Is there something safer than a VPN?
Summary
Contents
- 1 Summary
- 2 Main Thought
- 3 Main Thought
- 4 Key Points
- 5 1. Zero Trust Network Access
- 6 2. Secure Alternatives to VPNs
- 7 3. Limitations of VPNs
- 8 4. Tor Over VPN
- 9 5. Benefits of Zero Trust
- 10 Questions and Answers
- 10.1 1. Is there something safer than a VPN?
- 10.2 2. What can we use instead of a VPN?
- 10.3 3. Does a VPN actually keep you safe?
- 10.4 4. Is Tor over VPN safe?
- 10.5 5. Can anything bypass a VPN?
- 10.6 6. Is a free VPN better than no VPN?
- 10.7 7. What does a VPN not hide?
- 10.8 8. Can hackers get through a VPN?
- 10.9 9. Can police track VPN and Tor?
- 10.10 10. Can hackers track you on Tor?
- 10.11 11. What are the disadvantages of zero trust network?
When it comes to online security, many people turn to VPNs for protection. However, there are alternative options that may be more secure. This article explores the limitations of VPNs and discusses alternatives, such as software-defined perimeters and zero-trust network access.
Main Thought
VPNs have long been touted as the go-to solution for online security. But are they truly foolproof?
Main Thought
Zero trust network access is a promising alternative to traditional VPNs.
Key Points
1. Zero Trust Network Access
Zero trust network access is a network architecture that implements zero-trust principles to provide more secure remote access than VPNs.
2. Secure Alternatives to VPNs
Other secure alternatives to VPNs include secure access service edge (SASE), software-defined perimeter (SDP), and software-defined wide area networks (SD-WAN).
3. Limitations of VPNs
While VPNs may offer strong encryption, they can’t protect against all online threats, such as viruses, malware, and phishing scams.
4. Tor Over VPN
Using Tor over a VPN can offer enhanced privacy, but it’s important to note that Tor is not completely foolproof and may still leave room for malicious software.
5. Benefits of Zero Trust
Zero trust networks offer quick and efficient connections, making them a better choice for organizations wanting faster, more secure remote access.
Questions and Answers
1. Is there something safer than a VPN?
Yes, options such as software-defined perimeters and zero-trust network access provide more secure remote access than VPNs.
2. What can we use instead of a VPN?
Secure alternatives to VPNs include zero trust network access, secure access service edge, software-defined perimeter, software-defined wide area networks, and unified endpoint management tools.
3. Does a VPN actually keep you safe?
While VPNs can offer strong encryption, they are not infallible and may not protect against all online threats.
4. Is Tor over VPN safe?
Using Tor over a VPN can enhance privacy, but it’s important to note that Tor has its limitations and may have potential security risks.
5. Can anything bypass a VPN?
It is possible to bypass a VPN block by switching servers or using a different VPN provider.
6. Is a free VPN better than no VPN?
Using a free VPN may compromise your online security and expose you to potential risks. It is recommended to use a reasonably-priced paid VPN for better protection.
7. What does a VPN not hide?
A VPN masks your IP address and encrypts your internet traffic, but it does not hide the type of device you are using.
8. Can hackers get through a VPN?
While a VPN adds a layer of encryption, it is not invincible to hacking attempts. Premium VPNs have lower chances of being successfully hacked, but vulnerabilities can still exist.
9. Can police track VPN and Tor?
It is generally difficult for police or ISPs to track live, encrypted VPN traffic. However, using Tor could potentially attract suspicion.
10. Can hackers track you on Tor?
While Tor encrypts your internet traffic, malicious actors can still track your activities at the entry and exit nodes of the network.
11. What are the disadvantages of zero trust network?
Implementing a zero trust network can be complex and expensive, requiring significant changes to an organization’s network infrastructure and security policies. It may also increase user frustration and reduce productivity due to multiple authentication requirements.
