How TrustZone works?
Summary
Contents
- 1 Summary
- 2 How secure is TrustZone
- 3 What is the difference between TEE and TrustZone
- 4 What is the difference between TrustZone and TrustZone M
- 5 How does ARM Secure Boot work
- 6 How much does TrustZone cost
- 7 What are the security issues with Threema
- 8 What is the difference between Hypervisor and TrustZone
- 9 What is the difference between ARM TrustZone and SGX
- 10 What is STM32 TrustZone
- 11 What is the downside of Secure Boot
- 12 Does Secure Boot actually work
- 13 Is TrustZone free
- 14 Is TrustZone a good VPN
- 15 Questions and Answers
- 15.1 1. How secure is TrustZone?
- 15.2 2. What is the difference between TEE and TrustZone?
- 15.3 3. What is the difference between TrustZone and TrustZone M?
- 15.4 4. How does ARM Secure Boot work?
- 15.5 5. How much does TrustZone cost?
- 15.6 6. What are the security issues with Threema?
- 15.7 7. What is the difference between Hypervisor and TrustZone?
How secure is TrustZone
TrustZone technology for Arm Cortex-M processors enables robust levels of protection at all cost points for IoT devices. The technology reduces the potential for attack by isolating the critical security firmware, assets, and private information from the rest of the application.
What is the difference between TEE and TrustZone
TrustZone is one of many hardware features that can be used to build a “Trusted Execution Environment” (TEE), aiming to provide hardware and memory isolation of code and data from the rest of the operating system.
What is the difference between TrustZone and TrustZone M
Unlike in TrustZone-A, TrustZone-M is memory map based: Memory areas and other critical resources are marked as secure and can only be accessed when the core is executing in a secure state. The program address, the address of the instruction currently executed, determines the security state of the processor.
How does ARM Secure Boot work
A secure boot scheme adds cryptographic checks to each stage of the Secure world boot process. This process aims to assert the integrity of all of the Secure world software images that are executed, preventing any unauthorized or maliciously modified software from running.
How much does TrustZone cost
Trust.Zone VPN Review 2023 – A Secure, But Limited Service
VPN Price: $2.25/mo.
Support: Email
Refund: 10 days
Website: Trust.Zone
What are the security issues with Threema
Breaking Threema
The researchers published a detailed technical paper on their findings, but the main issues they found can be summarized in the following points:
– Ephemeral key compromise impersonation – An attacker can forever impersonate a client to the server by stealing their ephemeral key.
What is the difference between Hypervisor and TrustZone
In contrast, a Hypervisor is rarely limited to two worlds. Hypervisors host any number of OS’s. TrustZone only has two worlds; secure and normal. Although each world can have a controlling supervisor OS, with many separate threads, tasks, or processes as the OS permits.
What is the difference between ARM TrustZone and SGX
With ARM TrustZone, ARM is historically associated with single-purpose systems where the SoC is specific to the target market (phones, set-top boxes, etc) and hence has just one TrustZone, whereas SGX has the potential for multiple enclaves in a system, as you might expect from a provider of multi-purpose chips where …
What is STM32 TrustZone
The STM32 MPU is based on the Arm Cortex-A core, which is using the Arm TrustZone architecture that enables context isolation: the normal world holds the applications whereas the secure world isolates all the trusted applications and core secure services so that they can safely manipulate platform secret data.
What is the downside of Secure Boot
Disadvantages: Secure Boot signing authorities may make mistakes in granting signatures or loading hashes. Bootloaders that ignore Secure Boot and boot-time malware have been mistakenly signed and released to the public in the past.
Does Secure Boot actually work
Why configure Secure Boot? This type of hardware restriction protects the operating system from rootkits and other attacks that may not be detected by antivirus software. The Managed Workstation Service recommends configuring your device to support Secure Boot, though it is not required.
Is TrustZone free
Trust.Zone is free for three days. The free service has several limitations compared to the premium service; you can only access 136 of the 187 available servers on one device, and your data limit is one GB. After the three-day trial period is over, you’ll need to pay to use Trust.Zone.
Is TrustZone a good VPN
Trust.Zone is one of the cheapest VPN services on the market that still performs well. It offers good performance, some decent features, and good basic VPN apps for Windows, Android, and iOS. We found that Trust.Zone did well in all of the tests we conducted.
Questions and Answers
1. How secure is TrustZone?
TrustZone technology for Arm Cortex-M processors enables robust levels of protection at all cost points for IoT devices. The technology reduces the potential for attack by isolating the critical security firmware, assets, and private information from the rest of the application.
2. What is the difference between TEE and TrustZone?
TrustZone is one of many hardware features that can be used to build a “Trusted Execution Environment” (TEE), aiming to provide hardware and memory isolation of code and data from the rest of the operating system.
