Is ZeroTier safe?
Summary
Contents
- 1 Summary
- 2 Main Thought
- 3 Key Points
- 4 1. ZeroTier’s Safety
- 5 2. Difference between ZeroTier and VPN
- 6 3. ZeroTier as a VPN
- 7 4. Purpose of ZeroTier
- 8 5. Most Hacked Device
- 9 6. Finding Zero-Day Exploits
- 10 7. ZTNA vs. VPN Security
- 11 8. ZeroTier’s Pricing
- 12 9. Safest VPN Type
- 13 10. VPNs for Hackers
- 14 11. ZeroTier’s Founder
- 15 12. Devices Unlikely to Be Hacked
- 16 13. Most Targeted Websites for Hacking
- 17 14. Famous Zero-Day Exploit
In this article, I will be discussing various topics related to ZeroTier and cybersecurity. From the safety of ZeroTier to the comparison between VPNs and ZTNA, we will delve into different aspects of these subjects.
Main Thought
ZeroTier provides secure connectivity for devices and allows users to build virtualized networks of different types. The simplicity and global connectivity it offers make it an attractive option for many.
Key Points
1. ZeroTier’s Safety
ZeroTier has been known to be safe for user use. However, there have been instances where attackers were able to impersonate a ZeroTier node and inject packets into a network. These cases were limited and specific circumstances were required for such attacks.
2. Difference between ZeroTier and VPN
ZeroTier offers low latency connections compared to traditional VPNs after establishing a peer-to-peer connection. It efficiently utilizes existing bandwidth, resulting in minimal latency issues for users.
3. ZeroTier as a VPN
ZeroTier can be used as a VPN service and is simple to configure. It is also free for up to 100 devices, making it an affordable option for users.
4. Purpose of ZeroTier
ZeroTier aims to provide secure connectivity for devices anywhere. It allows for the creation of modern, secure multi-point virtualized networks, ranging from peer-to-peer networking to multi-cloud mesh infrastructure.
5. Most Hacked Device
IP cameras are often vulnerable to hacking attacks due to poor security measures. Attackers can exploit these cameras for spying or launch coordinated Distributed Denial of Service (DDoS) attacks.
6. Finding Zero-Day Exploits
Hackers discover zero-day exploits through various means. Some discover vulnerabilities when a program behaves suspiciously, while others are identified by developers themselves. Attackers have even exploited zero-day vulnerabilities in popular operating systems such as Google’s Android.
7. ZTNA vs. VPN Security
Zero Trust Network Access (ZTNA) provides enhanced access control and authentication, making it more secure than traditional VPNs where remote machines can access the entire internal network once authenticated.
8. ZeroTier’s Pricing
ZeroTier controllers and nodes can be self-hosted for free when used for non-commercial purposes. Commercial use requires contacting ZeroTier for further information. ZeroTier’s Business Source License (BSL) governs its pricing and usage.
9. Safest VPN Type
Lightway stands out as the most secure VPN protocol due to its usage of wolfSSL—a FIPS 140-2 validated cryptography library.
10. VPNs for Hackers
NordVPN and Surfshark are recommended VPN services for ethical hackers. NordVPN provides exceptional speeds, high security, and a strict no-log policy, while Surfshark offers affordability.
11. ZeroTier’s Founder
ZeroTier was founded in 2015 by Adam Ierymenko, driven by a vision to directly connect devices globally and enable decentralized computing.
12. Devices Unlikely to Be Hacked
The most secure phones on the market, such as Bittium Tough Mobile 2C and K-iPhone, are less prone to hacking compared to other devices.
13. Most Targeted Websites for Hacking
Websites like Riotgames.com, Netflix, Spotify.com, and Origin.com are commonly targeted by hackers.
14. Famous Zero-Day Exploit
Stuxnet is one of the most well-known examples of a zero-day attack. Discovered in 2010, it targeted manufacturing computers running programmable logic controller (PLC) software.
Can ZeroTier be hacked
It was possible for an attacker to impersonate a ZeroTier node and inject packets into a network, under very specific circumstances.
