What are the disadvantages of Zero Trust network?
Summary
Contents
- 1 Summary
- 2 Personal Experience with Zero Trust Networks
- 3 The Challenges of Implementing Zero Trust
- 4 Key Points
- 5 1. Zero Trust as a Labor-Intensive Process
- 6 2. Integrating Existing Technologies and Legacy Systems
- 7 3. Challenges of Zero Trust Adoption
- 8 4. Advantages of Zero Trust
- 9 Questions and Answers
- 9.1 1. What are the disadvantages of Zero Trust networks?
- 9.2 2. What are the challenges of Zero Trust?
- 9.3 3. Why does Zero Trust fail?
- 9.4 4. Is Zero Trust good or bad?
- 9.5 5. What are the three main concepts of Zero Trust?
- 9.6 6. What is the reputation of Zeta Tau Alpha?
- 9.7 7. What is ZTA known for?
- 9.8 8. What is the biggest challenge for Zero Trust?
- 9.9 9. What are the pros and cons of Zero Trust?
- 9.10 10. What are the 5 pillars of Zero Trust?
- 9.11 11. What are the goals of Zero Trust?
Personal Experience with Zero Trust Networks
When I first heard about Zero Trust networks, I was intrigued by the concept. The idea of not relying on traditional perimeter defenses and instead adopting a more granular approach to network security seemed like a logical step forward. So, I decided to educate myself on Zero Trust and its potential benefits and drawbacks.
The Challenges of Implementing Zero Trust
One of the main challenges of implementing Zero Trust is the labor-intensive process it requires. Assessing every device and application and creating profiles for every user can be time-consuming and meticulous. Additionally, a slow implementation can pose a secondary risk.
Another challenge is integrating existing technologies and legacy systems. Zero Trust may not be compatible with certain systems, requiring additional resources and potentially hindering productivity.
Key Points
1. Zero Trust as a Labor-Intensive Process
Implementing Zero Trust involves assessing every device and application, creating profiles for every user, and meticulous planning. This can be time-consuming and may result in a slow implementation process.
2. Integrating Existing Technologies and Legacy Systems
Zero Trust may not be compatible with certain legacy systems, requiring additional resources and potentially hindering productivity.
3. Challenges of Zero Trust Adoption
Zero Trust adoption can be hindered by a lack of knowledge about the framework and a lack of buy-in from senior management. These obstacles can prevent organizations from realizing the benefits of Zero Trust.
4. Advantages of Zero Trust
By enforcing strict access controls, continuously verifying trust, and segmenting the network, Zero Trust helps prevent lateral movement by attackers, limits the scope of potential breaches, and minimizes the impact of compromised credentials.
Questions and Answers
1. What are the disadvantages of Zero Trust networks?
Adopting Zero Trust can be a labor-intensive process and may hinder productivity if not properly integrated with existing technologies and legacy systems.
2. What are the challenges of Zero Trust?
Challenges of Zero Trust include integrating existing technologies, resource constraints, policy development, asset inventory, integration with legacy systems, interoperability concerns, user experience considerations, and fostering a common understanding within the organization.
3. Why does Zero Trust fail?
The lack of knowledge about the framework and the lack of buy-in from senior management are primary reasons why organizations fail to realize the benefits of Zero Trust.
4. Is Zero Trust good or bad?
Zero Trust has advantages in preventing lateral movement, limiting breaches, and minimizing the impact of compromised credentials. However, it also presents challenges in implementation and integration.
5. What are the three main concepts of Zero Trust?
The three key components of a Zero Trust network are user/application authentication, device authentication, and trust.
6. What is the reputation of Zeta Tau Alpha?
Zeta Tau Alpha is usually considered a “middle tier” sorority known for caring about social issues and fostering a sense of community among its members.
7. What is ZTA known for?
Zeta Tau Alpha has numerous active collegiate chapters across the US and focuses on breast cancer education and awareness through partnerships with organizations like the American Cancer Society and the NFL.
