What is the difference between IPsec and TLS tunnel?
Summary
Contents
- 1 Summary
- 2 Main Thought
- 3 Main Thought
- 4 Key Points
- 5 1. Main Thought
- 6 2. Main Thought
- 7 3. Main Thought
- 8 4. Main Thought
- 9 5. Main Thought
- 10 6. Main Thought
- 11 7. Main Thought
- 12 Questions and Answers
- 12.1 1. Question: Can TLS and IPsec be used together?
- 12.2 2. Question: Does VPN use IPsec or TLS?
- 12.3 3. Question: What is the difference between SSL tunnel and TLS tunnel?
- 12.4 4. Question: What is IPsec and TLS? Also, define their modes.
- 12.5 5. Question: What are the three main protocols that IPsec uses?
- 12.6 6. Question: Is IPsec a Layer 2 or Layer 3?
- 12.7 7. Question: Why is TLS better than IPsec?
- 12.8 8. Question: Is TLS considered a VPN?
- 12.9 9. Question: What is IPsec tunneling?
- 12.10 10. Question: Which are the two main types of VPN tunnels?
- 12.11 11. Question: What are the three protocols used in IPsec?
- 12.12 12. Question: What are the two types of IPsec?
- 12.13 13. Question: Is IPsec a Layer 3 or Layer 4?
- 12.14 14. Question: What layer does TLS operate at?
- 12.15 15. Question: What is the downside of TLS?
This article explores the differences between IPsec and TLS in terms of their usage, protocols, and benefits. It also addresses common questions related to the two technologies.
Main Thought
IPsec and TLS are both encryption protocols that provide confidentiality and integrity for communications.
Main Thought
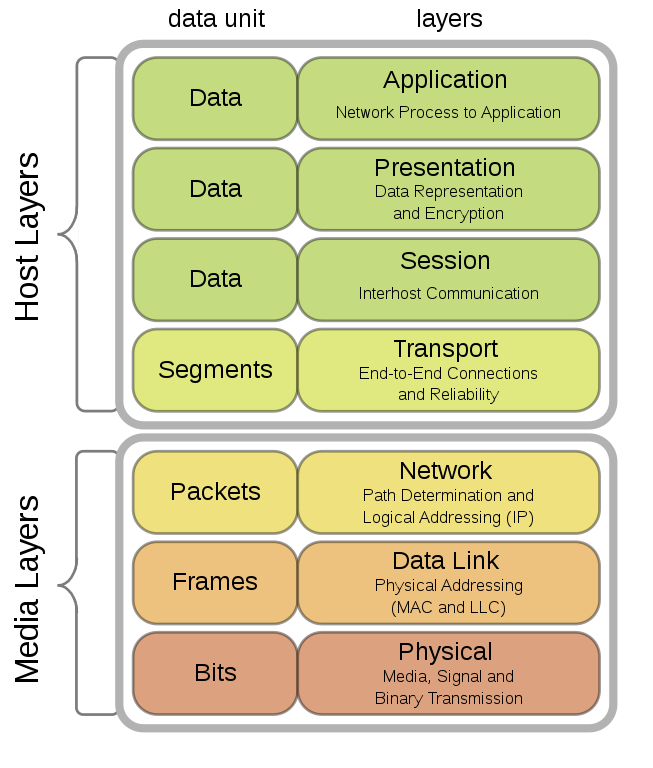
TLS operates at higher layers of the OSI model compared to IPsec, requiring each application and communication flow to establish its own TLS session.
Key Points
1. Main Thought
IPsec supports two operational modes: transport mode and tunnel mode.
2. Main Thought
TLS VPNs work seamlessly with most modern websites and add an additional cybersecurity barrier for web users.
3. Main Thought
IPsec is commonly used in VPNs to establish and run encrypted connections, but not all VPNs use IPsec.
4. Main Thought
TLS and IPsec can be used together, providing both confidentiality and integrity for communications.
5. Main Thought
IPsec is a group of protocols used together to set up secure connections between devices at layer 3 of the OSI model.
6. Main Thought
TLS operates at Layers 4 through 7 of the OSI model and requires each application and communication flow to establish its own TLS session.
7. Main Thought
TLS has higher latency compared to other secure encryption protocols.
Questions and Answers
1. Question: Can TLS and IPsec be used together?
2. Question: Does VPN use IPsec or TLS?
3. Question: What is the difference between SSL tunnel and TLS tunnel?
4. Question: What is IPsec and TLS? Also, define their modes.
5. Question: What are the three main protocols that IPsec uses?
6. Question: Is IPsec a Layer 2 or Layer 3?
7. Question: Why is TLS better than IPsec?
8. Question: Is TLS considered a VPN?
9. Question: What is IPsec tunneling?
10. Question: Which are the two main types of VPN tunnels?
11. Question: What are the three protocols used in IPsec?
12. Question: What are the two types of IPsec?
13. Question: Is IPsec a Layer 3 or Layer 4?
14. Question: What layer does TLS operate at?
15. Question: What is the downside of TLS?
Can TLS and IPsec be used together
Absolutely. In fact, I'm posting this answer using both IPSec (via VPN) and TLS (via HTTPS). As you noted, the technologies are similar as they both provide confidentiality and integrity on communications.