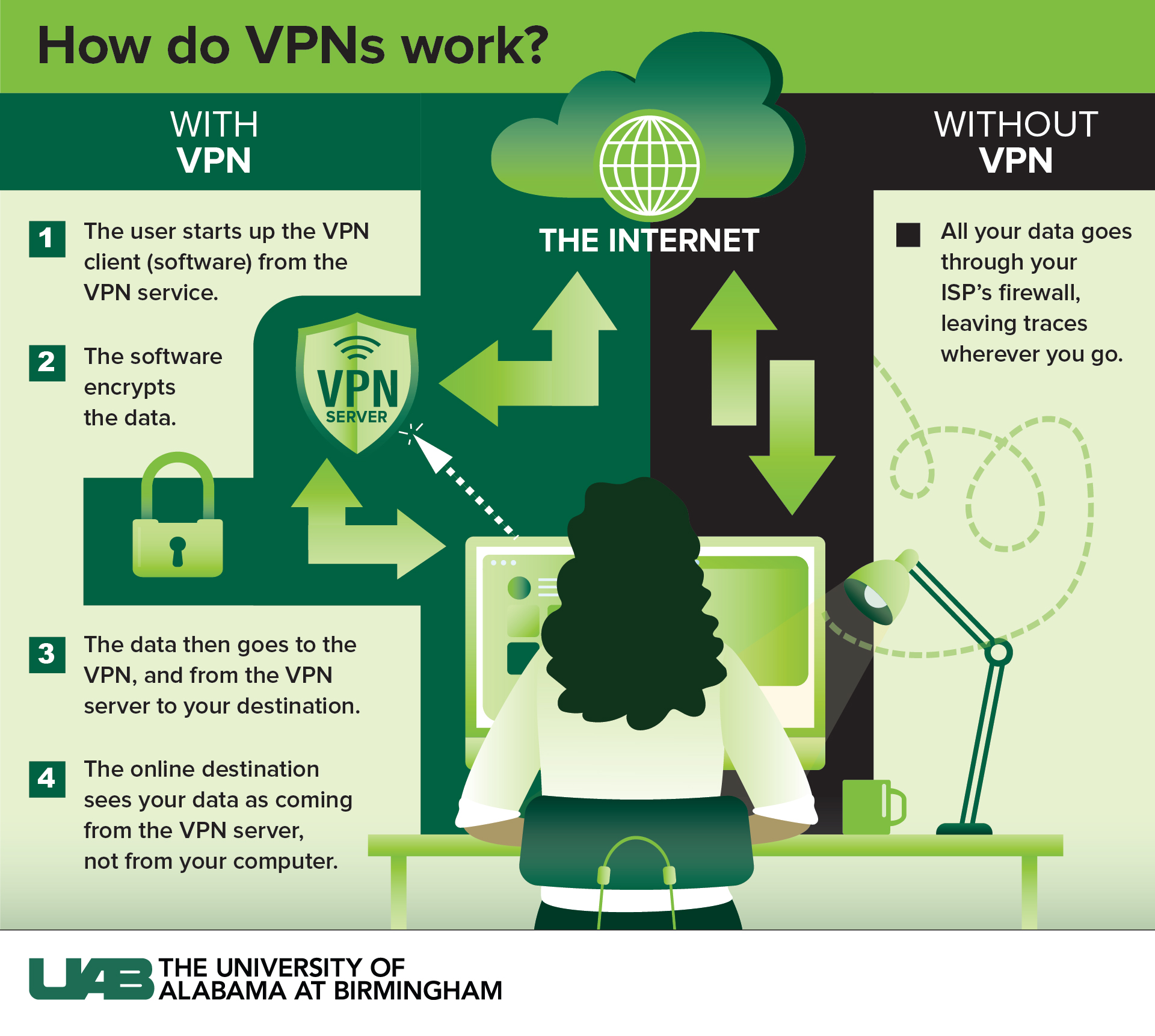
What’s more secure than a VPN
An SDP is a network architecture that implements zero-trust principles to provide more secure remote access than VPNs.
