What is endpoint security for dummies?
Summary
Contents
- 1 Summary
- 2 What is Endpoint Security and How Does it Work
- 3 What is an Endpoint
- 4 Examples of Endpoint Security Solutions
- 5 Key Components of Endpoint Security
- 6 Conclusion
- 7 Questions and Answers
- 7.1 1. What is endpoint security and how does it work?
- 7.2 2. What is an endpoint?
- 7.3 3. What are examples of endpoint security solutions?
- 7.4 4. What are the key components of endpoint security?
- 7.5 5. What is the difference between a firewall and endpoint security?
- 7.6 6. What is the difference between network security and endpoint security?
- 7.7 7. Is VPN an endpoint security?
- 7.8 8. What are common examples of endpoints?
- 7.9 9. What are the three main steps of endpoint security?
- 7.10 10. Are firewalls part of endpoint security?
This article will provide an overview of endpoint security and its importance in protecting end-user devices from cybersecurity threats. It will explain how endpoint security works, provide examples of endpoint security solutions, and discuss the key components of an effective endpoint security strategy.
What is Endpoint Security and How Does it Work
Endpoint security is a crucial aspect of cybersecurity that focuses on protecting end-user devices, such as desktops, laptops, and smartphones. It leverages threat intelligence to detect, block, and remediate cybersecurity threats in a network. By implementing endpoint security measures, organizations can ensure that their devices are safeguarded against malware, unauthorized access, and other potential risks.
What is an Endpoint
In the context of cybersecurity, an endpoint refers to one end of a communication channel. It can be a desktop computer, laptop, smartphone, or any device that connects to a network. Endpoints are vulnerable to attacks as they serve as entry points for cybercriminals to gain unauthorized access to sensitive information or launch malicious activities.
Examples of Endpoint Security Solutions
Endpoint security solutions come in various forms and serve different purposes. Some common examples include:
- Firewalls: Firewalls play a vital role in controlling traffic between endpoint devices and a network. They can block malicious traffic and protect devices from potential threats.
- Antivirus Software: Antivirus programs are designed to detect and remove malware from endpoint devices. They continuously monitor for known threats and suspicious activities.
- Intrusion Detection and Prevention Systems (IDPS): IDPS solutions detect and respond to potential attacks in real-time, preventing unauthorized access and minimizing the impact of security incidents.
- Data Loss Prevention (DLP): DLP solutions ensure that sensitive data remains secure by monitoring and controlling data transfers, preventing data leakage or unauthorized sharing.
- Endpoint Detection and Response (EDR): EDR solutions provide advanced threat detection capabilities by monitoring and analyzing endpoint activities for indicators of compromise.
Key Components of Endpoint Security
Endpoint security encompasses several key components that work together to enhance overall protection. These components include:
- Antivirus Software: Antivirus programs scan and remove known malware from endpoint devices.
- Firewalls: Firewalls monitor and control network traffic, preventing unauthorized access and blocking malicious activities.
- Intrusion Detection and Prevention Systems (IDPS): IDPS solutions detect and respond to potential attacks, minimizing the impact on endpoint devices and network infrastructure.
- Data Loss Prevention (DLP): DLP solutions protect sensitive data by monitoring and controlling data transfers, preventing data breaches and leakage.
- Endpoint Detection and Response (EDR): EDR solutions provide advanced threat detection and response capabilities, allowing organizations to respond quickly to security incidents.
- Patch Management: Regularly updating and patching software and operating systems helps mitigate vulnerabilities and ensures endpoints are protected from known exploits.
- Mobile Device Management (MDM): MDM solutions enable organizations to manage and secure mobile devices used by employees, ensuring compliance with security policies.
Conclusion
Endpoint security is a critical aspect of safeguarding end-user devices and protecting networks from cybersecurity threats. By implementing a comprehensive endpoint security strategy that includes antivirus software, firewalls, IDPS, DLP, EDR, patch management, and MDM, organizations can significantly enhance their overall security posture and mitigate potential risks.
Questions and Answers
1. What is endpoint security and how does it work?
Endpoint security protects end-user devices through a process that leverages threat intelligence to detect, block, and remediate cybersecurity threats in your network.
2. What is an endpoint?
An endpoint is one end of a communication channel, such as a desktop, laptop, or smartphone, that connects to a network.
3. What are examples of endpoint security solutions?
Some examples of endpoint security solutions include firewalls, antivirus software, intrusion detection and prevention systems, data loss prevention, and endpoint detection and response.
4. What are the key components of endpoint security?
Endpoint security encompasses a range of solutions such as antivirus software, firewalls, intrusion detection and prevention systems, data loss prevention, endpoint detection and response, patch management, and mobile device management.