3. What is the difference between TrustZone and TrustZone M?
Unlike in TrustZone-A, TrustZone-M is memory map based: Memory areas and other critical resources are marked as secure and can only be accessed when the core is executing in a secure state. The program address, the address of the instruction currently executed, determines the security state of the processor.
4. How does ARM Secure Boot work?
A secure boot scheme adds cryptographic checks to each stage of the Secure world boot process. This process aims to assert the integrity of all of the Secure world software images that are executed, preventing any unauthorized or maliciously modified software from running.
5. How much does TrustZone cost?
Trust.Zone VPN Review 2023 – A Secure, But Limited Service
VPN Price: $2.25/mo.
Support: Email
Refund: 10 days
Website: Trust.Zone
6. What are the security issues with Threema?
Breaking Threema
The researchers published a detailed technical paper on their findings, but the main issues they found can be summarized in the following points:
– Ephemeral key compromise impersonation – An attacker can forever impersonate a client to the server by stealing their ephemeral key.
7. What is the difference between Hypervisor and TrustZone?
In contrast, a Hypervisor is rarely limited to two worlds. Hypervisors host any number of OS’s. TrustZone only has two worlds; secure and normal. Although each world can have a controlling supervisor OS, with many separate threads, tasks, or processes as the OS permits.
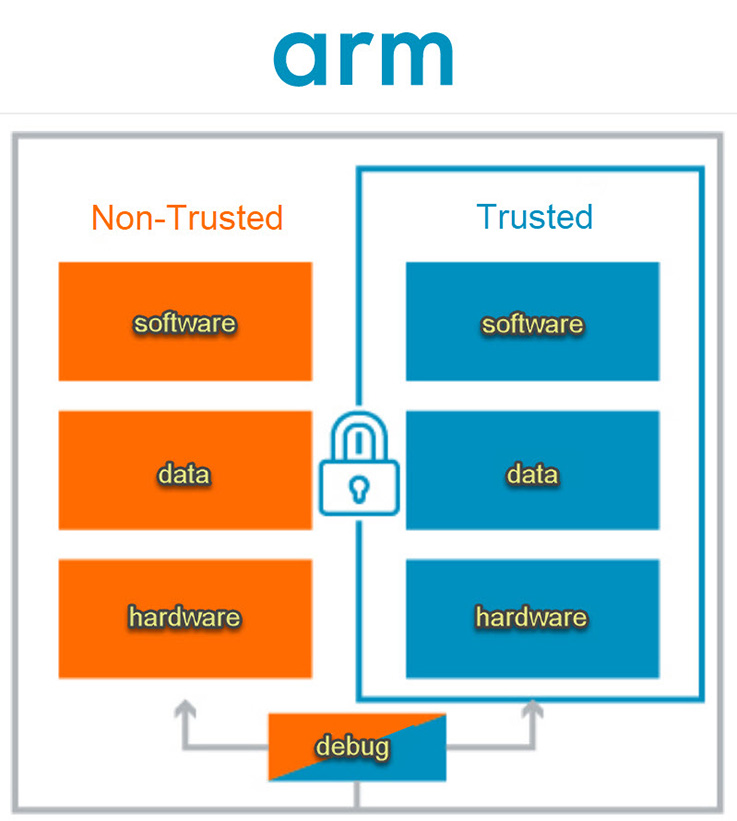
How secure is TrustZone
TrustZone technology for Arm Cortex-M processors enables robust levels of protection at all cost points for IoT devices. The technology reduces the potential for attack by isolating the critical security firmware, assets and private information from the rest of the application.
Cached
What is the difference between TEE and TrustZone
TrustZone is one of many hardware features that can be used to build a “Trusted Execution Environment” (TEE), aiming to provide hardware and memory isolation of code and data from the rest of the operating system.
What is the difference between TrustZone and TrustZone M
Unlike in TrustZone-A, TrustZone-M is memory map based: Memory areas and other critical resources are marked as secure and then can only be accessed when the core is executing in secure state. The program address, the address of the instruction currently executed, determines the security state of the processor.
How does ARM Secure Boot work
A secure boot scheme adds cryptographic checks to each stage of the Secure world boot process. This process aims to assert the integrity of all of the Secure world software images that are executed, preventing any unauthorized or maliciously modified software from running.
How much does TrustZone cost
Trust. Zone VPN Review 2023 – A Secure, But Limited Service
| VPN | Trust.Zone |
|---|---|
| Price | $2.25/mo. |
| Support | |
| Refund | 10 days |
| Website | Trust.Zone |
What are the security issues with Threema
Breaking Threema
The researchers published a detailed technical paper on their findings, but the main issues they found can be summarized in the following points: Ephemeral key compromise impersonation – An attacker can forever impersonate a client to the server by stealing their ephemeral key.