What we can use instead of VPN
Secure alternatives to VPNs for remote working include zero trust network access, secure access service edge (SASE), software-defined perimeter, software-defined wide area networks, and unified endpoint management tools.
Does a VPN actually keep you safe
A VPN may boast strong protocols and military-grade encryption, but it can’t protect against all threats and is only as secure as the company operating it.
Is Tor over VPN safe
Using Tor over a VPN can enhance privacy, but it’s important to understand that Tor has its limitations and potential security risks.
Why zero trust is better than VPN
Zero trust networks offer quicker and more efficient connections compared to VPNs, making them a more suitable choice for secure remote access.
Can Tor be traced
While Tor encrypts your traffic, your ISP can still detect that you’re using Tor, potentially raising suspicion.
Can anything bypass a VPN
A VPN block can sometimes be bypassed by switching servers or using a less popular VPN service.
Is a free VPN better than no VPN
Using a free VPN can compromise your security and privacy, so it’s generally recommended to opt for a reasonably-priced paid option.
What does a VPN not hide
A VPN masks your IP address and encrypts your traffic, but it does not hide information about the device you are using.
Can hackers get through a VPN
A VPN adds a layer of encryption, but it is not invincible to hacking attempts. Premium VPNs offer stronger protection but vulnerabilities can still exist.
Can police track VPN and Tor
Tracking VPN traffic is challenging due to encryption, while Tor usage may raise suspicion without necessarily leading to legal trouble.
Can hackers track you on Tor
While Tor encrypts your traffic, malicious actors can potentially track you at entry and exit nodes of the network.
What are the disadvantages of zero trust network
Implementing a zero trust network can be complex and expensive, and it may lead to user frustration and reduced productivity due to multiple authentication requirements.

What’s more secure than a VPN
An SDP is a network architecture that implements zero-trust principles to provide more secure remote access than VPNs.
What we can use instead of VPN
Secure alternatives to VPNs for remote workingZero trust network access.Secure access service edge (SASE)Software-defined perimeter.Software-defined wide area networks.Identity and access management and privileged access management.Unified endpoint management tools.
Does a VPN actually keep you safe
A VPN may boast strong protocols and military-grade encryption, but that doesn't mean it's infallible. It can't prevent cookie tracking, viruses, or malware, and it can't protect against phishing scams. Data leaks could occur. But most pivotally, a VPN is only as secure as the company that runs it.
Is Tor over VPN safe
Your ISP or government might get suspicious if you're using Tor. To avoid these, you can use Tor over a VPN. The VPN will shield your data on its way to the entry node. Your ISP won't be able to see that you're using Tor – only that you're using a VPN (and good VPNs can obfuscate even that).
Why zero trust is better than VPN
That's because VPNs work by routing all traffic through a data center to then be decrypted. But ultimately this process can take time and result in slow-moving protection. Because zero trust is primarily cloud-based, connections are quick and efficient. (Also read: The Best Practices for Managing Cloud Applications.)
Can Tor be traced
Tor doesn't provide a new IP address when you open the browser, so anyone watching knows you're using Tor and could track your true location. It does encrypt your traffic on most nodes, but it doesn't offer encryption at the exit node. This leaves room for malicious software to creep into your system.
Can anything bypass a VPN
You can often bypass a VPN block by switching servers or going to a different VPN provider. The organization blocking your access may have focused on only the more popular VPNs when choosing what to block, so you may be able to gain access using a less popular service.
Is a free VPN better than no VPN
We don't recommend using a free VPN because it could compromise and even harm your online security by selling your data to third parties and leaving you vulnerable to malware. Instead, we'd suggest using a reasonably-priced paid option, such as NordVPN, to keep your data safe while you're online.
What does a VPN not hide
While a VPN masks your IP address and encrypts your internet traffic, it does not hide the type of device you are using. Websites can still gather device-specific information (including operating system, screen resolution and browser type) through methods like browser fingerprinting.