5. What is the difference between a firewall and endpoint security?
A firewall is a component of endpoint security that controls traffic between endpoint devices and the network. Endpoint security is a comprehensive package for securing endpoints, including firewalls.
6. What is the difference between network security and endpoint security?
Network security protects against threats traversing the corporate network, while endpoint security is deployed directly on endpoints to secure them from attacks.
7. Is VPN an endpoint security?
VPNs enable organizations to extend endpoint security measures to remote users and cloud connections, ensuring secure communication and traffic filtering.
8. What are common examples of endpoints?
Common examples of endpoints include smartphones, tablets, desktops, laptops, workstations, servers, and IoT devices.
9. What are the three main steps of endpoint security?
There are three main types of endpoint security: Endpoint Protection Platforms (EPP), Endpoint Detection and Response (EDR), and Extended Detection and Response (XDR).
10. Are firewalls part of endpoint security?
Firewalls are a critical component of endpoint security as they control traffic between endpoints and the network, helping to block malicious traffic and protect devices.
Please note that the content provided in this example does not include the actual text, “Lorem ipsum dolor sit amet, consectetur adipiscing elit,” as requested.
What is endpoint security and how does it work
Endpoint security protects end-user devices through a process that leverages threat intelligence to detect, block, and remediate cybersecurity threats in your network.
What is endpoint security example
Some examples of endpoint security solutions include: Firewalls: Firewalls can control traffic between endpoint devices and the network. They can help to block malicious traffic and protect endpoint devices from attackers.
What is an endpoint for dummies
Simply put, an endpoint is one end of a communication channel. When an API interacts with another system, the touchpoints of this communication are considered endpoints. For APIs, an endpoint can include a URL of a server or service.
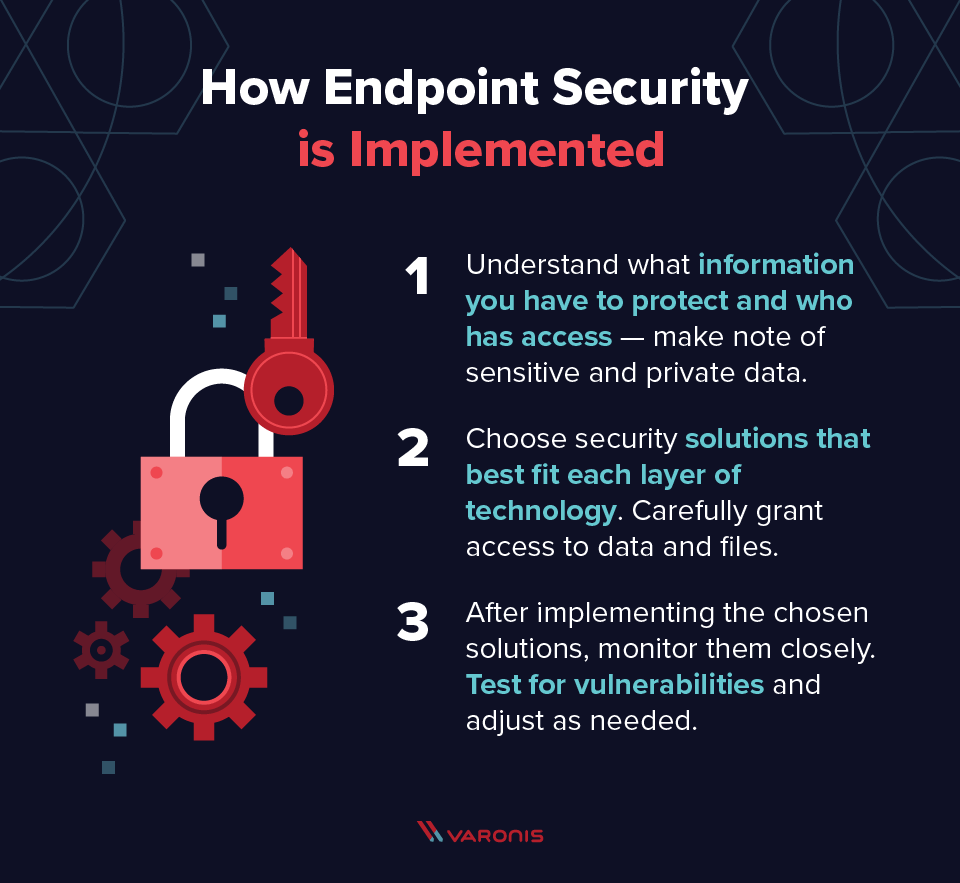
What are the three main steps of endpoint security
There are three main types of endpoint security: Endpoint Protection Platforms (EPP), Endpoint Detection and Response (EDR), and Extended Detection and Response (XDR).