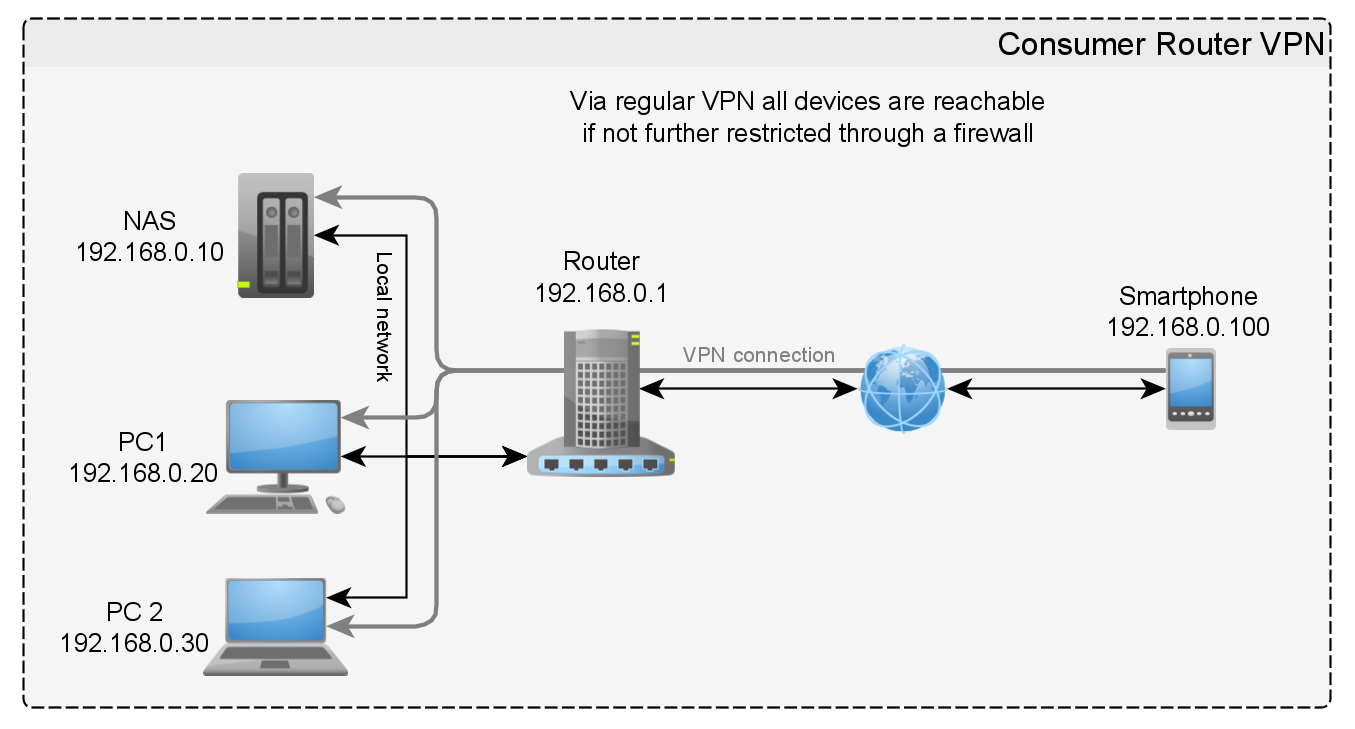
How is ZeroTier different from VPN
ZeroTier offers very low latency connections compared to traditional VPNs, once a peer-to-peer connection has been established. Existing bandwidth is used efficiently and users rarely face latency issues.
Cached
Can ZeroTier be used as a VPN
ZeroTier is one of the easiest VPN services to configure and it's completely free for up to 100 devices. The entire process, from start to finish, should only take a few minutes.
What is the purpose of ZeroTier
Securely connect any device, anywhere. ZeroTier lets you build modern, secure multi-point virtualized networks of almost any type. From robust peer-to-peer networking to multi-cloud mesh infrastructure, we enable global connectivity with the simplicity of a local network.
What device gets hacked the most
IP cameras
IP cameras are infamous for having poor security. They are being hacked not only to spy on people, but also to participate in coordinated DDoS attacks. Infected IP cameras also often become part of botnets.
How do hackers find zero day exploits
In most cases, hackers use code to exploit zero-day. Sometimes it is discovered by an individual when the program behaves suspiciously, or the developer himself may recognize the vulnerability. Attackers have found a new route by exploiting a zero-day vulnerability in Google's Android mobile operating system.
Is VPN more secure than ZTNA
With ZTNA, the user and the device have to always authenticate each time they make a new request. This enhanced access control makes ZTNA more secure than VPN, in which a remote machine once authenticated could access the entire internal network.
Is ZeroTier free
You can self-host ZeroTier controllers and nodes for free if you use it for non-commercial purposes. Please contact us to learn more. ZeroTier's BSL is based on the Business Source License (BSL) version 1.1 developed by MariaDB.
What is the safest VPN type
What is the most secure VPN protocol Lightway, IKEv2, L2TP, and OpenVPN are all secure protocols, but the title of the most secure VPN protocol should go to Lightway, which uses wolfSSL, a well-established cryptography library that is FIPS 140-2 validated—which means it has been rigorously vetted by third parties.
