How does TLS tunnel VPN work?
Summary
Contents
- 1 Summary
- 2 Personal Experience with TLS Tunnel VPN
- 3 TLS Tunnel VPN: Not a Good Protocol
- 4 The Difference Between TLS and VPN Tunnel
- 5 What is the TLS Tunnel
- 6 How TLS Works Step by Step
- 7 Are VPN Tunnels Legal?
- 8 The Safest VPN to Use
- 9 What Port Does a TLS VPN Typically Use?
- 10 The Two Main Types of VPN Tunnels
- 11 The Difference Between SSL and Tunnel
- 12 What Network Layer is TLS SSL Tunneling Done?
- 13 The 4 Protocols in TLS
- 14 How Does TLS Communicate Between Client and Server
- 15 Can the Government Track You When Using a VPN?
- 16 Can Police Get Around VPN?
- 17 Questions and Answers
- 17.1 1. Is TLS Tunnel VPN safe?
- 17.2 2. What is the difference between TLS and VPN tunnel?
- 17.3 3. What is the TLS tunnel?
- 17.4 4. How does TLS work step by step?
- 17.5 5. Are VPN tunnels legal?
- 17.6 6. What is the safest VPN to use?
- 17.7 7. What port does a TLS VPN typically use?
- 17.8 8. Which are the two main types of VPN tunnels?
- 17.9 9. What is the difference between SSL and tunnel?
- 17.10 10. What network layer is TLS SSL tunneling done?
- 17.11 11. What are the 4 protocols in TLS?
- 17.12 12. How does TLS communicate between client and server?
- 17.13 13. Can the government still track you if you use a VPN?
- 17.14 14. Can police get around VPN?
Personal Experience with TLS Tunnel VPN
TLS Tunnel VPN: Not a Good Protocol
Lorem ipsum dolor sit amet, consectetur adipiscing elit.
The Difference Between TLS and VPN Tunnel
Lorem ipsum dolor sit amet, consectetur adipiscing elit.
What is the TLS Tunnel
Lorem ipsum dolor sit amet, consectetur adipiscing elit.
How TLS Works Step by Step
Lorem ipsum dolor sit amet, consectetur adipiscing elit.
Are VPN Tunnels Legal?
Lorem ipsum dolor sit amet, consectetur adipiscing elit.
The Safest VPN to Use
Lorem ipsum dolor sit amet, consectetur adipiscing elit.
What Port Does a TLS VPN Typically Use?
Lorem ipsum dolor sit amet, consectetur adipiscing elit.
The Two Main Types of VPN Tunnels
Lorem ipsum dolor sit amet, consectetur adipiscing elit.
The Difference Between SSL and Tunnel
Lorem ipsum dolor sit amet, consectetur adipiscing elit.
What Network Layer is TLS SSL Tunneling Done?
Lorem ipsum dolor sit amet, consectetur adipiscing elit.
The 4 Protocols in TLS
Lorem ipsum dolor sit amet, consectetur adipiscing elit.
How Does TLS Communicate Between Client and Server
Lorem ipsum dolor sit amet, consectetur adipiscing elit.
Can the Government Track You When Using a VPN?
Lorem ipsum dolor sit amet, consectetur adipiscing elit.
Can Police Get Around VPN?
Lorem ipsum dolor sit amet, consectetur adipiscing elit.
Questions and Answers
1. Is TLS Tunnel VPN safe?
2. What is the difference between TLS and VPN tunnel?
3. What is the TLS tunnel?
Answer
4. How does TLS work step by step?
Answer
5. Are VPN tunnels legal?
Answer
6. What is the safest VPN to use?
Answer
7. What port does a TLS VPN typically use?
Answer
8. Which are the two main types of VPN tunnels?
Answer
9. What is the difference between SSL and tunnel?
Answer
10. What network layer is TLS SSL tunneling done?
Answer
11. What are the 4 protocols in TLS?
Answer
12. How does TLS communicate between client and server?
Answer
13. Can the government still track you if you use a VPN?
Answer
14. Can police get around VPN?
Answer
Is TLS tunnel VPN safe
It's not a good protocol!
if you use a VPN Tunnel, and “No!”, if you use HTTPS. The SSL/TLS tunnel is one of the weakest areas within computer security, as it only protects data as it goes from machine to machine, and does little to protect a proxy being setup on either end of the tunnel.
What is the difference between TLS and VPN tunnel
In other words, IPsec VPNs connect hosts or networks to a protected private network, while SSL/TLS VPNs securely connect a user's application session to services inside a protected network. IPsec VPNs can support all IP-based applications.
