What is endpoint security example?
Summary
Contents
- 1 Summary
- 2 Main Thought
- 3 Key Points
- 4 1. Different Types of Endpoint Security
- 5 2. Examples of Endpoints
- 6 3. VPN and Endpoint Security
- 7 4. Firewall and Endpoint Security
- 8 5. Understanding Endpoints in Communication
- 9 6. Endpoint Security vs. Antivirus
- 10 7. Key Components of Endpoint Security
- 11 8. Routers and Endpoint Devices
- 12 9. McAfee and Endpoint Security
- 13 10. Endpoint Security vs. Internet Security
- 14 11. Providing Endpoint Security
- 15 Questions and Answers
- 15.1 1. What is considered endpoint security?
- 15.2 2. What is an example of an endpoint network?
- 15.3 3. What are the three main types of endpoint security?
- 15.4 4. Is VPN an endpoint security?
- 15.5 5. Is a firewall an endpoint?
- 15.6 6. What is an endpoint in simple terms?
- 15.7 7. What is endpoint security vs. antivirus?
- 15.8 8. What are the key components of endpoint security?
- 15.9 9. Is a router an endpoint device?
- 15.10 10. Is McAfee an endpoint security?
- 15.11 11. What is the difference between endpoint security and Internet security?
- 15.12 12. Is McAfee an endpoint?
- 15.13 13. How do you provide endpoint security?
In this article, we will explore the concept of endpoint security and its importance in protecting devices from malicious threats and cyberattacks. We will also discuss the key components of endpoint security and answer common questions related to this topic.
Main Thought
Endpoint security is crucial in today’s digital age. It helps safeguard devices like desktops, laptops, smartphones, and tablets from various cyber threats. By implementing effective endpoint security measures, individuals and organizations can better protect their sensitive information and maintain the integrity of their systems.
Key Points
1. Different Types of Endpoint Security
There are three main types of endpoint security: Endpoint Protection Platforms (EPP), Endpoint Detection and Response (EDR), and Extended Detection and Response (XDR). Each type offers different features and functionalities to enhance device security.
2. Examples of Endpoints
Endpoints are not limited to traditional devices like desktop computers and laptops. They also include mobile devices, servers, virtual machines, embedded devices, and Internet of Things (IoT) devices. These endpoints connect to computer networks and exchange information.
3. VPN and Endpoint Security
Virtual Private Networks (VPNs) provide an added layer of security to endpoint devices, especially when remote users and cloud connections are involved. By routing traffic through a VPN, organizations can log, monitor, and filter traffic with the same reliability as a physical connection.
4. Firewall and Endpoint Security
Network firewalls and host-based firewalls play different roles in endpoint security. Network firewalls filter traffic between networks, while host-based firewalls are installed on individual machines (endpoints) to control network traffic in and out of those devices.
5. Understanding Endpoints in Communication
Endpoints, in the context of communication channels and APIs, refer to the touchpoints of interaction. APIs interact with other systems through endpoints, which can be URLs or services that facilitate communication between different entities.
6. Endpoint Security vs. Antivirus
While antivirus software focuses on scanning devices for viruses and malware at specific times, endpoint security takes a broader approach. It scans all devices within a network for threats, anomalies, and suspicious behavior, providing comprehensive protection.
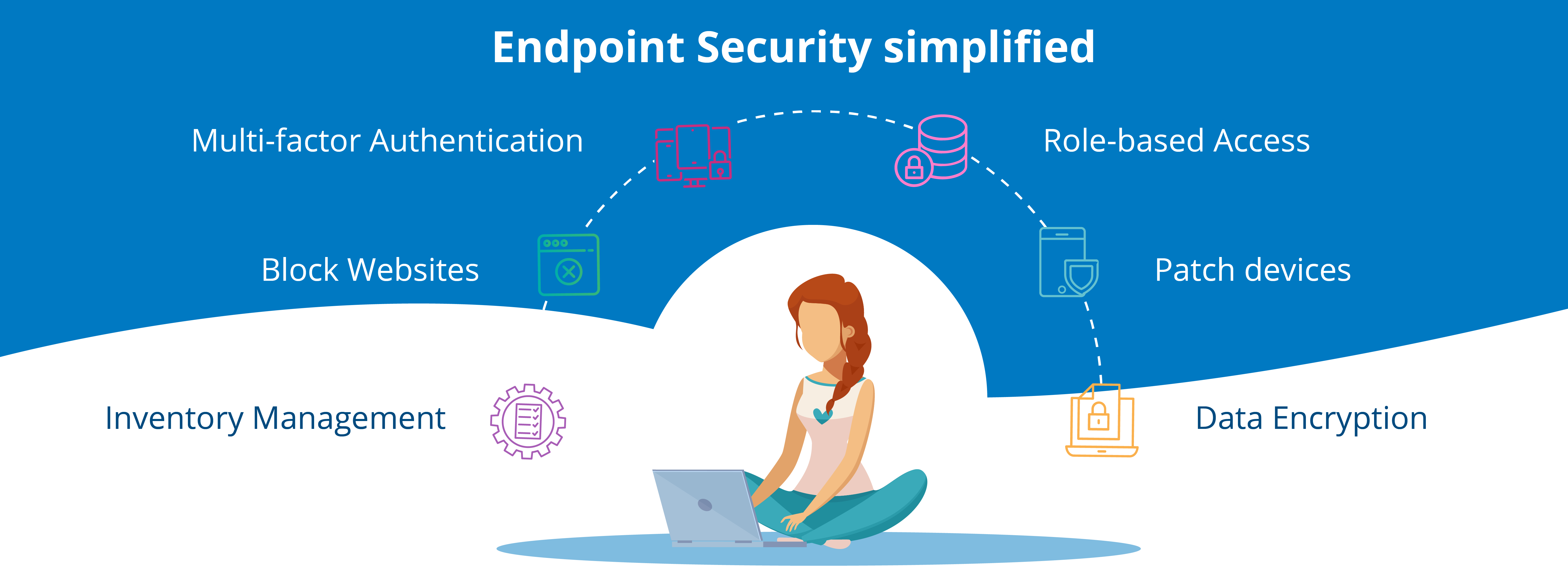
7. Key Components of Endpoint Security
Endpoint security encompasses several solutions, including antivirus software, firewalls, intrusion detection and prevention systems, data loss prevention, endpoint detection and response (EDR), patch management, and mobile device management (MDM). These components work together to create a robust security framework.