Does VPN use IPsec or TLS
Many VPNs use the IPsec protocol suite to establish and run these encrypted connections. However, not all VPNs use IPsec. Another protocol for VPNs is SSL/TLS, which operates at a different layer in the OSI model than IPsec.
What is the difference between SSL tunnel and TLS tunnel
SSL performs authentication and data encryption. The Transport Layer Security (TLS) tunnel encrypts all data sent over the TCP connection.
What is IPsec and TLS also define its modes
IPSec supports two operational modes: transport mode and tunnel mode. In transport mode, security protection is provided to traffic end to end, from one host to another. In tunnel mode, the protection typically is provided to traffic from the gateway of one network to the gateway of another network.
What are the 3 main protocols that IPsec uses
The three main protocols comprising IPsec are: Authentication Header (AH), Encapsulating Security Payload (ESP), and Internet Key Exchange (IKE).
Is IPsec a layer 2 or 3
IPsec helps keep private data secure when it is transmitted over a public network. More specifically, IPsec is a group of protocols that are used together to set up secure connections between devices at layer 3 of the OSI model (the network layer).
Why is TLS better than IPsec
If you really need per-user, per-application access control at the gateway, go SSL/TLS. If you need to give trusted user groups homogenous access to entire private network segments or need the highest level of security available with shared secret encryption, go IPsec.
Is TLS considered a VPN
TLS VPNs are usually clientless. There is no need for separate software to establish connections and control access. This style of VPN also works with HTTP, allowing it to work seamlessly with most modern websites. It functions in the background, adding another cybersecurity barrier for web users.
What is IPsec tunneling
An Internet Protocol Security (IPSec) tunnel is a set of standards and protocols originally developed by the Internet Engineering Task Force (IETF) to support secure communication as packets of information are transported from an IP address across network boundaries and vice versa.
Which are the two main types of VPN tunnels
Types of VPNsSite-to-Site VPN: A site-to-site VPN is designed to securely connect two geographically-distributed sites.Remote Access VPN: A remote access VPN is designed to link remote users securely to a corporate network.
What are the 3 protocols used in IPsec
Some IPSec protocols are given below.Authentication header (AH)Encapsulating security payload (ESP)Internet key exchange (IKE)
What are the two types of IPsec
The IPsec standards define two distinct modes of IPsec operation, transport mode and tunnel mode. The modes do not affect the encoding of packets. The packets are protected by AH, ESP, or both in each mode.
Is IPsec a layer 3 or 4
What is IPsec IPsec helps keep private data secure when it is transmitted over a public network. More specifically, IPsec is a group of protocols that are used together to set up secure connections between devices at layer 3 of the OSI model (the network layer).
What layer does TLS operate at
Because TLS operates at Layers 4 through 7 of the OSI model, as opposed to Layer 3, which is the case with IPsec, each application and each communication flow between client and server must establish its own TLS session to gain authentication and data encryption benefits.
What is the downside of TLS
TLS disadvantages:
Higher latency compared to other secure encryption protocols.
What are the three main benefits of TLS protocol
There are three main components to what the TLS protocol accomplishes: Encryption, Authentication, and Integrity. Encryption: hides the data being transferred from third parties.
Does TLS hide IP address
SSL/TLS doesn't hide the source and the destination IP addresses. It is impossible (at least, with a purely ssl/tls solution), because the src/dst addresses must be valid to a working tcp connection. The name of the connected website, is hidden by default – or, at least, it was until the last some years.
Does TLS encrypt IP
A primary use case of TLS is encrypting the communication between web applications and servers, such as web browsers loading a website. TLS can also be used to encrypt other communications such as email, messaging, and voice over IP (VoIP).
What are the two modes of IPsec
The IPsec standards define two distinct modes of IPsec operation, transport mode and tunnel mode. The modes do not affect the encoding of packets. The packets are protected by AH, ESP, or both in each mode.
What is the two tunneling protocol
Layer Two Tunneling Protocol (L2TP) is an extension of the Point-to-Point Tunneling Protocol (PPTP) used by internet service providers (ISPs) to enable virtual private networks (VPNs). To ensure security and privacy, L2TP must rely on an encryption protocol to pass within the tunnel.
Which tunneling protocol is most commonly used for VPN
Point-to-Point Protocol (PPP) is used to encrypt the data between the connection. PPTP is one of the most widely used VPN protocol and has been in use since the early release of Windows.
What are the 2 main protocols used by IPsec
IPsec originally defined two protocols for securing IP packets: Authentication Header (AH) and Encapsulating Security Payload (ESP). The former provides data integrity and anti-replay services, and the latter encrypts and authenticates data.
Is IPsec a layer 2 tunneling protocol
IPsec is often used to secure L2TP packets by providing confidentiality, authentication and integrity. The combination of these two protocols is generally known as L2TP/IPsec (discussed below). The two endpoints of an L2TP tunnel are called the L2TP access concentrator (LAC) and the L2TP network server (LNS).
What are the two main protocols of TLS
The TLS and SSL protocols can be divided into two layers. The first layer consists of the application protocol and the three handshaking protocols: the handshake protocol, the change cipher spec protocol, and the alert protocol. The second layer is the record protocol.
Is TLS layer 5 or 6
The original OSI 7-layer model did not consider security, so TLS is usually referred to as a layer 6.5 protocol. It is built on top of layer 4 TCP (layers 5 and 6 are obsolete), and it is used to provide secure communications to layer 7 applications.