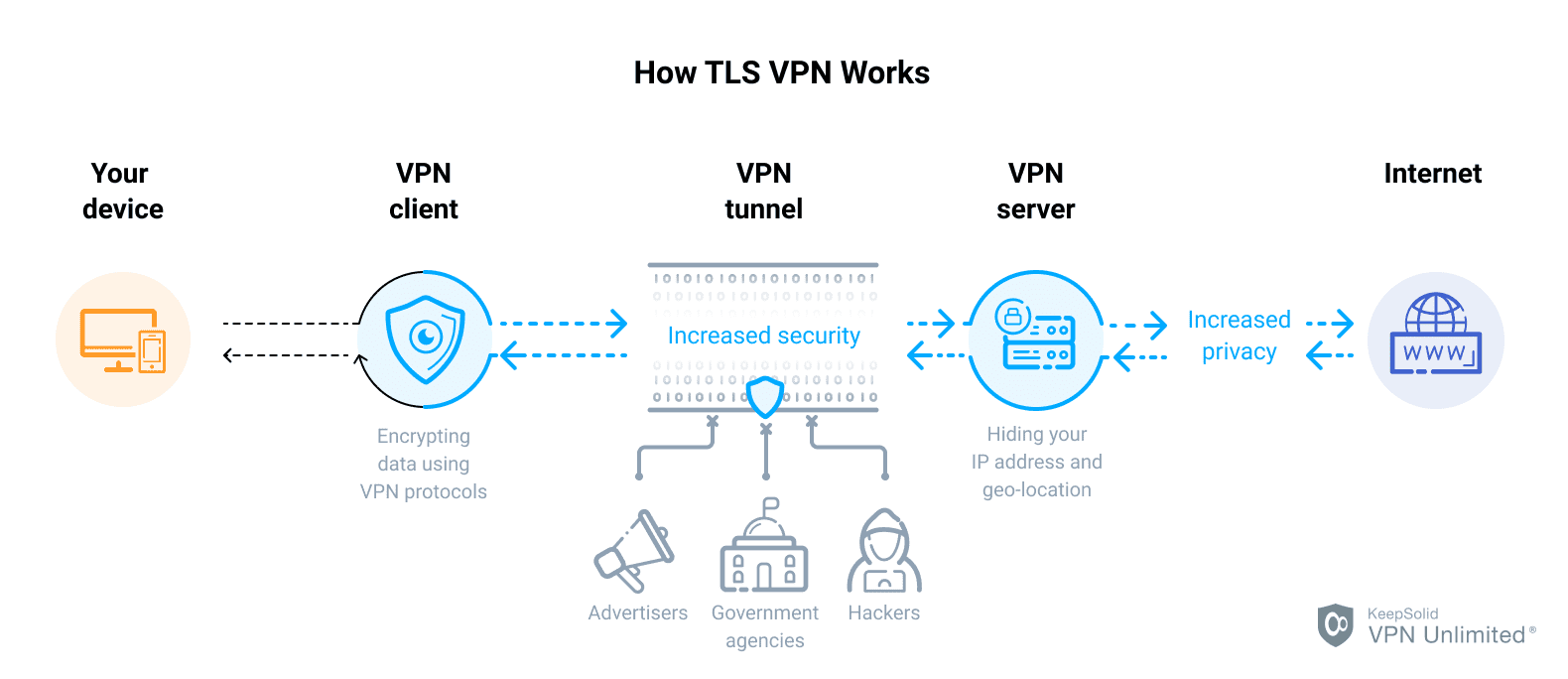
What is the TLS tunnel
Transport Layer Security (TLS) encrypts data sent over the Internet to ensure that eavesdroppers and hackers are unable to see what you transmit which is particularly useful for private and sensitive information such as passwords, credit card numbers, and personal correspondence.
Cached
How TLS works step by step
TLDR: SSL/TLS encrypts communications between a client and server, primarily web browsers and web sites/applications.The client contacts the server using a secure URL (HTTPS…).The server sends the client its certificate and public key.
Are VPN tunnels legal
While it's perfectly legal to use a VPN in most of the world, some countries have specific bans or restrictions. Countries with heavily-restricted network access generally don't want their citizens accessing the open internet with a VPN.
What is the safest VPN to use
The Best VPNs of 2023NordVPN: Best Overall.TorGuard VPN: Most Customizable VPN.TunnelBear: Best for Beginners.Private Internet Access: Best for Customizable Security.ProtonVPN: Best for Tor Integrations.hide.me: Best for Wi-Fi Security.Surfshark: Best for Unlimited Connections.
