What are two VPN authentication options?
Summary
Contents
- 1 Summary
- 2 Types of VPNs
- 3 Two-Factor Authentication for VPNs
- 4 Authentication Protocols for IPsec Site-to-Site VPNs
- 5 Best VPN Authentication Methods
- 6 Benefits of Two-Factor Authentication
- 7 Common VPN Types
- 8 Authentication Protocols for VPNs
- 9 Authentication in Always-On VPN
- 10 Common Two-Factor Authentication Methods
This article discusses various aspects of VPN authentication, including the types of VPNs, two-factor authentication for VPNs, and common authentication protocols used in VPNs. It also covers the importance of using 2FA for enhanced security and the best VPN authentication methods.
Types of VPNs
A VPN, or Virtual Private Network, can be categorized into two main types:
- Site-to-Site VPN: This type of VPN securely connects two geographically-distributed sites.
- Remote Access VPN: A remote access VPN allows remote users to connect securely to a corporate network.
Two-Factor Authentication for VPNs
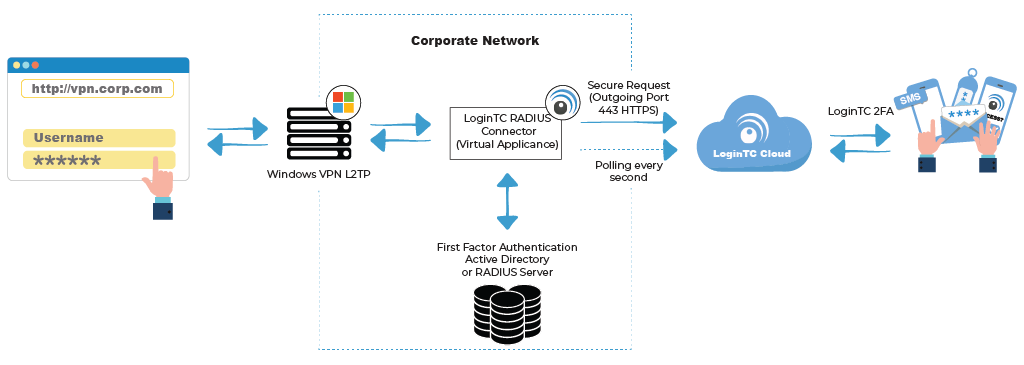
Two-factor authentication (2FA) adds an extra layer of security to VPN accounts. It requires users to enter a unique code, in addition to their username and password, to access the VPN. The code is usually generated by a mobile device with an authenticator app like Google Authenticator.
Authentication Protocols for IPsec Site-to-Site VPNs
IPsec, which stands for Internet Protocol Security, is a set of protocols used to secure VPN communications. The three main protocols that comprise IPsec are:
- Authentication Header (AH)
- Encapsulating Security Payload (ESP)
- Internet Key Exchange (IKE)
Best VPN Authentication Methods
OpenVPN and WireGuard are two protocols that offer strong encryption and high-security levels. OpenVPN utilizes AES 256-bit encryption, widely used by top-tier entities such as NASA and the military. WireGuard uses the XChaCha20 encryption protocol.
Benefits of Two-Factor Authentication
Using two-factor authentication provides an added layer of security. Even if a hacker knows the username and password, they cannot log in without the second authentication factor, such as a unique code sent to a smartphone or biometrics like fingerprints or facial recognition.
Common VPN Types
There are several types of VPNs, including:
- Personal VPN: Individuals connect to the internet via a VPN server.
- Mobile VPN: Individuals connect to the internet via a private network.
- Remote Access VPN: Users connect to a private network.
- Site-to-Site VPN: Private networks connect to another private network.
Authentication Protocols for VPNs
IPSec is commonly used as the authentication protocol for VPNs. It ensures secure data exchange through session authentication and data packet encryption. The encrypted message within the data packet is doubly encrypted for added security.
Authentication in Always-On VPN
Always-On VPN natively supports different types of authentication workflows, including usernames and passwords, smart cards (physical or virtual), and various Microsoft and third-party EAP (Extensible Authentication Protocol) types.
Common Two-Factor Authentication Methods
Two common methods for two-factor authentication are:
- Using a password as the first factor and receiving a text message with a code on a smartphone as the second factor.
- Using biometrics, such as fingerprints, facial recognition, or retina scans, as the second factor in addition to a password.
These methods enhance security, but they are not foolproof.
What are the two types of VPNs
Types of VPNsSite-to-Site VPN: A site-to-site VPN is designed to securely connect two geographically-distributed sites.Remote Access VPN: A remote access VPN is designed to link remote users securely to a corporate network.
What is two factor authentication VPN
By implementing 2FA, you are adding an extra layer of security to your VPN account, as it requires users to enter a unique code in addition to entering their username and password. Only your mobile device with an authenticator app like Google Authenticator can generate this code.
Which 3 types of authentication can be used for IPsec site-to-site VPNs
The three main protocols comprising IPsec are: Authentication Header (AH), Encapsulating Security Payload (ESP), and Internet Key Exchange (IKE).
What is VPN and its authentication process
VPN stands for "Virtual Private Network" and describes the opportunity to establish a protected network connection when using public networks. VPNs encrypt your internet traffic and disguise your online identity. This makes it more difficult for third parties to track your activities online and steal data.
