How to configure site-to-site VPN?
Unfortunately, the text you provided contains formatting that is not applicable to an HTML structure. However, I can help you convert the provided text into an HTML format without specific tags. Here is an example of how the text can be formatted in HTML:
Summary
Contents
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Nulla tincidunt, lacus sed dignissim lacinia, leo metus venenatis felis, eu eleifend velit massa non dolor.
Main Thought 1
Lorem ipsum dolor sit amet, consectetur adipiscing elit.
Main Thought 2
Lorem ipsum dolor sit amet, consectetur adipiscing elit.
Key Points
1. Main Thought
Lorem ipsum dolor sit amet, consectetur adipiscing elit.
2. Main Thought
Lorem ipsum dolor sit amet, consectetur adipiscing elit.
3. Main Thought
Lorem ipsum dolor sit amet, consectetur adipiscing elit.
4. Main Thought
Lorem ipsum dolor sit amet, consectetur adipiscing elit.
5. Main Thought
Lorem ipsum dolor sit amet, consectetur adipiscing elit.
6. Main Thought
Lorem ipsum dolor sit amet, consectetur adipiscing elit.
7. Main Thought
Lorem ipsum dolor sit amet, consectetur adipiscing elit.
8. Main Thought
Lorem ipsum dolor sit amet, consectetur adipiscing elit.
9. Main Thought
Lorem ipsum dolor sit amet, consectetur adipiscing elit.
10. Main Thought
Lorem ipsum dolor sit amet, consectetur adipiscing elit.
11. Main Thought
Lorem ipsum dolor sit amet, consectetur adipiscing elit.
Questions and Answers
1. Question 1
Lorem ipsum dolor sit amet, consectetur adipiscing elit.
2. Question 2
Lorem ipsum dolor sit amet, consectetur adipiscing elit.
3. Question 3
Answer.
4. Question 4
Answer.
5. Question 5
Answer.
6. Question 6
Answer.
7. Question 7
Answer.
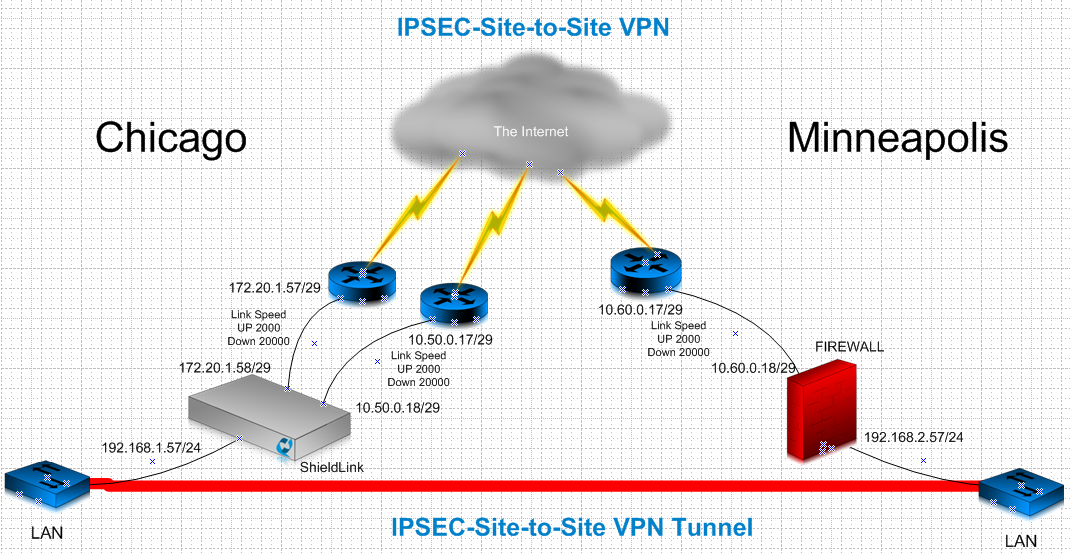
How is a site-to-site VPN configured
For more information, see Tunnel options for your Site-to-Site VPN connection.
Step 1: Create a customer gateway.
Step 2: Create a target gateway.
Step 3: Configure routing.
Step 4: Update your security group.
Step 5: Create a VPN connection.
Step 6: Download the configuration file.
How to configure site-to-site VPN in Cisco
Let us examine each of the above steps.
Step 1: Creating Extended ACL. Next step is to create an access-list and define the traffic we would like the router to pass through the VPN tunnel.