What port does a TLS VPN typically use
TCP port 443
The default protocol and port for Mobile VPN with SSL is TCP port 443, which is usually open on most networks.
Which are the two main types of VPN tunnels
Types of VPNsSite-to-Site VPN: A site-to-site VPN is designed to securely connect two geographically-distributed sites.Remote Access VPN: A remote access VPN is designed to link remote users securely to a corporate network.
What is the difference between SSL and tunnel
An SSH tunnel encrypts data transmitted between a client and server using a secure “tunnel.” In contrast, an SSL tunnel encrypts data transmitted between a client and server using SSL/TLS protocol. An SSH tunnel uses public key authentication or password authentication for access control.
What network layer is TLS SSL tunneling done
-SSL/TLS can arguably be called a Transport protocol for the "application data" that the webbrowser is trying to display to the end-user. This puts it at around Layer 6-7 depending on how you want to argue for "presentation" vs "application" layer.
What are the 4 protocols in TLS
The TLS and SSL protocols can be divided into two layers. The first layer consists of the application protocol and the three handshaking protocols: the handshake protocol, the change cipher spec protocol, and the alert protocol. The second layer is the record protocol.
How does TLS communicate between client and server
The TLS client sends the server a finished message, which is encrypted with the secret key, indicating that the client part of the handshake is complete. The TLS server sends the client a finished message, which is encrypted with the secret key, indicating that the server part of the handshake is complete.
Can the government still track you if you use a VPN
Can police track online purchases made with a VPN There is no way to track live, encrypted VPN traffic. That's why police or government agencies who need information about websites you visited have to contact your internet service provider (ISP for short), and only then your VPN provider.
Can police get around VPN
With a VPN on, the user's online activities and data are encrypted. But, if the VPN software has security flaws and vulnerabilities, the police (or any other third party, for that matter) can use them to “break into” the VPN and see what data is being sent and received. So technically, the policy could track a VPN.
Are there any dangers in using a VPN
Key reasons not to use a free VPN include: Free VPN tools compromise user security: Many free VPN tools contain malware that could be used by cyber criminals to steal users' data, gain unauthorized access to their data or machine, or launch a cyberattack.
What VPN does not protect you from
Another common misconception is that a VPN protects you from online threats or cyberattacks. A VPN helps you stay invisible and behind the scenes, but it doesn't give you immunity against online risks like malware, ransomware, phishing attacks, or even computer viruses. That's where your antivirus software comes in.
Does VPN use TLS or SSL
SSL was replaced several years ago by Transport Layer Security (TLS), but the term "SSL" is still in common use for referring to the protocol. In addition to encrypting client-server communications in web browsing, SSL can also be used in VPNs.
Does VPN use IPsec or TLS
Many VPNs use the IPsec protocol suite to establish and run these encrypted connections. However, not all VPNs use IPsec. Another protocol for VPNs is SSL/TLS, which operates at a different layer in the OSI model than IPsec.
What is the difference between a VPN and a VPN tunnel
What is a VPN tunnel A VPN is a secure, encrypted connection over a publicly shared network. Tunneling is the process by which VPN packets reach their intended destination, which is typically a private network. Many VPNs use the IPsec protocol suite.
Which tunneling protocol is most commonly used for VPN
Point-to-Point Protocol (PPP) is used to encrypt the data between the connection. PPTP is one of the most widely used VPN protocol and has been in use since the early release of Windows.
What is the difference between SSH tunnel and TLS tunnel
The biggest difference between SSH and TLS/SSL is in what they're used for. SSH encrypts a connection between two computers and can execute commands. TLS/SSL encrypts data in transit as well, but it's typically in a website browser with HTTPS. You can't issue commands with TLS/SSL.
Is TLS layer 4 or 7
Because TLS operates at Layers 4 through 7 of the OSI model, as opposed to Layer 3, which is the case with IPsec, each application and each communication flow between client and server must establish its own TLS session to gain authentication and data encryption benefits.
Does SSL VPN use TLS
How SSL VPNs work. SSL VPNs rely on the TLS protocol, which has replaced the older SSL protocol, to secure remote access. SSL VPNs enable authenticated users to establish secure connections to internal HTTP and HTTPS services via standard web browsers or client applications that enable direct access to networks.
What are the two main protocols of TLS
The TLS and SSL protocols can be divided into two layers. The first layer consists of the application protocol and the three handshaking protocols: the handshake protocol, the change cipher spec protocol, and the alert protocol. The second layer is the record protocol.
Does TLS use TCP or UDP
TCP
TLS was designed to operate on top of a reliable transport protocol such as TCP. However, it has also been adapted to run over datagram protocols such as UDP.