Do I need a VPN with zero trust?
Summary
Contents
- 1 Summary
- 2 Key Points
- 3 1. Zero Trust Network Access vs. VPNs
- 4 2. Implementing Zero Trust Security
- 5 3. The Benefits of ZTNA
- 6 4. Alternatives to VPNs
- 7 5. The Importance of VPN Usage
- 8 6. Zero Trust Security and Firewalls
- 9 7. The Security of Zero Trust
- 10 Questions and Answers
- 10.1 1. Can ZTNA replace VPN?
- 10.2 2. What is the difference between VPN and zero trust network?
- 10.3 3. Do I need a VPN on trusted Wi-Fi?
- 10.4 4. What are the disadvantages of zero trust network?
- 10.5 5. Will zero trust replace VPN by 2025?
- 10.6 6. Is there a better solution than VPN?
- 10.7 7. Should I always use a VPN?
- 10.8 8. Does zero trust use firewalls?
- 10.9 9. How secure is zero trust?
- 10.10 10. Is VPN necessary in 2023?
- 11 Conclusion
This article focuses on the topic of zero trust network access (ZTNA) and its relation to virtual private networks (VPNs). It provides an overview of the differences between ZTNA and VPNs, explores the advantages and disadvantages of implementing a zero trust security strategy, and answers common questions related to VPN usage and alternatives. The article aims to provide insights from personal experience and present a clear understanding of the topic.
Key Points
1. Zero Trust Network Access vs. VPNs
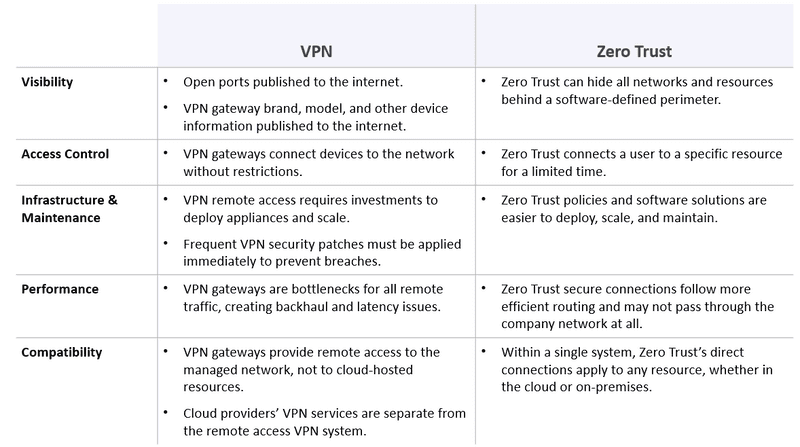
ZTNA offers an alternative to traditional VPNs, providing access only to explicitly authorized applications and services rather than allowing direct tunneled access to the entire corporate LAN.
2. Implementing Zero Trust Security
Implementing a zero trust security strategy can be expensive and complex, requiring significant changes to an organization’s network infrastructure and security policies. It may also increase the risk of user frustration and decrease productivity due to the need for multiple authentications.
3. The Benefits of ZTNA
ZTNA offers several benefits, including a logical access perimeter implemented as software, enhanced protection on trusted Wi-Fi networks, and the potential to replace VPNs entirely by 2025, according to Gartner.
4. Alternatives to VPNs
Other alternatives to VPNs include The Onion Router (Tor) network, which provides secure encryption and protects user data, and ZeroTier, which functions as an SD-WAN, P2P, and VPN solution.
5. The Importance of VPN Usage
Using a VPN is crucial for protecting data and privacy online, ensuring that every action remains anonymous and secure. While web applications are becoming more accessible and encrypted, a VPN adds an extra layer of protection.
6. Zero Trust Security and Firewalls
In a zero trust network, a segmentation gateway and Layer 7 firewall are commonly used to thoroughly vet users and data before granting access.
7. The Security of Zero Trust
Zero trust assumes that individuals, devices, and services attempting to access company resources cannot be automatically trusted and go through verification for every access request, enhancing overall security.
Questions and Answers
1. Can ZTNA replace VPN?
With a zero trust security strategy, VPNs are no longer a viable secure remote access solution. ZTNA offers an alternative with several benefits when compared to VPNs, including a logical access perimeter implemented as software.
2. What is the difference between VPN and zero trust network?
Unlike VPNs, which provide direct tunneled access to an endpoint on a corporate LAN, ZTNA provides access only to explicitly authorized applications and services.
3. Do I need a VPN on trusted Wi-Fi?
Using a VPN on trusted Wi-Fi networks adds an extra layer of protection, ensuring that your online activities cannot be monitored or followed by malicious individuals.
4. What are the disadvantages of zero trust network?
Implementing zero trust security can be expensive and complex, requiring significant changes to an organization’s network infrastructure and security policies. It may also increase the risk of user frustration and decrease productivity due to multiple authentications.