What type of VPN do hackers use
NordVPN: Our top VPN for hackers! Boasts outstanding speeds, a high level of security, and a strict no-log policy. Includes a risk-free 30-day money-back guarantee. Surfshark: The best budget option for ethical hackers.
Who owns ZeroTier
Adam Ierymenko
ZeroTier was founded by Adam Ierymenko in 2015 driven by a simple but powerful vision… to directly connect the world's devices and enable a new era of decentralized computing.
What devices Cannot be hacked
Most Secure PhonesBittium Tough Mobile 2C. The first device on the list of most secure Phones is the Bittium Tough Mobile 2C.K-iPhone – One of the most secure Phones.Most secure Phones – Solarin From Sirin Labs.Among the most secure Phones – Purism Librem 5.Sirin Labs Finney U1.
What websites are you most likely to get hacked from
Netflix And Spotify Users Are The Most Likely To Be Hacked — Here's What To Do
| Rank | Top targeted brands |
|---|---|
| 1. | Riotgames.com |
| 2. | Netflix |
| 3. | Spotify.com |
| 4. | Origin.com |
What is the most famous zero-day exploit
One of the most famous examples of a zero-day attack was Stuxnet. First discovered in 2010 but with roots that spread back to 2005, this malicious computer worm affected manufacturing computers running programmable logic controller (PLC) software.
How common are zero-day attacks
In 2021, the Mandiant report found 80 zero-days exploited, which more than doubled the previous record set in 2019. The primary actors exploiting these vulnerabilities continue to be. The researchers also detected a notable rise in financially driven attacks.
What is the safest VPN to use
The Best VPNs of 2023NordVPN: Best Overall.TorGuard VPN: Most Customizable VPN.TunnelBear: Best for Beginners.Private Internet Access: Best for Customizable Security.ProtonVPN: Best for Tor Integrations.hide.me: Best for Wi-Fi Security.Surfshark: Best for Unlimited Connections.
What is the least secure VPN
All VPNs use encryption, but the quality of the encryption depends on which VPN protocol is used. OpenVPN, IKEv2, and L2TP support AES encryption, considered the gold standard, while WireGuard uses ChaCha20, which is also secure. PPTP uses the least secure encryption standard, MPPE.
What type of VPN is ZeroTier
ZeroTier
| Developer(s) | ZeroTier, Inc. |
|---|---|
| Operating system | Microsoft Windows, macOS, Linux, Linux on ARM |
| Type | SD-WAN, P2P, VPN |
| License | Business Source License (Free for personal use. Enterprise pricing available); formerly GPLv3 |
| Website | https://www.zerotier.com |
What VPN do most hackers use
Best VPNs for HackersNordVPN: Our top VPN for hackers!Surfshark: The best budget option for ethical hackers.ExpressVPN: An advanced VPN with several added security options to enhance your online privacy.CyberGhost: A well-respected VPN with fast servers in 94 countries.
What VPN does not protect you from
Another common misconception is that a VPN protects you from online threats or cyberattacks. A VPN helps you stay invisible and behind the scenes, but it doesn't give you immunity against online risks like malware, ransomware, phishing attacks, or even computer viruses. That's where your antivirus software comes in.
Can hackers track you if you use VPN
A premium quality VPN encrypts data and hides your IP address by routing your activity through a VPN server; even if someone tries to monitor your traffic, all they'll see is the VPN server's IP and complete gibberish. Beyond that, you can only be tracked with information you provide to sites or services you log into.
Can someone hack me if I have VPN
By encrypting all your internet traffic and hiding your IP address, a VPN makes it nearly impossible for anyone to track or get ahold of your sensitive data. However, a VPN cannot protect you from installing malware or clicking on malicious links, but it can protect you from a few specific techniques used by hackers.
Is ZeroTier free to use
You can self-host ZeroTier controllers and nodes for free if you use it for non-commercial purposes. Please contact us to learn more. ZeroTier's BSL is based on the Business Source License (BSL) version 1.1 developed by MariaDB.
Where is ZeroTier based
ZeroTier, Inc. is a software company with a freemium business model based in Irvine, California. ZeroTier provides proprietary software, SDKs and commercial products and services to create and manage virtual software-defined networks.
What is the most hacked security system
The systems our testers were able to jam are the Abode Iota All-In-One Kit, Cove Home Security System, Eufy 5-Piece Home Alarm Kit, Ring Alarm Security Kit (2nd gen.), and SimpliSafe The Essentials SS3-01.