Is VLAN good for security?
Summary
Contents
- 1 Summary
- 2 Do VLANs improve security?
- 3 Is VLAN a security measure?
- 4 Why is VLAN important in network security?
- 5 What are the 3 benefits of a VLAN?
- 6 What are the disadvantages of a VLAN?
- 7 Can malware spread through VLAN?
- 8 What are the security weaknesses of VLAN?
- 9 Is a VLAN more secure than a subnet?
- 10 Why is VLAN 1 a security risk?
- 11 Why is VLAN not secure?
- 12 What is the best use of VLAN?
- 13 What is the main purpose of VLAN?
- 14 Why use VLAN instead of a router?
- 15 Can a VLAN be hacked?
This article discusses the use of VLANs (Virtual Local Area Networks) in network security and explores their benefits and weaknesses.
Do VLANs improve security?
Improved security: Using VLANs improves security by reducing both internal and external threats. Internally, separating users improves security and privacy by ensuring that users can only access the networks that apply to their responsibilities. External threats are also minimized.
Is VLAN a security measure?
Creating isolated guest networks: VLANs prevent unauthorized access and associated security issues by isolating guest devices from the internal network. This isolation guarantees that visitors have access to the resources they require while safeguarding the internal network’s integrity and security.
Why is VLAN important in network security?
VLANs can also limit the access of internal users and specific device types to a specified network segment. This makes sure segments are accessed only by authorized users and devices, and it’s particularly helpful for segments with systems containing sensitive information, such as the company’s financial system.
What are the 3 benefits of a VLAN?
VLANs provide a number of advantages including ease of administration, confinement of broadcast domains, reduced network traffic, and enforcement of security policies.
What are the disadvantages of a VLAN?
VLANs require more configuration and management than subnetting or routing, as they involve assigning VLAN IDs, trunking ports, and setting up inter-VLAN routing. This can lead to more potential for human error, misconfiguration, or security breaches.
Can malware spread through VLAN?
VLAN hopping is a significant security threat. It lets malicious actors gain access to networks that they don’t have permission to enter. A hacker can then steal passwords or other protected information, install malware and spyware, spread Trojan horses, worms, and viruses, or corrupt, modify, or delete critical data.
What are the security weaknesses of VLAN?
One of the main security risks of VLAN trunking is spoofing attacks, where an attacker can send packets with a forged VLAN tag to access or disrupt other VLANs on the trunk. This can lead to data leakage, denial of service, or network compromise.
Is a VLAN more secure than a subnet?
Subnetting and VLANs are two important concepts to understand when it comes to networking. Subnets are a way of breaking up a larger network into smaller, more scalable and secure networks. VLANs provide an additional layer of security by creating virtual networks within the same physical infrastructure.
Why is VLAN 1 a security risk?
The main reasons VLAN 1 is considered a potential security risk is because it is the default VLAN on switches. This means that if you have any enabled and unconfigured ports on a switch, someone can plug in with immediate access to VLAN 1.
Why is VLAN not secure?
VLANs, or virtual LANs, are a way of dividing a physical network into logical segments that can isolate traffic and improve security. However, VLANs are not immune to attacks, such as VLAN hopping and spoofing, that can compromise the network integrity and data confidentiality.
What is the best use of VLAN?
The most common use of VLANs is to separate traffic from different departments or network locations into its subnet, making it easier to manage each group separately.
What is the main purpose of VLAN?
VLANs allow network administrators to automatically limit access to a specified group of users by dividing workstations into different isolated LAN segments. When users move their workstations, administrators don’t need to reconfigure the network or change VLAN groups.
Why use VLAN instead of a router?
The main advantage of using VLANs is that they allow you to separate traffic from different users onto different segments of the same physical network switch. You don’t need to run dedicated lines for each user group.
Can a VLAN be hacked?
VLAN (Virtual Local Area Network) security is an important consideration. While VLANs provide an additional layer of security, they are not invulnerable to attacks. VLAN hopping and spoofing are some of the security risks associated with VLANs, requiring proper configuration and monitoring to prevent unauthorized access and data breaches.