8. Routers and Endpoint Devices
Routers can be considered endpoint devices in traditional network setups. However, endpoints can also include modems, hubs, bridges, switches, data terminal equipment (such as digital telephone handsets and printers), or host computers like workstations and servers.
9. McAfee and Endpoint Security
McAfee is a well-established cybersecurity company that offers comprehensive endpoint protection solutions. Their Endpoint Protection system, including McAfee Endpoint Security technology, is designed to secure small businesses from a range of threats.
10. Endpoint Security vs. Internet Security
Endpoint security is deployed directly on devices, while network security tools focus on protecting the corporate network from threats. Ideally, network security tools detect and block threats before they reach the endpoints connected to the network.
11. Providing Endpoint Security
To enhance endpoint security, consider implementing the following measures: cataloging and assessing vulnerabilities, implementing a data access policy, securing IoT devices, encrypting data, and enforcing Bring Your Own Device (BYOD) policies.
Questions and Answers
1. What is considered endpoint security?
Endpoint security refers to the process of protecting devices like desktops, laptops, mobile phones, and tablets from malicious threats and cyberattacks.
2. What is an example of an endpoint network?
Everyday examples of endpoints include desktop computers, smartphones, tablets, laptops, and Internet of Things (IoT) devices.
3. What are the three main types of endpoint security?
The three main types of endpoint security are Endpoint Protection Platforms (EPP), Endpoint Detection and Response (EDR), and Extended Detection and Response (XDR).
4. Is VPN an endpoint security?
VPNs enable organizations to extend their endpoint security measures to remote users and cloud connections, ensuring that traffic is routed through the VPN to log, monitor, and filter it effectively.
5. Is a firewall an endpoint?
Network firewalls run on network hardware and filter traffic between two or more networks, while host-based firewalls are installed and run on individual machines (endpoints) to control network traffic.
6. What is an endpoint in simple terms?
An endpoint refers to one end of a communication channel, with APIs considering the touchpoints of communication as endpoints. This can include URLs or services that facilitate interaction between systems.
7. What is endpoint security vs. antivirus?
Antivirus software focuses on detecting and removing viruses or malware from individual devices, while endpoint security takes a broader approach, scanning all devices within a network for threats and suspicious behavior.
8. What are the key components of endpoint security?
Endpoint security encompasses solutions such as antivirus software, firewalls, intrusion detection and prevention systems, data loss prevention, endpoint detection and response (EDR), patch management, and mobile device management (MDM).
9. Is a router an endpoint device?
In traditional network setups, routers can be considered endpoint devices. However, endpoints can also include modems, hubs, bridges, switches, data terminal equipment, or host computers like workstations and servers.
10. Is McAfee an endpoint security?
McAfee is a renowned cybersecurity company with extensive experience in providing endpoint protection. Their Endpoint Protection system includes McAfee Endpoint Security technology, which caters to small businesses.
11. What is the difference between endpoint security and Internet security?
Endpoint security is deployed directly on devices to protect them, while Internet security tools focus on safeguarding the corporate network against threats that might reach the endpoints.
12. Is McAfee an endpoint?
McAfee is a reputable cybersecurity company that specializes in endpoint protection but is not considered an endpoint itself.
13. How do you provide endpoint security?
To enhance endpoint security, you can identify vulnerabilities, define data access policies, secure IoT devices, encrypt data, and enforce Bring Your Own Device (BYOD) policies.
What is considered endpoint security
Endpoint security is the process of protecting devices like desktops, laptops, mobile phones, and tablets from malicious threats and cyberattacks.
What is endpoint with example
Endpoints are physical devices that connect to and exchange information with a computer network. Some examples of endpoints are mobile devices, desktop computers, virtual machines, embedded devices, and servers.
