What is needed for site to site VPN?
Summary
Contents
- 1 Summary
- 2 How do I implement a site to site VPN
- 3 Does site-to-site VPN require hardware
- 4 How does a site to site VPN work
- 5 What are the two types of site to site VPN
- 6 What are the requirements for IPSec
- 7 What is the difference between VPN and site-to-site VPN
- 8 What are the required components for a VPN to work
- 9 What three items are required to establish a VPN connection
- 10 What is the difference between VPN tunnel and site-to-site VPN
- 11 What is the difference between a VPN and a site-to-site connection
- 12 What are the 3 major components of IPSec
- 13 What are the 3 protocols used in IPSec
- 14 What is the advantage of site-to-site VPN
- 15 Is site-to-site VPN the same as virtual private gateway
This article discusses site-to-site VPNs and provides answers to common questions related to their implementation, requirements, and functionality.
How do I implement a site to site VPN
For more information on implementing a site-to-site VPN, see “Tunnel options for your Site-to-Site VPN connection.” The implementation involves creating a customer gateway, creating a target gateway, configuring routing, updating security groups, creating a VPN connection, and downloading the configuration file.
Does site-to-site VPN require hardware
Both site-to-site VPN and remote access VPN require additional hardware or software to be installed in order to establish the VPN connection.
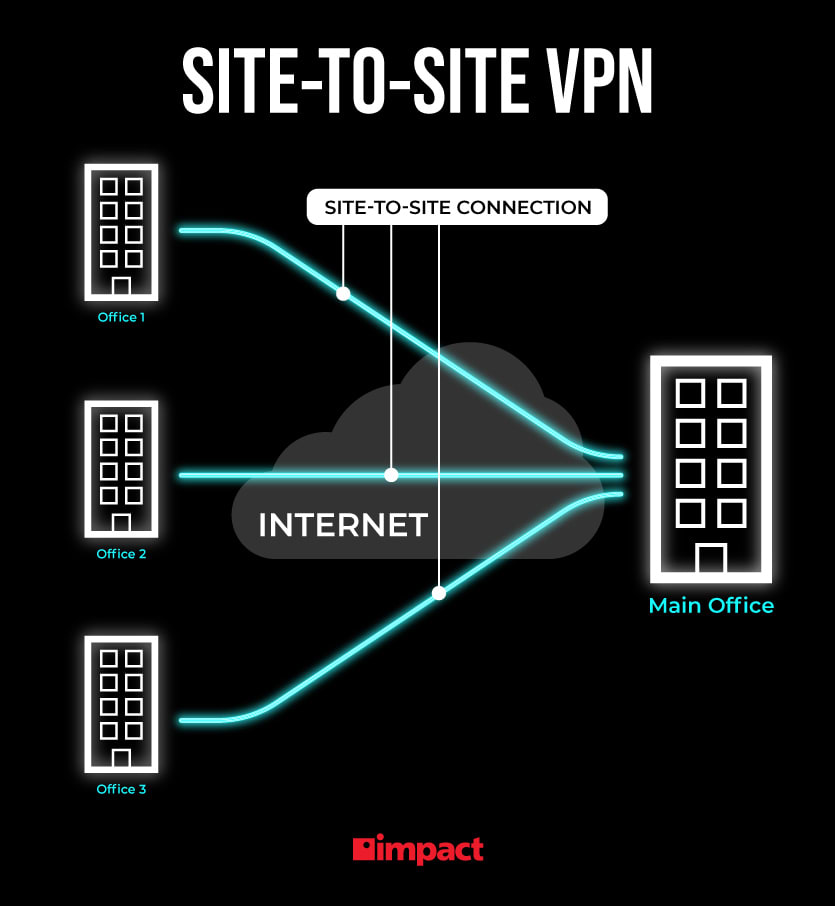
How does a site to site VPN work
A site-to-site VPN creates an encrypted link between VPN gateways located at different sites. The VPN tunnel encrypts traffic at one end, sends it over the public Internet to the other site, where it is decrypted and routed to its destination.