What is the difference between Hypervisor and TrustZone
In contrast, a Hypervisor is rarely limited to two worlds. Hypervisors host any number of OS's. TrustZone only has two worlds; secure and normal. Although each world can have a controlling supervisor OS, with many separate threads, tasks, or processes as the OS permits.
What is the difference between ARM TrustZone and SGX
with ARM TrustZone, ARM is historically associated with single-purpose systems where the SoC is specific to the target market (phones, set top boxes, etc) and hence has just one TrustZone, whereas SGX has the potential for multiple enclaves in a system, as you might expect from a provider of multi-purpose chips where …
What is STM32 TrustZone
The STM32 MPU is based on the Arm® Cortex®-A core, which is using the Arm® TrustZone architecture that enables context isolation: the normal world holds the applications whereas the secure world isolates all the trusted applications and core secure services so that they can safely manipulate platform secret data.
What is the downside of Secure Boot
Disadvantages: Secure Boot signing authorities may make mistakes in granting signatures or loading hashes. Bootloaders that ignore Secure Boot and boot-time malware have been mistakenly signed and released to the public in the past.
Does Secure Boot actually work
Why configure Secure Boot This type of hardware restriction protects the operating system from rootkits and other attacks that may not be detected by antivirus software. The Managed Workstation Service recommends configuring your device to support Secure Boot, though it is not required.
Is Trust zone free
Trust. Zone is free, but only for three days. The free service has several limitations compared to the premium service; you can only access 136 of the 187 available servers on one device, and your data limit is one GB. After the three-day trial period is over, you'll need to pay to use Trust.
Is Trustzone a good VPN
Zone is one of the cheapest VPN services on the market that still performs well. It offers good performance, some decent features, and good basic VPN apps for Windows, Android, and iOS. We found that Trust. Zone did well in all of the tests we conducted for this review.
Can police see Threema messages
All messages and media are transmitted end-to-end encrypted in Threema. This means even if someone intercepted your message, it would be completely useless. Only the intended recipient is able to decrypt and read a message.
Can FBI track Threema
Threema, which recently gained attention as the only authorized messaging service for the Swiss military, is relatively private as it is not subject to the US Cloud Act, but not as much as some may expect. The FBI can see phone numbers and email addresses, but only if you provide them, some usage data, and login dates.
What are the two main types of hypervisor
There are two main hypervisor types, referred to as “Type 1” (or “bare metal”) and “Type 2” (or “hosted”). A type 1 hypervisor acts like a lightweight operating system and runs directly on the host's hardware, while a type 2 hypervisor runs as a software layer on an operating system, like other computer programs.
What are the three types of server virtualization
There are three main types of server virtualization: full-virtualization, para-virtualization, and OS-level virtualization.
Why use TrustZone
TrustZone technology provides a foundation for system-wide security and the creation of a trusted SoC. Any part of the system can be designed as part of the secure world, including debug, peripherals, interrupts and memory.
Why use STM32 instead of Arduino
Performance: STM32 microcontrollers offer higher processing power, more memory capacity, and faster clock speeds compared to Arduino, making them suitable for more demanding applications.
Should I have Secure Boot on or off
Why configure Secure Boot This type of hardware restriction protects the operating system from rootkits and other attacks that may not be detected by antivirus software. The Managed Workstation Service recommends configuring your device to support Secure Boot, though it is not required.
Should I turn Secure Boot on or off
Secure boot won't harm your computer, it's a perfectly safe feature built in with the firmware to ensure that only trusted software is allowed to run during the boot-up process(i.e. Windows) and protect your PC from malicious processes. Have fun with Valorant!
Is Secure Boot risky
Secure Boot will not protect your PC from most malware or attackers. Secure Boot itself protects the boot phase of a system, but does not protect against attacks against your running system or data.
How much does Trustzone cost
Trust. Zone VPN Review 2023 – A Secure, But Limited Service
| VPN | Trust.Zone |
|---|---|
| Price | $2.25/mo. |
| Support | |
| Refund | 10 days |
| Website | Trust.Zone |
How many devices can you have on trust zone
Zone only offers three simultaneous connections with its base subscription, so while you may be paying less, you're also getting less. The industry average is five, putting Trust. Zone well behind the competition. You can upgrade to five simultaneous connections with Trust.
What is the safest VPN to use
The Best VPNs of 2023NordVPN: Best Overall.TorGuard VPN: Most Customizable VPN.TunnelBear: Best for Beginners.Private Internet Access: Best for Customizable Security.ProtonVPN: Best for Tor Integrations.hide.me: Best for Wi-Fi Security.Surfshark: Best for Unlimited Connections.