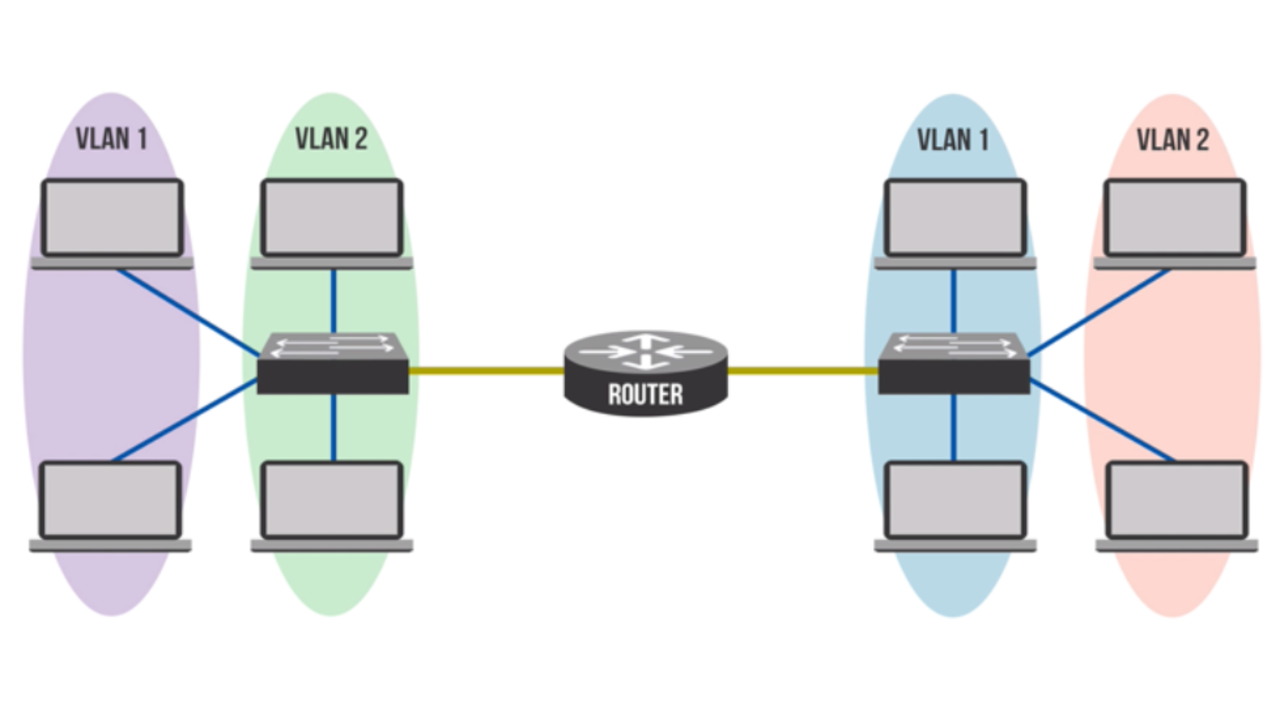
Do VLANs improve security
Improved security: Using VLANs improves security by reducing both internal and external threats. Internally, separating users improves security and privacy by ensuring that users can only access the networks that apply to their responsibilities. External threats are also minimized.
Is VLAN a security measure
Creating isolated guest networks: VLANs prevent unauthorized access and associated security issues by isolating guest devices from the internal network. This isolation guarantees that visitors have access to the resources they require while safeguarding the internal network's integrity and security.
Cached
Why is VLAN important in network security
VLANs can also limit the access of internal users and specific device types to a specified network segment. This makes sure segments are accessed only by authorized users and devices, and it's particularly helpful for segments with systems containing sensitive information, such as the company's financial system.
What are the 3 benefits of a VLAN
VLANs provide a number of advantages including ease of administration, confinement of broadcast domains, reduced network traffic, and enforcement of security policies.
What are the disadvantages of a VLAN
VLANs require more configuration and management than subnetting or routing, as they involve assigning VLAN IDs, trunking ports, and setting up inter-VLAN routing. This can lead to more potential for human error, misconfiguration, or security breaches.
Can malware spread through VLAN
VLAN hopping is a significant security threat. It lets malicious actors gain access to networks that they don't have permission to enter. A hacker can then steal passwords or other protected information; install malware and spyware; spread Trojan horses, worms, and viruses; or corrupt, modify, or delete critical data.
What are the security weaknesses of VLAN
One of the main security risks of VLAN trunking is spoofing attacks, where an attacker can send packets with a forged VLAN tag to access or disrupt other VLANs on the trunk. This can lead to data leakage, denial of service, or network compromise.
