How does TrustZone work?
Summary
This article will discuss the topic of TrustZone technology and its usage in the world of Arm processors. We will explore how TrustZone works, its benefits, and its role in creating a trusted system-on-a-chip (SoC). Additionally, we will address common questions about TrustZone, such as the difference between TrustZone and a Trusted Execution Environment (TEE), the security of TrustZone, and its use in Android devices.
Main Thought
TrustZone technology is a vital component of Arm Cortex-A processors, providing a secure world and a non-secure world for software. The switch between these worlds is managed by a secure monitor. This technology is widely used to protect valuable code and data on billions of applications processors worldwide.
Key Points
1. TrustZone provides a foundation for system-wide security and the creation of a trusted SoC. It allows any part of the system to be designed as part of the secure world, including peripherals, interrupts, and memory.
2. TrustZone is one of many hardware features that can be used to build a Trusted Execution Environment (TEE), ensuring code and data isolation from the rest of the operating system.
3. Unlike TrustZone-A, TrustZone-M operates on a memory map basis. Memory areas and critical resources can only be accessed when the core is executing in a secure state, determined by the program address.
4. TrustZone technology for Arm Cortex-M processors enables robust protection for IoT devices, isolating critical security firmware, assets, and private information from the rest of the application.
5. TrustZone is a hardware-based security feature present in every modern ARM processor. It provides support for creating a secure environment to protect private assets in Android systems.
6. TrustZone expands the standard “Exception Level” privilege model for the CPU, introducing an additional EL3 level (secure monitor mode) that controls the entire system.
Questions and Answers
1. How does arm TrustZone work?
Arm TrustZone technology ensures the separation of software into the secure and non-secure worlds within Cortex-A processors. A secure monitor facilitates the switching between these worlds.
2. What is the use of TrustZone?
TrustZone technology forms the foundation for system-wide security and the creation of a trusted SoC. It can secure any part of the system, including peripherals, interrupts, and memory.
3. What is the difference between TEE and TrustZone?
TrustZone is a hardware feature that can be used to build a Trusted Execution Environment (TEE). TEE aims to provide hardware and memory isolation of code and data from the rest of the operating system.
4. What is the difference between TrustZone and TrustZone M?
TrustZone-M operates on a memory map basis, marking specific memory areas and resources as secure. Access to these areas is only granted when the core is executing in a secure state. TrustZone-A does not operate in this manner.
5. How secure is TrustZone?
TrustZone technology for Arm Cortex-M processors provides robust protection for IoT devices, isolating critical security firmware, assets, and private information from the rest of the application.
6. Is TrustZone safe?
TrustZone is a hardware-based security feature built into ARM processors and is not directly related to a VPN service. The security and safety of TrustZone depend on its implementation in various devices.
7. What is the use of TrustZone in Android?
In Android devices, TrustZone technology provides a hardware-based security feature used to create a secure environment for private assets.
8. Is TrustZone a TEE?
TrustZone is one of many hardware features that can be used to build a Trusted Execution Environment (TEE). However, not all TEEs utilize TrustZone technology.
9. What are the exception levels in TrustZone?
TrustZone expands the standard “Exception Level” privilege model for the CPU, including EL3 (secure monitor mode), which controls the entire system.
10. How much does TrustZone cost?
TrustZone is a VPN service that offers different pricing plans. Please refer to the official website for up-to-date pricing information.
11. What is the most secure network transmission?
Fiber-based networks are generally considered the most secure due to the difficulty of tapping into the physical fiber cables. However, the security of a network transmission depends on various factors and technologies employed.
12. Is TrustZone a good VPN?
TrustZone offers good performance, features, and VPN apps for different platforms. However, it is essential to evaluate the specific VPN service based on individual needs and requirements.
13. How many devices can you have on TrustZone?
TrustZone VPN’s base subscription allows three simultaneous connections. However, this may vary depending on the specific subscription plan and provider.
14. What is Samsung Trust Zone?
Samsung TrustZone refers to the implementation of TrustZone technology in Samsung devices, providing a secure environment for protecting sensitive data and assets.
With the provided HTML format, this article can be structured and presented effectively while maintaining a personal, informative tone.
