a Firewall?
- 14 Is Zero-Day a Threat or Vulnerability?
In this article, I will discuss the difference between Zero Trust Network Access (ZTNA) and firewalls, as well as answer questions related to firewalls and ZTNA.
Does Zero Trust Use Firewalls?
At the edge of a microperimeter, a Zero Trust network employs a segmentation gateway that monitors the entry of people and data. It applies security measures designed to thoroughly vet users and data before granting access, using a Layer 7 firewall and the Kipling method.
What Are the Three Types of Firewalls?
The three main types of firewalls, namely packet-filtering, stateful inspection, and proxy, offer progressively more advanced protection levels. However, firewalls don’t inspect application-level traffic, which can lead to blocking safe traffic or websites such as YouTube under certain circumstances.
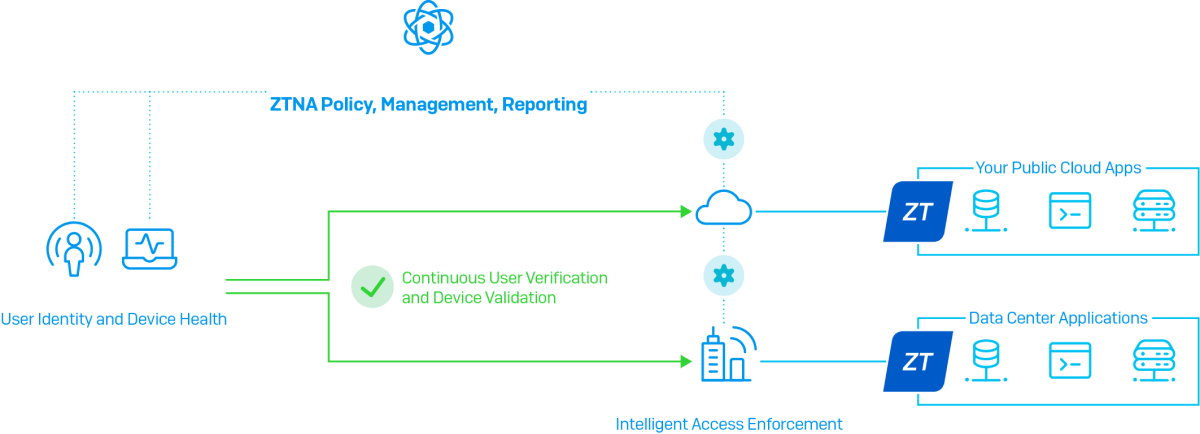
What Is the Purpose of ZTNA?
The primary use for ZTNA is to provide a highly granular access mechanism based on a user’s identity. Where IP-based VPN access offers broad access to a network once authorized, ZTNA offers limited, granular access to specific applications and resources.
What Is the Difference Between ZTNA and WAF?
Web Application Firewalls (WAFs) are designed to protect and secure public-facing applications by providing firewall, threat detection, and other hardening like SQL injection attack defenses. On the other hand, ZTNA is designed to control access by staff to internal applications.
What Is Zero Day Protection in Firewall?
Zero-day protection refers to blocking unknown threats that pose critical risks to businesses and are the hardest to prevent. Many businesses rely on Security Operations Center (SOC) teams to detect and respond to these threats after they breach their systems.
What Is the Best No Root Firewall?
For Android devices, firewalls like NetGuard and NoRoot Firewall are great options for users who do not want to root their devices. For more advanced users, AFWall+, Mobiwol, and Firewalla offer additional features.
What Are the Four Major Types of Firewalls?
The five types of firewalls include packet filtering firewalls, circuit-level gateways, application-level gateways (proxy firewalls), stateful inspection firewalls, and next-generation firewalls (NGFW).
What Are the Two Main Types of Firewalls?
The two main types of firewalls are network firewalls, deployed at the network boundary, and host-based firewalls, installed on individual computers or servers. Both types play a crucial role in protecting networks and systems from unauthorized access and malicious activities.
What Are Two Functions of ZTNA?
ZTNA serves to reduce third-party risk by giving contractors, vendors, and other third parties access to specific internal applications without providing broader access. Additionally, ZTNA can hide sensitive applications, making them “invisible” to unauthorized users and devices, thus reducing insider threats.
How Is ZTNA Better Than VPN?
Compared to VPNs, ZTNA offers lower latency and improved performance. Unlike VPNs that require routing all traffic through a centralized gateway or server, ZTNA uses distributed gateways closer to the user and the resources they are accessing.
Do I Need a Firewall If I Have a WAF?
While a Web Application Firewall (WAF) provides protection against web application vulnerabilities, it cannot protect from attacks at the network layer. Therefore, a WAF should supplement a network firewall rather than replace it.
Does a WAF Replace a Firewall?
A Web Application Firewall (WAF) does not replace traditional network layer firewalls. Instead, it complements network firewalls by providing additional protection at the application layer (Layer 7) of the OSI model. WAFs intercept HTTP data but cannot monitor and filter data protocols used at lower levels.
Is Zero-Day a Threat or Vulnerability?
A zero-day exploit, also known as a zero-day threat, is an attack that takes advantage of a security vulnerability that does not have a fix or patch in place.
Does zero trust use firewalls
At the edge of a microperimeter, a zero trust network employs a segmentation gateway, which monitors the entry of people and data. It applies security measures that are designed to thoroughly vet users and data before to granting access using a Layer 7 firewall and the Kipling method.
What are the 3 types of firewalls
The three main types of firewalls (packet-filtering, stateful inspection, and proxy) offer progressively more advanced protection levels. Firewalls don't inspect application-level traffic, which can lead to blocking safe traffic or websites such as YouTube under certain circumstances.