Is A VLAN more secure than a subnet
Subnetting and VLANs are two important concepts to understand when it comes to networking. Subnets are a way of breaking up a larger network into smaller, more scalable and secure networks. VLANs provide an additional layer of security by creating virtual networks within the same physical infrastructure.
Why is VLAN 1 a security risk
The main reasons vlan 1 is considered a potential security risk is because it is the default vlan on switches. This means that if you have any enabled and unconfigured ports on a switch, someone can plug in with immediate access to vlan 1.
Why is VLAN not secure
VLANs, or virtual LANs, are a way of dividing a physical network into logical segments that can isolate traffic and improve security. However, VLANs are not immune to attacks, such as VLAN hopping and spoofing, that can compromise the network integrity and data confidentiality.
What is the best use of VLAN
The most common use of VLANs is to separate traffic from different departments or network locations into its subnet, making it easier to manage each group separately.
What is the main purpose of VLAN
VLANs allow network administrators to automatically limit access to a specified group of users by dividing workstations into different isolated LAN segments. When users move their workstations, administrators don't need to reconfigure the network or change VLAN groups.
Why use VLAN instead of a router
The main advantage of using VLANs is that they allow you to separate traffic from different users onto different segments of the same physical network switch. You don't need to run dedicated lines for each user group.
Can a VLAN be hacked
VLAN (Virtual Local Area Network) security is an important aspect of network security. With the increasing use of virtual networks, the risk of VLAN attack has also increased. Attackers can gain access to sensitive data or disrupt network operations by exploiting vulnerabilities in the VLAN configuration.
What is the disadvantage of VLAN
Disadvantages of VLANs
VLANs require more configuration and management than subnetting or routing, as they involve assigning VLAN IDs, trunking ports, and setting up inter-VLAN routing. This can lead to more potential for human error, misconfiguration, or security breaches.
Why not use VLAN
Not using VLAN1 is just a good practice recommendation as it is the default VLAN of any switch, but it does not mean that it cannot be used or that network security is at risk. Security goes much further than a simple VLAN. If possible, avoid using it, but if you do, that's fine, it's not the end of the world.
How to use VLAN for security
The first principle in securing a VLAN network is physical security. If an organization does not want its devices tampered with, physical access must be strictly controlled. Core switches are usually safely located in a data center with restricted access, but edge switches are often located in exposed areas.
What are the pros and cons of VLAN
The primary advantage of VLAN is that it reduces the size of broadcast domains. The drawback of VLAN is that an injected packet may lead to a cyber-attack. VLAN is used when you have 200+ devices on your LAN.
What is the difference between VLAN and VPN
A VLAN is basically a means to logically segregate or geographically distance apart networks without physically segregating them with multiple switches. and the VPN on the other hand is used to connect two points in a secure and secure tunnel or moreover encrypted way.
When should you use VLANs
VLANs are commonly used to separate traffic between two or more groups of hosts. For example, you might want to segregate traffic between employees and contractors. Or you might want to separate traffic between production servers.
What are three disadvantages of VLANs
Disadvantages of VLANA packet can leak from one VLAN to other.An injected packet may lead to a cyber-attack.Threat in a single system may spread a virus through a whole logical network.You require an additional router to control the workload in large networks.You can face problems in interoperability.
What are the drawbacks of VLAN
Using VLANs can also have some drawbacks for your network, such as increasing network complexity due to more dependencies and interactions between VLANs, limiting scalability due to limited number of devices and ports, and introducing security risks due to potential vulnerabilities or misconfigurations.
What are the security risks of VLAN
One of the main security risks of VLAN trunking is spoofing attacks, where an attacker can send packets with a forged VLAN tag to access or disrupt other VLANs on the trunk. This can lead to data leakage, denial of service, or network compromise.
What is the disadvantage of a VLAN
VLANs require more configuration and management than subnetting or routing, as they involve assigning VLAN IDs, trunking ports, and setting up inter-VLAN routing. This can lead to more potential for human error, misconfiguration, or security breaches.
What are the disadvantages of VLANs
Disadvantages of VLANs
VLANs require more configuration and management than subnetting or routing, as they involve assigning VLAN IDs, trunking ports, and setting up inter-VLAN routing. This can lead to more potential for human error, misconfiguration, or security breaches.