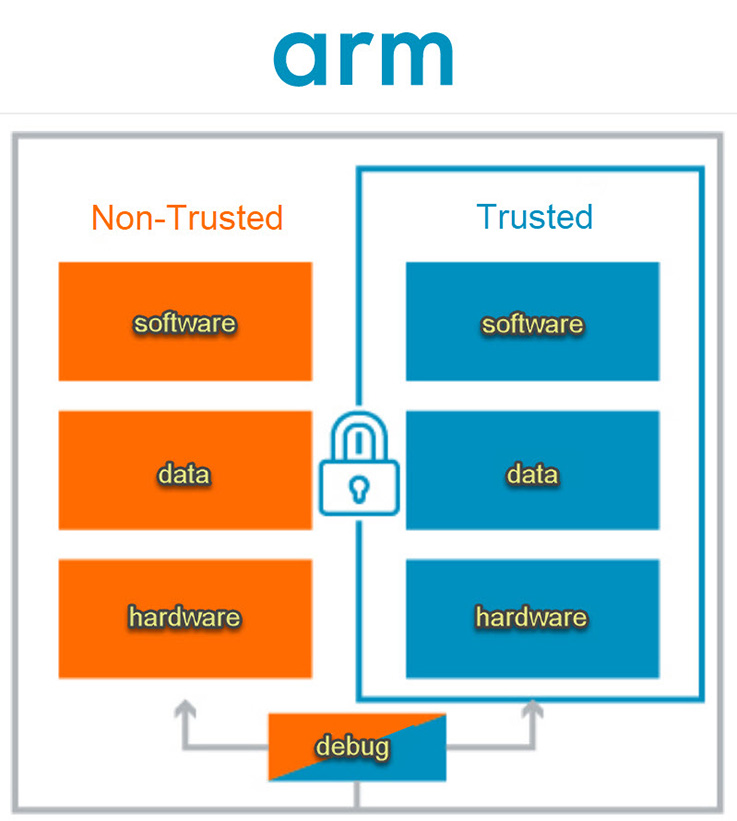
How does arm TrustZone work
Arm TrustZone technology is used on billions of applications processors to protect high-value code and data. Within Arm Cortex-A processors, software either resides in the secure world or the non-secure world; a switch between the two is accomplished via software referred to as the secure monitor.
Cached
What is the use of TrustZone
TrustZone technology provides a foundation for system-wide security and the creation of a trusted SoC. Any part of the system can be designed as part of the secure world, including debug, peripherals, interrupts and memory.
Cached
What is the difference between TEE and TrustZone
TrustZone is one of many hardware features that can be used to build a “Trusted Execution Environment” (TEE), aiming to provide hardware and memory isolation of code and data from the rest of the operating system.
What is the difference between TrustZone and TrustZone M
Unlike in TrustZone-A, TrustZone-M is memory map based: Memory areas and other critical resources are marked as secure and then can only be accessed when the core is executing in secure state. The program address, the address of the instruction currently executed, determines the security state of the processor.
How secure is TrustZone
TrustZone technology for Arm Cortex-M processors enables robust levels of protection at all cost points for IoT devices. The technology reduces the potential for attack by isolating the critical security firmware, assets and private information from the rest of the application.
Is Trust zone safe
zone is a basic VPN located in the Seychelles Islands. It has 178+ servers in 96 countries and supports the OpenVPN tunneling protocol. Additionally, it uses AES-256 encryption and doesn't keep any logs. So, in terms of privacy, you can be sure that your sensitive data is safe.
What is the use of TrustZone in Android
TrustZone is a hardware-based security feature built into every modern ARM processor. Using TrustZone, you have hardware support for creating a separated secure environment to place and use in your private assets.
Is TrustZone a TEE
TrustZone is one of many hardware features that can be used to build a “Trusted Execution Environment” (TEE), aiming to provide hardware and memory isolation of code and data from the rest of the operating system. Not all TEEs use TrustZone.
What are the exception levels in TrustZone
TrustZone also expands the standard “Exception Level” privilege model for the CPU. Before TrustZone, three levels existed: EL0 (user-mode), EL1 (kernel-mode) and EL2 (hypervisor-mode). TrustZone adds a new EL3 (secure monitor mode), which is the most privileged level and controls the entire system.