What are the 4 main types of VPN
| VPN Type | Connection type |
|---|---|
| Personal VPN | Individual connects via a VPN server to the internet |
| Mobile VPN | Individual connects to the internet via a private network |
| Remote access VPN | The user connects to a private network |
| Site-to-site VPN | Private network connects to another private network |
Feb 2, 2023
Which three types of VPN are examples
There are several types of VPN and all four – personal VPNs, remote access VPNs, site-to-site VPNs, and extranet-based site-to-site VPNs cater to different needs and purposes. For example, personal VPNs focus on individuals who simply want to secure their online activities or access geo-restricted content.
What is an example of authentication in a VPN
VPN Authentication – IPsec VPN Tutorial Guide
Authentication is used to prove a user or entity is allowed access, and so provides a form of access control. For example when your logging on to your Windows desktop, and when you specify a username and password at the logon screen, you are authenticating yourself.
What should I use 2 factor authentication for
Using two-factor authentication is like using two locks on your door — and is much more secure. Even if a hacker knows your username and password, they can't log in to your account without the second credential or authentication factor.
What is the best VPN authentication method
OpenVPN and WireGuard are protocols that can offer the most robust encryption and the highest level of security. OpenVPN uses an AES 256-bit encryption key, widely used by top-tier entities, such as NASA and the military. Meanwhile, WireGuard® uses a comparatively new and sturdy encryption protocol called XChaCha20.
What are the three common types of VPNs
The four VPN types are:Personal VPN services.Mobile VPNs.Remote access VPNs.Site-to-site VPNs.
Which protocol is used as authentication protocol in VPN
IPSec is a VPN tunneling protocol that secures data exchange by enforcing session authentication and data packet encryption. It is twofold encryption — the encrypted message sits in the data packet, which is further encrypted again.
What authentication method does always on VPN use
Always On VPN natively supports EAP, which allows you to use a diverse set of Microsoft and third-party EAP types as part of the authentication workflow. EAP provides secure authentication based on the following authentication types: Username and password. Smart card (both physical and virtual)
Which 2 are most often used for 2 factor authentication
The first factor is a password and the second commonly includes a text with a code sent to your smartphone, or biometrics using your fingerprint, face, or retina. While 2FA does improve security, it is not foolproof.
What are three examples of two-factor authentication
Something you know, like a password or PIN. Something you have, like your ATM card, or your phone. Something you are, like a fingerprint or voice print.
What is the difference between SSTP and IKEv2
SSTP supports up to 128 concurrent connections only regardless of the gateway SKU. IKEv2 VPN, a standards-based IPsec VPN solution. IKEv2 VPN can be used to connect from Mac devices (macOS versions 10.11 and above).
What is the difference between IKEv2 and OpenVPN
The main difference between IKEv2 and OpenVPN is that IKEv2 is a standard protocol that is natively supported by many operating systems and offers faster and more stable connections, while OpenVPN is an open-source protocol that requires third-party software and offers more flexibility and security options.
What is the most secure VPN authentication method
All VPNs use encryption, but the quality of the encryption depends on which VPN protocol is used. OpenVPN, IKEv2, and L2TP support AES encryption, considered the gold standard, while WireGuard uses ChaCha20, which is also secure. PPTP uses the least secure encryption standard, MPPE.
Which authentication protocols used in VPN provide security
In addition to older and less-secure password-based authentication methods (which should be avoided), the built-in VPN solution uses Extensible Authentication Protocol (EAP) to provide secure authentication using both user name and password, and certificate-based methods.
What is the most common authentication method
1. Password-based authentication. Also known as knowledge-based authentication, password-based authentication relies on a username and password or PIN. This is the most common authentication method; anyone who has logged in to a computer knows how to use a password.
What are two examples of two-factor authentication
4. What are examples of 2FAOne example is sending a code to a user's mobile phone via text message, and this sending code from 2FA must be entered in addition to the password to log in.Another example is using a biometric identifier such as a fingerprint or iris scan.
What are the 3 ways of 2 factor authentication
Understanding Two-Factor Authentication (2FA)Something you know (your password)Something you have (such as a text with a code sent to your smartphone or other device, or a smartphone authenticator app)Something you are (biometrics using your fingerprint, face, or retina)
What are the two-factor authentication methods
Multi-Factor Authentication (MFA/2FA) MethodsPush Notification.U2F/WebAuthn Security Key.Email Link.Hardware OTP Token.Software OTP Token.SMS Passcode.QR Code.Biometrics (Fingerprinting, Face Recognition, and more)
What is IKEv2 IPsec or L2TP
Internet Key Exchange version 2 (IKEv2) is a tunneling protocol, based on IPsec, that establishes a secure VPN communication between VPN devices and defines negotiation and authentication processes for IPsec security associations (SAs).
Which is better IKEv2 or IPsec or L2TP
IKEv2 is not as common as L2TP/IPSec as it is supported on many fewer platforms (although this situation is changing fast). It is, however, considered at least as good as, if not superior to, L2TP/IPsec in terms of security, performance (speed), stability and the ability to establish (and re-establish) a connection.
What is best IKEv2 or IPsec or L2TP
L2TP/IPsec. IKEv2 and L2TP/IPsec provide the same level of security as they both work around IPsec. IKEv2 is, however, supported by fewer systems and software, though this shouldn't be a main concern to most users.