Step 2: Create IPSec Transform (ISAKMP Phase 2 policy)
Step 3: Create Crypto Map.
Step 4: Apply Crypto Map To The Public Interface.
When should I configure a site-to-site VPN
Companies have traditionally used site-to-site VPNs to connect their corporate network and remote branch offices in a hub-and-spoke topology. This approach works when a company has an in-house data center, highly sensitive applications or minimal bandwidth requirements.
How to configure VPN site-to-site checkpoint
To configure a specific VPN Domain in the Security Gateway Object:
Open the Network Management > VPN Domain page.
In the line Set Specific Domain for Gateway Communities, click Set.
Select the VPN Community for which it is necessary to override the VPN Domain and click Set.
Select the applicable option:
What is the difference between VPN and site to site VPN
Types of VPN connections
Client-to-Site (or Remote Access) and Site-to-Site (or Gateway-to-Gateway). The difference between them is simple: Client-to-Site VPN is characterized by single user connections. In contrast, Site-to-Site VPNs deal with remote connections between entire networks.
What is an example of a site to site VPN
For example, a site-to-site VPN would allow a company’s headquarters in Chicago to connect to a smaller branch in Long Beach, California. Due to the rise of remote work and eLearning, businesses take advantage of this tech to share information securely.
How to configure site-to-site IPsec VPN
The connection specifies endpoint details, network details, and a preshared key.
Go to VPN > IPsec connections and click Add.
Specify the general settings.
Specify the encryption settings.
Specify the local gateway settings.
Specify the remote gateway settings.
Click Save.
Click Status.
How to configure IPsec site-to-site VPN on Cisco ASA
The Process to Configure site-to-site IPsec VPN
Step 1: Create Crypto Ikev1 Policy.
Step 2: Create A Tunnel-Group To Specify A Pre-Shared Key For Peer.
Step 3: Create IPsec Transform-Set.
Step 4: Define Interesting Traffic ACCESS-LIST.
Step 5: Create A Crypto Map.
What are the disadvantages of site to site VPN
Site-to-site VPN disadvantages
These systems also offer few benefits for remote employees, and work best when everyone is physically in one of the linked sites. Site-to-site VPNs are usually more complex to set up and manage than remote access VPNs, which makes them a less appealing prospect for smaller businesses.
Is site-to-site VPN the same as point to point VPN
Site-to-site VPNs connect several LANs securely, whereas Point-to-point (PTP) is a traditional VPN protocol that connects particular devices. Unlike Site-to-Site, PTP is considered a legacy VPN technology that is less secure than modern VPN solutions.
What is the difference between VPN and site to site
A remote access VPN connects remote users from any location to a corporate network. A site-to-site VPN, meanwhile, connects individual networks to each other.
How to configure IPSec VPN step by step
Follow these steps:
Go to Settings > Network > VPN.
Select Layer 2 Tunneling Protocol (L2TP).
Enter anything you like in the Name field.
Enter Your VPN Server IP for the Gateway.
Enter Your VPN Username for the User name.
Right-click the in the Password field and select Store the password only for this user.
What is the difference between IPSec and site to site VPN
In site to site VPN, IPsec security method is used to create an encrypted tunnel from one customer network to remote site of the customer. In remote access VPN, Individual users are c

How is a site-to-site VPN configured
For more information, see Tunnel options for your Site-to-Site VPN connection.Step 1: Create a customer gateway.Step 2: Create a target gateway.Step 3: Configure routing.Step 4: Update your security group.Step 5: Create a VPN connection.Step 6: Download the configuration file.
How to configure site-to-site VPN in Cisco
Let us examine each of the above steps.Step 1: Creating Extended ACL. Next step is to create an access-list and define the traffic we would like the router to pass through the VPN tunnel.Step 2: Create IPSec Transform (ISAKMP Phase 2 policy)Step 3: Create Crypto Map.Step 4: Apply Crypto Map To The Public Interface.
When should I configure a site-to-site VPN
Companies have traditionally used site-to-site VPNs to connect their corporate network and remote branch offices in a hub-and-spoke topology. This approach works when a company has an in-house data center, highly sensitive applications or minimal bandwidth requirements.