How much does TrustZone cost
Trust. Zone VPN Review 2023 – A Secure, But Limited Service
| VPN | Trust.Zone |
|---|---|
| Price | $2.25/mo. |
| Support | |
| Refund | 10 days |
| Website | Trust.Zone |
What is the most secure network transmission
There are three broad categories of media: Wire, fiber and wireless. On a very high level, it could be said that fiber is the most secure as it is the hardest to tap. Cable is a little more secure, as physical access is not hard to tap and sniff the passing traffic.
Is TrustZone a good VPN
Zone is one of the cheapest VPN services on the market that still performs well. It offers good performance, some decent features, and good basic VPN apps for Windows, Android, and iOS. We found that Trust. Zone did well in all of the tests we conducted for this review.
How many devices can you have on trust zone
Zone only offers three simultaneous connections with its base subscription, so while you may be paying less, you're also getting less. The industry average is five, putting Trust. Zone well behind the competition. You can upgrade to five simultaneous connections with Trust.
What is Samsung Trust Zone
Generally, TrustZone is used to access hardware-backed features and to perform sensitive operations in a supervised manner (e.g. cryptographic engine, credentials storage, etc.). Samsung heavily uses TrustZone for Samsung Knox, a system-wide security toolbox developed by Samsung.
What is TrustZone VPN
Trust. zone is a basic VPN located in the Seychelles Islands. It has 178+ servers in 96 countries and supports the OpenVPN tunneling protocol. Additionally, it uses AES-256 encryption and doesn't keep any logs. So, in terms of privacy, you can be sure that your sensitive data is safe.
What is the difference between trusted platform module and TEE
TPM is physically isolated from the rest of the system (i.e. it is a standalone chip on the mainboard), while TEE is a secure area of the main CPU. The key function of both TPM and TEE is to do cryptographic calculations, but can they also store credentials/keys used in these calculations
What are the three exception classes
In short, all exceptions are not created equal and therefore there are several types for a programmer to think about. An exception is an event which causes the program to be unable to flow in its intended execution. There are three types of exception—the checked exception, the error and the runtime exception.
Is Trust zone good
zone is a good VPN service. However, it's good as long as you need to become more secure online. This VPN uses advanced encryption, has a kill switch, and it's possible to use the WireGuard tunnel.
Which network is most difficult to secure
Security – A wireless network is less secure than a wired network. Wireless networks must be secured correctly as accessing a wireless network can be done discreetly and does not require physical access to a building.
Which network has the strongest security
WEP, WPA, WPA2 and WPA3: Which is best When choosing from among WEP, WPA, WPA2 and WPA3 wireless security protocols, experts agree WPA3 is best for Wi-Fi security. As the most up-to-date wireless encryption protocol, WPA3 is the most secure choice.
What is the safest VPN to use
The Best VPNs of 2023NordVPN: Best Overall.TorGuard VPN: Most Customizable VPN.TunnelBear: Best for Beginners.Private Internet Access: Best for Customizable Security.ProtonVPN: Best for Tor Integrations.hide.me: Best for Wi-Fi Security.Surfshark: Best for Unlimited Connections.
Is Trust zone VPN free
Trust. Zone is free, but only for three days. The free service has several limitations compared to the premium service; you can only access 136 of the 187 available servers on one device, and your data limit is one GB. After the three-day trial period is over, you'll need to pay to use Trust.
Can I have the same trust wallet on 2 devices
There is no limit to the number of mobile and desktop devices you can access your wallet from, however each will use a separate PIN (unless you intentionally set them to be the same). To use your wallet on an additional device, simply restore your wallet on that device using your recovery phrase backup.
What are trust zones
The trust zone is assigned to the internal local area network [LAN] and the untrust zone is assigned to the Internet. The name of the zone is arbitrary, but is used to help the administrator determine what the zone is used for. Security zones are a key component in policy configuration.
Is Trust Zone VPN legit
zone is a good VPN service. However, it's good as long as you need to become more secure online. This VPN uses advanced encryption, has a kill switch, and it's possible to use the WireGuard tunnel.