8. What is the biggest challenge for Zero Trust?
The biggest challenge for organizations implementing Zero Trust is the lack of qualified vendors with a complete solution and the importance of integrating it into existing systems.
9. What are the pros and cons of Zero Trust?
Pros of Zero Trust include preventing attackers from gaining access to multiple resources at once. However, achieving a complete transition to a Zero Trust security model may not be feasible.
10. What are the 5 pillars of Zero Trust?
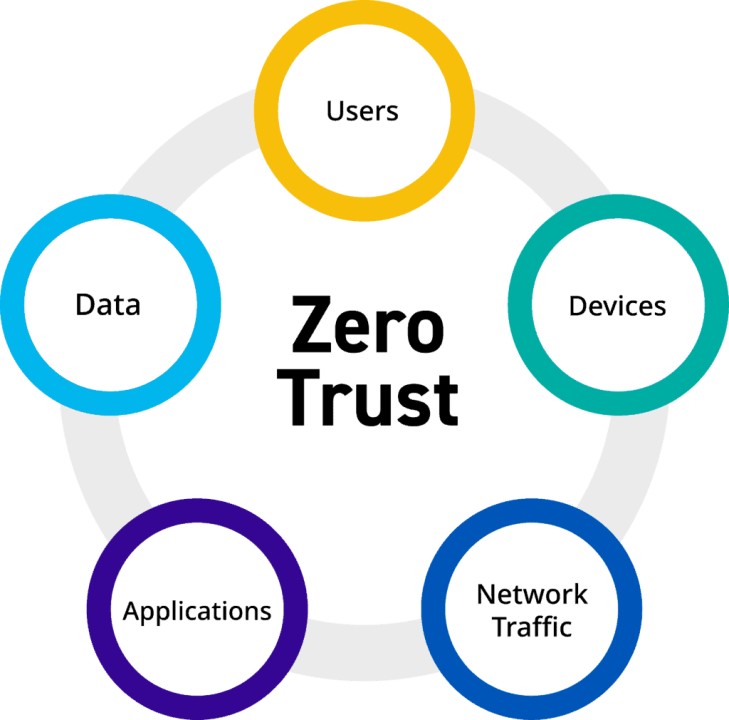
The five pillars of the Zero Trust Maturity Model are Identity, Devices, Network, Data, and Applications and Workloads.
11. What are the goals of Zero Trust?
The goals of Zero Trust include cultural adoption, security and defense of information systems, technology acceleration, and enabling Zero Trust within an organization.
What is the disadvantage of zero trust
Adopting Zero Trust can therefore be a labor intensive process. IT teams need to assess every device and application. Teams must create profiles for every user, with no exceptions. Meticulous planning can also lead to a secondary risk of moving too slowly.
Cached
What are the problems in zero trust
Top 6 challenges of a zero-trust security modelA piecemeal approach to zero-trust cybersecurity can create gaps.All-in-one zero-trust products don't exist.Legacy systems may not adapt to zero trust.Zero trust requires ongoing administration, maintenance.Zero trust can hinder productivity.
What are the challenges of ZTA
These challenges include integrating existing technologies, resource constraints, policy development, asset inventory, integration with legacy systems, interoperability concerns, user experience considerations, and fostering a common understanding within the organization.
Why does zero trust fail
However, the most prevalent obstacles in adopting Zero Trust were the lack of knowledge about the framework and the lack of buy-in from senior management. And the resounding result is that Gartner predicts that over 50% of organizations will fail to realize the benefits of Zero Trust.
Is Zero Trust good or bad
By enforcing strict access controls, continuously verifying trust, and segmenting the network, zero trust helps prevent lateral movement by attackers, limits the scope of potential breaches, and minimizes the impact of compromised credentials.
What are the three main concepts of Zero Trust
There are three key components in a zero trust network: user/application authentication, device authentication, and trust.