What is the purpose of ZTNA
Authentication and Access – The primary use for ZTNA is to provide a highly granular access mechanism based on a user's identity. Where IP-based VPN access offers broad access to a network once authorized, ZTNA offers limited, granular access to specific applications and resources.
What is the difference between ZTNA and WAF
WAF is designed to protect and secure public-facing applications by providing firewall, threat detection, and other hardening like SQL injection attack defenses. ZTNA is designed to control access by staff to internal applications.
What is zero day protection in firewall
Zero-Day Protection: Block Unknown Threats. Attacks from unknown threats pose critical risks to businesses and are the hardest to prevent. This is why many businesses rely on SOC teams to detect them after breaching their systems.
What is the best no root firewall
In conclusion, a firewall is essential for protecting your Android device from cyber threats. NetGuard and NoRoot Firewall are great options for users who do not want to root their devices, while AFWall+, Mobiwol, and Firewalla offer more advanced features for advanced users.
What are the 4 major types of firewalls
Five types of firewall include the following:packet filtering firewall.circuit-level gateway.application-level gateway (aka proxy firewall)stateful inspection firewall.next-generation firewall (NGFW)
What are the two main types of firewall
The two main types of firewalls are network firewalls, which are deployed at the network boundary, and host-based firewalls, which are installed on individual computers or servers. Both types play a crucial role in protecting networks and systems from unauthorized access and malicious activities.
What are two functions of ZTNA
Reduce third-party risk – Give contractors, vendors, and other third parties access to specific internal applications — and no more. Hide Sensitive Applications – Render applications “invisible” to unauthorized users and devices. ZTNA can significantly reduce the risk posed by insider threats.
How is ZTNA better than VPN
When it comes to latency as well, ZTNA has an edge over VPN as it does not require all traffic to be routed through a centralized gateway or server. Instead, ZTNA uses distributed gateways that are closer to the user and the resources they are accessing. This reduces latency and improves performance.
Do I need a firewall if I have a WAF
Choosing an Application or Network Firewall
So without an application firewall, businesses could leave their broader network open to attack through web application vulnerabilities. However, a WAF cannot protect from attacks at the network layer, so it should supplement a network firewall rather than replace it.
Does a WAF replace a firewall
WAFs complement network firewalls and provide additional protection but do not replace traditional network layer firewalls. A web application firewall works at the application layer, Layer 7 in the OSI model. It intercepts HTTP data but cannot monitor and filter data protocols used at lower levels.
Is zero-day a threat or vulnerability
A zero-day exploit (also called a zero-day threat) is an attack that takes advantage of a security vulnerability that does not have a fix in place.
What is the best protection against zero-day attacks
4 Best Practices for Protection Against Zero-Day AttacksUse Windows Defender Exploit Guard.Leverage Next-Generation Antivirus (NGAV)Implement Patch Management.Have an Incident Response Plan Ready.
What is the best firewall to put on your phone
6 Best Firewall Apps for AndroidNetGuard. Netguard is a free and open-source firewall app that you can use on either rooted or unrooted devices running Android Lollipop (or newer).Droid Firewall.No Root Firewall.VPN Safe Firewall.AFWall +Mobiwol: No Root Firewall.
Which device can bypass a firewall
VPN: A virtual private network (VPN) can help bypass firewalls and intrusion detection systems by routing traffic through a secure server. Proxy server: A proxy server can help mask the origin of the traffic, making it harder for the firewall or intrusion detection system to trace the source of an attack.
What are the 5 types of firewalls
There are five basic categories of firewalls:Packet Filtering Firewall.Circuit-Level Gateway.Application-Level Gateway (“proxy”)Stateful Inspection Firewall.Next-Generation Firewall (NGFW)Choosing the Right Firewall for You.Types of Firewalls.
What are the 3 main functions of a firewall
Overall, firewalls play an important role in preventing cyber attacks, protecting sensitive data, and maintaining the privacy and security of computer systems and networks.
What is the most common firewall
The most common firewall types based on methods of operation are: Packet-filtering firewalls. Proxy firewalls. NAT firewalls.
Which 2 traits are unique to ZTNA
Six Key Characteristics of a Modern ZTNA SolutionScalable Performance.Robust Data Loss Prevention (DLP)Advanced Threat Protection (ATP)Granular Visibility and Reporting.Part of a Comprehensive SASE Offering.
How will zero trust replace VPN
Replace VPN with Zero Trust Strategy
While VPN services do offer a level of connectivity, zero trust is specifically designed to meet modern needs for visibility and control as well as critical business demands such as remote work, speed, performance, security and more.
Should a WAF be in front or behind firewall
Ideally, you'll deploy a WAF behind your load balancing tier. This optimizes for utilization, performance, and reliability while providing the protection necessary for all apps – but particularly for those exposed on the Internet.
What is the firewall behind WAF
A web application firewall (WAF) is a type of firewall that protects web applications and APIs by filtering, monitoring and blocking malicious web traffic and application-layer attacks — such as DDoS, SQL injection, cookie manipulation, cross-site scripting (XSS), cross-site forgery and file inclusion.
Is Palo Alto firewall a WAF
Palo Alto Networks is one such vendor that offers a comprehensive and easy-to-use set of firewalls, including NGFWs and Web Application and API Security platform, which includes a built-in WAF.
What is firewall zero-day threats
Zero-day exploits refer to security vulnerabilities that are unknown to the software developer or security team. These types of vulnerabilities can be exploited by hackers to gain unauthorized access to an application, device, or network. As such, they represent a major risk for organizations and businesses.