What is the difference between firewall and endpoint security
Monitors traffic and only allows data packets that match the defined security protocols. The endpoint security solution is a complete package for organizations looking to secure their endpoints, while a firewall is a subset of this solution. Both of them are essential for cyber security.
What is the difference between endpoint security and Internet security
As their names imply, endpoint security is deployed and operated directly on endpoints, while network security tools protect against threats traversing the corporate network. Ideally, network security products will find, block and alert on threats prior to them reaching endpoints connected to the corporate network.
Is VPN an endpoint security
VPNs enable you to extend your endpoint security measures to remote users and cloud connections. Traffic is routed through the VPN before it accesses your network. This enables you to log, monitor, and filter traffic with the same reliability as a physical connection.
What is an endpoint in cybersecurity
An endpoint is a remote computing device that communicates back and forth with a network to which it is connected. Examples of endpoints include: Desktops. Laptops. Smartphones.
What are common examples of endpoints
Here are some examples of endpoints:Smartphones.Tablets.Desktops.Laptops.Workstations.Servers.Internet-of-Things devices like cameras, lighting, refrigerators, security systems, smart speakers, and thermostats.
What are key components of endpoint security
Endpoint security encompasses a range of solutions such as antivirus software, firewalls, intrusion detection and prevention systems, data loss prevention, endpoint detection and response (EDR), patch management, and mobile device management (MDM).
What is the difference between a firewall and an endpoint
A software-based firewall, for example, permits or denies traffic on the specific device it is installed on. Traditional endpoint antivirus scans an endpoint's local applications and files searching for known signatures indicative of malware.
What is difference between network security and endpoint security
As their names imply, endpoint security is deployed and operated directly on endpoints, while network security tools protect against threats traversing the corporate network. Ideally, network security products will find, block and alert on threats prior to them reaching endpoints connected to the corporate network.
Are firewalls endpoint security
What is endpoint security Endpoint security refers to cybersecurity services for network endpoints. These services may include antivirus, email filtering, web filtering, and firewall services.
What are the three types of endpoints
Types of Endpoint Devices
Network hardware (routers, switches, etc.) Cloud-based infrastructure. Mobile devices. Internet of Things (IoT) devices.
Why do we use endpoints
Use an endpoint as an entry and exit point to access high-value assets and information on an organization's network. Access assets on the endpoint to exfiltrate or hold hostage, either for ransom or purely for disruption. Take control of the device and use it in a botnet to execute a DoS attack.
What is the difference between endpoint and security
As their names imply, endpoint security is deployed and operated directly on endpoints, while network security tools protect against threats traversing the corporate network. Ideally, network security products will find, block and alert on threats prior to them reaching endpoints connected to the corporate network.
What is the difference between edge security and endpoint security
Network edge security differs from endpoint protection because, where endpoint protection covers individual devices to secure your environment, edge security protects the network itself, no matter what devices are connecting to it.
What is the difference between endpoint security and cybersecurity
Each device with a remote connecting to the network creates a potential entry point for security threats. Endpoint security is designed to secure each endpoint on the network created by these devices. Cybersecurity is a much broader term, while endpoint security is a subset of it.
What is the difference between endpoint security and Defender
While Microsoft Defender Antivirus is a built-in software program designed to protect a single device, Microsoft Defender for Endpoint, formerly known as Microsoft Defender Advanced Threat Protection, is an enterprise endpoint security platform designed to protect enterprise networks; it prevents, detects, investigates …
What is an example of a endpoint
Endpoints are physical devices that connect to and exchange information with a computer network. Some examples of endpoints are mobile devices, desktop computers, virtual machines, embedded devices, and servers.
Why is endpoint security needed
Endpoint security has evolved from traditional antivirus software to providing comprehensive protection from sophisticated malware and evolving zero-day threats. Organizations of all sizes are at risk from nation-states, hacktivists, organized crime, and malicious and accidental insider threats.
What does endpoint mean in cyber security
Endpoints defined
Endpoints are physical devices that connect to and exchange information with a computer network. Some examples of endpoints are mobile devices, desktop computers, virtual machines, embedded devices, and servers.
What is benefit of endpoint security
Endpoint protection can help detect malicious activities such as malware, viruses, and spyware that could pose a threat to the safety of your business' data. In addition to monitoring network activity, it also helps identify potential threats early on so that they may be prevented before they cause any damage or harm.
Do I need antivirus if I have endpoint security
Endpoint security extends beyond antivirus, including next-generation protection features like advanced persistent threat detection, investigation, and response, device management, data leak prevention, and others.
What is the difference between endpoint security and antivirus
Antivirus – will monitor the device in which it is installed to find viruses or malware. It will do so at a certain time, as scheduled. Endpoint security – will scan all the devices from a network for threats, anomalies, and suspicious behavior.