What are the two types of site to site VPN
There are two types of site-to-site VPNs: Intranet-based VPN and Extranet-based VPN. Intranet-based VPN connects multiple offices of the same company, while Extranet-based VPN connects a company’s office to another company’s office.
What are the requirements for IPSec
All IPsec VPN configurations require at least two items: the Internet Security Association and Key Management Protocol (ISAKMP) or Internet Key Exchange (IKE) policy, and the IPsec policy.
What is the difference between VPN and site-to-site VPN
There are two types of VPN connections: Client-to-Site (or Remote Access) and Site-to-Site (or Gateway-to-Gateway). The difference between them is that Client-to-Site VPN deals with single user connections, while Site-to-Site VPNs establish remote connections between entire networks.
What are the required components for a VPN to work
A VPN uses three basic components to work: the tunnel, the encryption, and the server. These components ensure secure and private connections between devices and websites/services over the internet.
What three items are required to establish a VPN connection
To establish a VPN connection, you will need a VPN client, a VPN server, and a VPN router. The client connects you to servers around the world, allowing access to your small business network from anywhere, even when using public Wi-Fi networks.
What is the difference between VPN tunnel and site-to-site VPN
While a site-to-site VPN provides security through encryption between two points, the VPN tunnel itself doesn’t offer additional security features like access control or content regulation.
What is the difference between a VPN and a site-to-site connection
A remote access VPN involves a client/server model, while a site-to-site VPN connects two internet gateways and doesn’t require users to install software.
What are the 3 major components of IPSec
The three major components of IPSec are the Authentication Header (AH), Encapsulating Security Payload (ESP), and Internet Key Exchange (IKE).
What are the 3 protocols used in IPSec
The three protocols used in IPSec are the Authentication Header (AH), Encapsulating Security Payload (ESP), and Internet Key Exchange (IKE).
What is the advantage of site-to-site VPN
The main advantage of a site-to-site VPN is its security. IPsec protocols ensure that all traffic is encrypted in transit through the VPN tunnel, preventing interception from external sources.
Is site-to-site VPN the same as virtual private gateway
No, a virtual private gateway is the VPN concentrator on the Amazon side of the Site
How do I implement a site to site VPN
For more information, see Tunnel options for your Site-to-Site VPN connection.Step 1: Create a customer gateway.Step 2: Create a target gateway.Step 3: Configure routing.Step 4: Update your security group.Step 5: Create a VPN connection.Step 6: Download the configuration file.
Does site to site VPN require hardware
Both site-to-site VPN and remote access VPN require additional hardware or software to be installed to establish the VPN connection.
How does a site to site VPN work
A site-to-site Virtual Private Network (VPN) provides this by creating an encrypted link between VPN gateways located at each of these sites. A site-to-site VPN tunnel encrypts traffic at one end and sends it to the other site over the public Internet where it is decrypted and routed on to its destination.
What are the two types of site to site VPN
2. Site to Site VPNIntranet based VPN: When several offices of the same company are connected using Site-to-Site VPN type, it is called as Intranet based VPN.Extranet based VPN: When companies use Site-to-site VPN type to connect to the office of another company, it is called as Extranet based VPN.
What are the requirements for IPSec
All IPsec VPN configurations require at least two items: (1) the Internet Security Association and Key Management Protocol (ISAKMP) or Internet Key Exchange (IKE) policy; and (2) the IPsec policy.
What is the difference between VPN and site-to-site VPN
Types of VPN connections
Client-to-Site (or Remote Access) and Site-to-Site (or Gateway-to-Gateway). The difference between them is simple: Client-to-Site VPN is characterized by single user connections. In contrast, Site-to-Site VPNs deal with remote connections between entire networks.
What are required components for a VPN to work
Imagine the internet as a bunch of roads that connect your home (your device) to a variety of destinations (websites and services). A VPN uses three basic components to work: the tunnel, the encryption, and the server.
What three items are required to establish a VPN connection
To get started, you'll need a VPN client, a VPN server, and a VPN router. The downloadable client connects you to servers around the world, so employees everywhere can access your small business network. The client can be used on devices like smartphones and laptops, even if workers are using public Wi-Fi networks.