Can hackers get through a VPN
A VPN is not invincible to hacking attempts. Like any software or service that relies on the internet, a VPN can be vulnerable in various aspects. Nonetheless, premium VPNs have lower chances of being successfully hacked. Their strong encryptions will take millions of years to break.
Can police track VPN and Tor
There is no way to track live, encrypted VPN traffic.
Using the Tor browser could be suspicious to your ISP and, therefore, to the police. However, you're not going to get in trouble just because it looks a bit suspicious.
Can hackers track you on Tor
Although your internet traffic is encrypted on Tor, your ISP can still see that you're connected to Tor. Plus, Tor cannot protect against tracking at the entry and exit nodes of its network. Anyone who owns and operates the entry node will see your real IP address.
What are the disadvantages of zero trust network
It can be expensive and complex to implement, requiring significant changes to the organization's network infrastructure and security policies. Zero-trust security can also increase the risk of user frustration and reduce productivity, as users may need to authenticate multiple times to access different resources.
What are the disadvantages of zero trust in cyber security
Zero Trust Slows Down Application Performance
One of the biggest complaints about Zero Trust is that it can slow down application performance. This is because every user, device, and application must be authenticated and authorized before accessing data or applications.
Can FBI track Tor
Traffic Analysis:
Another way that agencies can track down users on the TOR network is through traffic analysis. This involves analyzing the flow of data through the TOR network to try and identify the location of the user.
Is Tor 100% safe
Tor Browser is safe to use if you're browsing the same sites you would on the “clear web.” But if you browse . onion sites, use caution. Tor's encryption tries to keep your identity and destination secret, but bad actors can still find a way to identify you.
Why is Netflix blocking VPN
In short, Netflix bans VPN connections because they don't have the rights to air certain content in many countries. So when a subscriber uses a Netflix VPN to watch a show that isn't typically available in their region, Netflix is in violation of their copyright agreement.
Can a hacker bypass your VPN
Technically – no. Hackers can't get through standard VPN encryption. A brute force attack would take millions to billions of years to crack the current standard AES-256 encryption. This cipher is known for being essentially impenetrable and is a good choice to keep your online activity safe.
Does anyone really need a VPN
VPN use is important for online privacy whenever you're logging into the internet from a public spot because cyber snoops could track your online activity when you are using public Wi-Fi, whether it's on your computer or your mobile device.
Do any free VPNs actually work
Free VPNs often limit speed, data usage, the number of servers and device connections and hardly unblock streaming sites. But that's not all—no VPN can operate without money, so they tend to make their money in other ways, which often turns out bad for users.
Can you be tracked if you use VPN
A premium quality VPN encrypts data and hides your IP address by routing your activity through a VPN server; even if someone tries to monitor your traffic, all they'll see is the VPN server's IP and complete gibberish. Beyond that, you can only be tracked with information you provide to sites or services you log into.
Can the police track a VPN
With a VPN on, the user's online activities and data are encrypted. But, if the VPN software has security flaws and vulnerabilities, the police (or any other third party, for that matter) can use them to “break into” the VPN and see what data is being sent and received. So technically, the policy could track a VPN.
Can you still be spied on with a VPN
The ISP gives you access to the internet, so they can see the connections you make through their servers. It doesn't mean that there are bold letters proclaiming that you're using a VPN, but based on IP addresses and encrypted traffic, they could, in theory, connect the dots.
Can the FBI track a VPN
Can police track online purchases made with a VPN There is no way to track live, encrypted VPN traffic. That's why police or government agencies who need information about websites you visited have to contact your internet service provider (ISP for short), and only then your VPN provider.
Can the FBI track you on Tor
Traffic Analysis:
Another way that agencies can track down users on the TOR network is through traffic analysis. This involves analyzing the flow of data through the TOR network to try and identify the location of the user.