What is the reputation of Zeta Tau Alpha
Zeta itself is usually considered to be a “middle tier” sorority where the sisters tend to care more about social issues than about forming cliques. This reputation was part of what drew Buonomo to the chapter, and helped her realize it was the kind of community she'd been looking for.
What is ZTA known for
Zeta Tau Alpha has 171 active collegiate chapters across the US and more than 257,000 initiated members. Its charitable foundation, founded in 1954, focuses on breast-cancer education and awareness (hence its slogan Think Pink) and partners with the American Cancer Society and the NFL to that end.
What is the biggest challenge for zero trust
Zero Trust Implementation May Be Easier Said Than Done
However, even if they do realize the importance of integration, the most prominent challenge organizations report facing in building a zero trust strategy is the lack of qualified vendors with a complete solution.
Is zero trust good or bad
By enforcing strict access controls, continuously verifying trust, and segmenting the network, zero trust helps prevent lateral movement by attackers, limits the scope of potential breaches, and minimizes the impact of compromised credentials.
What are the pros and cons of zero trust
Pro: Zero-trust systems prevent attackers from gaining access to multiple resources at a time. Con: It may not be possible to achieve a transition to a fully zero-trust security model.
What are the 5 pillars of Zero Trust
The five pillars of the Zero Trust Maturity Model are: Identity; Devices; Network, Data, and Applications and Workloads.
What are the 4 goals of Zero Trust
The strategy unveiled in the fall outlined four high-level goals for achieving the DOD's vision for a zero trust architecture including cultural adoption, security and defense of DOD information systems, technology acceleration and zero trust enablement.
What is the Zeta Beta Tau controversy
In February 2018, the Cornell University chapter of Zeta Beta Tau was placed on probation for two years following an investigation into multiple reports of "pig roasts" in which men competed to try to sleep with and humiliate women they considered to be overweight.
What are the stereotypes of Zeta
Along with being seen as compassionate and smart women, the members of Zeta Phi Beta were stereotyped and characterized most often as being portly, unattractive, homely, and dark-skinned women.
What are 3 of the more common challenges associated with implementing zero trust architectures
Access to sensitive data is part of the job, but if people change roles and find themselves locked out of pertinent files or applications, their work suffers. This scenario is precisely what leads to three common challenges with zero trust rollouts: productivity, change, and collaboration.
What is the biggest challenge for Zero Trust
Zero Trust Implementation May Be Easier Said Than Done
However, even if they do realize the importance of integration, the most prominent challenge organizations report facing in building a zero trust strategy is the lack of qualified vendors with a complete solution.
What are the three core principles of zero trust
As business and technology continue to evolve, the three core principles of Zero Trust security remain consistent. Never trust. Always verify. Implement Zero Trust security for your business.
What are the three main concepts of zero trust
There are three key components in a zero trust network: user/application authentication, device authentication, and trust.
What are the three core principles of Zero Trust
As business and technology continue to evolve, the three core principles of Zero Trust security remain consistent. Never trust. Always verify. Implement Zero Trust security for your business.
What are Zetas sorority known for
Zeta chapters and auxiliary groups have given untotaled hours of voluntary service to educate the public, assist youth, provide scholarships, support organized charities, and promote legislation for social and civic change.
What is the threat model of a zero trust architecture
Zero trust is a modern security strategy based on the principle: never trust, always verify. Instead of assuming everything behind the corporate firewall is safe, the Zero Trust model assumes breach and verifies each request as though it originates from an open network.
What are stereotypes about zetas
Along with being seen as compassionate and smart women, the members of Zeta Phi Beta were stereotyped and characterized most often as being portly, unattractive, homely, and dark-skinned women.
Is Zeta a top tier sorority
Zeta itself is usually considered to be a “middle tier” sorority where the sisters tend to care more about social issues than about forming cliques.
What are the 5 pillars of zero trust
The five pillars of the Zero Trust Maturity Model are: Identity; Devices; Network, Data, and Applications and Workloads.