What is the difference between VPN tunnel and site-to-site VPN
Security. With a site-to-site VPN, data is designed to only be encrypted between two points. The VPN tunnel itself doesn't offer any security features like access control or content regulation.
What is the difference between a VPN and a site-to-site connection
The main difference between a remote access VPN and a site-to-site VPN is how the systems are set up. The former involves a client/server model, while the latter connects two internet gateways and does not require users to install software.
What are the 3 major components of IPSec
IPsec is a suite of protocols widely used to secure connections over the internet. The three main protocols comprising IPsec are: Authentication Header (AH), Encapsulating Security Payload (ESP), and Internet Key Exchange (IKE).
What are the 3 protocols used in IPSec
Some IPSec protocols are given below.Authentication header (AH)Encapsulating security payload (ESP)Internet key exchange (IKE)
What is the advantage of site-to-site VPN
Site-to-site VPN security is the most important benefit, as IPsec protocols will ensure all traffic is encrypted in transit through the VPN tunnel. The site-to-site VPN tunnel only allows traffic from one end to the other, blocking any attempts to intercept the traffic from the outside.
Is site-to-site VPN the same as virtual private gateway
A virtual private gateway is the VPN concentrator on the Amazon side of the Site-to-Site VPN connection. You create a virtual private gateway and attach it to a virtual private cloud (VPC) with resources that must access the Site-to-Site VPN connection.
What are the three elements of a VPN
Imagine the internet as a bunch of roads that connect your home (your device) to a variety of destinations (websites and services). A VPN uses three basic components to work: the tunnel, the encryption, and the server.
What are the two 2 components required to configure remote access VPN
A remote access VPN comprises two key components: the network access server (NAS) and VPN client software (often called an app). The NAS enables users to connect to the remote VPN and could be a separate server or software installed on a shared server.
Does site-to-site VPN use internet
A site-to-site virtual private network (VPN) is a connection between two or more networks, such as a corporate network and a branch office network. Many organizations use site-to-site VPNs to leverage an internet connection for private traffic as an alternative to using private MPLS circuits.
What is remote access vs site-to-site VPN
A remote access VPN connects remote users from any location to a corporate network. A site-to-site VPN, meanwhile, connects individual networks to each other.
Which three steps are required to create an IPSec VPN tunnel
This step is required only if the VPN peer uses policy-based VPN.Select. Network. IPSec Tunnels. and click.Select the. Proxy IDs. tab.Select the. IPv4. or. IPv6.Click. Add. and enter the.Enter the. Local. IP address or subnet for the VPN gateway.Enter the. Remote. address for the VPN gateway.Select the. Protocol. :Click. OK. .
What are the requirements for IPsec
All IPsec VPN configurations require at least two items: (1) the Internet Security Association and Key Management Protocol (ISAKMP) or Internet Key Exchange (IKE) policy; and (2) the IPsec policy.
What are the 2 main protocols used by IPsec
IPsec originally defined two protocols for securing IP packets: Authentication Header (AH) and Encapsulating Security Payload (ESP). The former provides data integrity and anti-replay services, and the latter encrypts and authenticates data.
What is the difference between site-to-site VPN and tunnel interface
A site-to-site VPN does not give you that type of redundancy since the network is configured in the policy itself. Tunnel interface offloads that configuration from source network to destination network to a route policy.
What are the 4 main types of VPN
| VPN Type | Connection type |
|---|---|
| Personal VPN | Individual connects via a VPN server to the internet |
| Mobile VPN | Individual connects to the internet via a private network |
| Remote access VPN | The user connects to a private network |
| Site-to-site VPN | Private network connects to another private network |
Feb 2, 2023
Can my internet provider track me on VPN
Your ISP can't see your browsing history when you use a VPN. Everything you do stays private when you connect to a VPN server. Premium VPNs, like PIA, reroute your traffic through their own DNS servers, which conceals your DNS requests from your ISP.
What are the 3 major components of IPsec
IPsec is a suite of protocols widely used to secure connections over the internet. The three main protocols comprising IPsec are: Authentication Header (AH), Encapsulating Security Payload (ESP), and Internet Key Exchange (IKE).