Cached
What are the three main types of endpoint security
Different Types of Endpoints Security
There are three main types of endpoint security: Endpoint Protection Platforms (EPP), Endpoint Detection and Response (EDR), and Extended Detection and Response (XDR).
What is an example of an endpoint network
Everyday examples of endpoints include desktop computers, smartphones, tablets, laptops, and Internet of Things (IoT) devices.
Is VPN an endpoint security
VPNs enable you to extend your endpoint security measures to remote users and cloud connections. Traffic is routed through the VPN before it accesses your network. This enables you to log, monitor, and filter traffic with the same reliability as a physical connection.
Is a firewall an endpoint
Network firewalls filter traffic between two or more networks, such as the World Wide Web and a business' network, and run on network hardware. In contrast, host-based firewalls are installed and run on host computers (endpoints) and control network traffic in and out of those machines.
What is an endpoint in simple terms
Simply put, an endpoint is one end of a communication channel. When an API interacts with another system, the touchpoints of this communication are considered endpoints. For APIs, an endpoint can include a URL of a server or service.
How do you find the endpoint example
We've. Got 1 plus ax okay which we don't know divided by 2 should give us the x coordinate of the midpoint same thing with the Y's. Negative 4 plus y. Divided. By 2 equals.
What is endpoint security vs antivirus
Antivirus – will monitor the device in which it is installed to find viruses or malware. It will do so at a certain time, as scheduled. Endpoint security – will scan all the devices from a network for threats, anomalies, and suspicious behavior.
What are key components of endpoint security
Endpoint security encompasses a range of solutions such as antivirus software, firewalls, intrusion detection and prevention systems, data loss prevention, endpoint detection and response (EDR), patch management, and mobile device management (MDM).
Is a router an endpoint device
In a traditional sense, an endpoint can be a modem, hub, bridge, or switch. It also could be data terminal equipment (such as a digital telephone handset, router, or printer) or a host computer (such as a workstation or a server).
Is McAfee an endpoint security
McAfee is a veteran cybersecurity company with decades of endpoint protection experience. Its McAfee Endpoint Protection system includes its foundational McAfee Endpoint Security technology for small businesses.
What is the difference between endpoint security and Internet security
As their names imply, endpoint security is deployed and operated directly on endpoints, while network security tools protect against threats traversing the corporate network. Ideally, network security products will find, block and alert on threats prior to them reaching endpoints connected to the corporate network.
Is McAfee an endpoint
McAfee is a veteran cybersecurity company with decades of endpoint protection experience.
How do you provide endpoint security
7 Tips to Boost Endpoint SecurityIdentify your endpoint. The first step you should take to secure endpoints is cataloging and assessing vulnerabilities.Data Access Policy.IoT Security.Data encryption.Enforce Bring Your Own Device (BYOD) Policy.Advanced and Automated Endpoint Protection.Awareness.
What is the common endpoint
The common endpoint is called the vertex of the angle. The measure of an angle is a number representing the spread of the two arms of the angle.
Do I need antivirus if I have endpoint security
Endpoint security extends beyond antivirus, including next-generation protection features like advanced persistent threat detection, investigation, and response, device management, data leak prevention, and others.
Is Windows Defender an endpoint security
Microsoft Defender for Endpoint is an enterprise endpoint security platform designed to help enterprise networks prevent, detect, investigate, and respond to advanced threats. Example endpoints may include laptops, phones, tablets, PCs, access points, routers, and firewalls.
What is the difference between endpoint security and antivirus
Antivirus – will monitor the device in which it is installed to find viruses or malware. It will do so at a certain time, as scheduled. Endpoint security – will scan all the devices from a network for threats, anomalies, and suspicious behavior.
What is the difference between endpoint and antivirus
Antivirus – uses a signature-based threat detection, so more advanced threats, like fileless malware, can bypass this security solution. Once infiltrate into an endpoint, a malware can infect an entire network. Endpoint security – uses a firewall to identify even the most sophisticated threats.
Is Endpoint Security an antivirus
Endpoint security extends beyond antivirus, including next-generation protection features like advanced persistent threat detection, investigation, and response, device management, data leak prevention, and others.
Is A router an end point
In a traditional sense, an endpoint can be a modem, hub, bridge, or switch. It also could be data terminal equipment (such as a digital telephone handset, router, or printer) or a host computer (such as a workstation or a server).
What is the difference between antivirus and endpoint security
Antivirus – will monitor the device in which it is installed to find viruses or malware. It will do so at a certain time, as scheduled. Endpoint security – will scan all the devices from a network for threats, anomalies, and suspicious behavior.
How do I know if endpoint protection is installed
In the Configuration Manager console, click Monitoring. In the Monitoring workspace, expand Security and then click Endpoint Protection Status. In the Collection list, select the collection for which you want to view status information.
What is the difference between endpoint security and Defender
While Microsoft Defender Antivirus is a built-in software program designed to protect a single device, Microsoft Defender for Endpoint, formerly known as Microsoft Defender Advanced Threat Protection, is an enterprise endpoint security platform designed to protect enterprise networks; it prevents, detects, investigates …