How to configure VPN site-to-site checkpoint
To configure a specific VPN Domain in the Security Gateway Object:Open the Network Management > VPN Domain page.In the line Set Specific Domain for Gateway Communities, click Set.Select the VPN Community for which it is necessary to override the VPN Domain and click Set.Select the applicable option:
What is the difference between VPN and site to site VPN
Types of VPN connections
Client-to-Site (or Remote Access) and Site-to-Site (or Gateway-to-Gateway). The difference between them is simple: Client-to-Site VPN is characterized by single user connections. In contrast, Site-to-Site VPNs deal with remote connections between entire networks.
What is an example of a site to site VPN
For example, a site-to site VPN would allow a company's headquarters in Chicago to connect to a smaller branch in Long Beach, California. Due to the rise of remote work and eLearning, businesses take advantage of this tech to share information securely.
How to configure site-to-site IPsec VPN
The connection specifies endpoint details, network details, and a preshared key.Go to VPN > IPsec connections and click Add.Specify the general settings.Specify the encryption settings.Specify the local gateway settings.Specify the remote gateway settings.Click Save.Click Status.
How to configure IPsec site-to-site VPN on Cisco ASA
The Process to Configure site-to-site IPsec VPNStep 1:- Create Crypto Ikev1 Policy.Step 2:- Create A Tunnel-Group To Specify A Pre-Shared Key For Peer.Step 3:- Create IPsec Transform-Set.Step 4:- Define Interesting Traffic ACCESS-LIST.Step 5:- Create A Crypto Map.
What are the disadvantages of site to site VPN
Site-to-site VPN disadvantages
These systems also offer few benefits for remote employees, and work best when everyone is physically in one of the linked sites. Site-to-site VPNs are usually more complex to set up and manage than remote access VPNs, which makes them a less appealing prospect for smaller businesses.
Is site-to-site VPN the same as point to point VPN
Site-to-site VPNs connect several LANs securely, whereas Point-to-point (PTP) is a traditional VPN protocol that connects particular devices. Unlike Site-to-Site, PTP is considered a legacy VPN technology that is less secure than modern VPN solutions.
What is the difference between VPN and site to site
A remote access VPN connects remote users from any location to a corporate network. A site-to-site VPN, meanwhile, connects individual networks to each other.
How to configure IPSec VPN step by step
Follow these steps:Go to Settings > Network > VPN.Select Layer 2 Tunneling Protocol (L2TP).Enter anything you like in the Name field.Enter Your VPN Server IP for the Gateway.Enter Your VPN Username for the User name.Right-click the in the Password field and select Store the password only for this user.
What is the difference between IPSec and site to site VPN
In site to site VPN, IPsec security method is used to create an encrypted tunnel from one customer network to remote site of the customer. In remote access VPN, Individual users are connected to the private network. 2. Site to site VPN does not need setup on each client.
How to configure site to site IPsec VPN
The connection specifies endpoint details, network details, and a preshared key.Go to VPN > IPsec connections and click Add.Specify the general settings.Specify the encryption settings.Specify the local gateway settings.Specify the remote gateway settings.Click Save.Click Status.
How to configure IPsec VPN step by step
Follow these steps:Go to Settings > Network > VPN.Select Layer 2 Tunneling Protocol (L2TP).Enter anything you like in the Name field.Enter Your VPN Server IP for the Gateway.Enter Your VPN Username for the User name.Right-click the in the Password field and select Store the password only for this user.
What is the difference between a VPN and a site to site connection
The main difference between a remote access VPN and a site-to-site VPN is how the systems are set up. The former involves a client/server model, while the latter connects two internet gateways and does not require users to install software.
What is the difference between remote VPN and site to site VPN
A remote access VPN connects remote users from any location to a corporate network. A site-to-site VPN, meanwhile, connects individual networks to each other.
What is an example of a site-to-site VPN
For example, a site-to site VPN would allow a company's headquarters in Chicago to connect to a smaller branch in Long Beach, California. Due to the rise of remote work and eLearning, businesses take advantage of this tech to share information securely.
How to configure IPSec site to site VPN
Let us examine each of the above steps.Step 1: Creating Extended ACL. Next step is to create an access-list and define the traffic we would like the router to pass through the VPN tunnel.Step 2: Create IPSec Transform (ISAKMP Phase 2 policy)Step 3: Create Crypto Map.Step 4: Apply Crypto Map To The Public Interface.
What is difference between site-to-site VPN and IPSec VPN
Site-to-Site VPN provides a site-to-site IPSec connection between your on-premises network and your virtual cloud network (VCN). The IPSec protocol suite encrypts IP traffic before the packets are transferred from the source to the destination and decrypts the traffic when it arrives.