5. Will zero trust replace VPN by 2025?
Gartner predicts that zero trust network access (ZTNA) is the fastest-growing form of cybersecurity and will replace VPNs entirely by 2025.
6. Is there a better solution than VPN?
Alternative solutions to VPNs include The Onion Router (Tor) network, which protects user data with multiple layers of secure encryption, and ZeroTier, which functions as an SD-WAN, P2P, and VPN solution.
7. Should I always use a VPN?
It is recommended to always use a VPN when connected to the internet to protect your data and privacy from prying eyes. However, there may be exceptions for certain banking apps and services that may not work well with a VPN.
8. Does zero trust use firewalls?
In a zero trust network, a segmentation gateway and Layer 7 firewall are commonly used to thoroughly vet users and data before granting access.
9. How secure is zero trust?
Zero trust is a high-level strategy that verifies individuals, devices, and services for every access request, enhancing security even for resources inside the network.
10. Is VPN necessary in 2023?
While more advanced cybersecurity solutions are becoming available, using a VPN remains essential to ensure data and privacy protection.
Conclusion
ZTNA offers a viable alternative to traditional VPNs, providing greater control and security when accessing corporate resources. This article explored the advantages and disadvantages of zero trust security, highlighted the differences between VPNs and ZTNA, and discussed common questions related to VPN usage and alternatives. As the threat landscape evolves, understanding and implementing effective security measures become increasingly important.
Can ZTNA replace VPN
With a zero trust security strategy, VPNs are no longer a viable secure remote access solution. ZTNA offers an alternative with several benefits when compared to VPNs, including: Logical Access Perimeter: ZTNA implements the “perimeter” as software rather than the physical network boundary.
What is the difference between VPN and zero trust network
How Is ZTNA Different from VPN Unlike VPNs, which provide direct tunneled access to an endpoint on a corporate LAN, ZTNA provides access only to explicitly authorized applications and services.
Do I need VPN on trusted WIFI
Ensuring protection
To prevent this, it makes sense to use a VPN on a trusted network. You then connect to the network via the encrypted VPN tunnel. That means that you cannot be touched and followed by people with malicious will. Instead, you can simply go online without worry.
What are the disadvantages of zero trust network
It can be expensive and complex to implement, requiring significant changes to the organization's network infrastructure and security policies. Zero-trust security can also increase the risk of user frustration and reduce productivity, as users may need to authenticate multiple times to access different resources.
Will Gartner zero trust replace your VPN by 2025
Gartner believes that #zero-trust network access (#ZTNA) is the fastest-growing form of cybersecurity, will grow by 31% in 2023, and will replace #VPNs entirely by 2025. The study showed that zero trust network access is the security framework of the future and will replace virtual private networks by 2025.
Is there a better solution than VPN
The Onion Router
The Onion Router (Tor) network protects user data by encapsulating the data in multiple layers of secure encryption — using the Onion Protocol — as it routes the data from sender to receiver. The Tor process ensures that a user's identity is protected from ISPs and advertisers.
What type of VPN is ZeroTier
ZeroTier
| Developer(s) | ZeroTier, Inc. |
|---|---|
| Operating system | Microsoft Windows, macOS, Linux, Linux on ARM |
| Type | SD-WAN, P2P, VPN |
| License | Business Source License (Free for personal use. Enterprise pricing available); formerly GPLv3 |
| Website | https://www.zerotier.com |
Is VPN going away
Virtual private networks (VPNs) are becoming more obsolete, largely due to web applications being internet accessible and as powerful as their thick client predecessors that required VPNs. Plus, they are already encrypted with strong and robust cryptographic protocols like TLS.
Should you always use a VPN
You should use a Virtual Private Network (VPN) whenever you're online. By doing so, you make sure that your data and privacy are protected. Without a VPN, your every action online may be monitored and taken advantage of. A VPN encrypts all of your data, effectively hiding any information about you from prying eyes.
Should I leave my VPN on all the time on my iPhone
Should a VPN be on or off on an iPhone You should always keep your VPN on, regardless if you're using an iPhone or any other device connected to the internet. There are only a few exceptions, mainly related to banking apps and other services that may not work well with a VPN.
Does zero trust use firewalls
At the edge of a microperimeter, a zero trust network employs a segmentation gateway, which monitors the entry of people and data. It applies security measures that are designed to thoroughly vet users and data before to granting access using a Layer 7 firewall and the Kipling method.
How secure is zero trust
Zero Trust is a high-level strategy that assumes that individuals, devices, and services that are attempting to access company resources, even those inside the network, cannot automatically be trusted. To enhance security these users are verified every time they request access, even if they were authenticated earlier.
Is VPN necessary in 2023
While more advanced cybersecurity solutions are becoming available, a business VPN is still an essential part of your security toolkit in 2023. It provides you with a safe, reliable way to access the internet, shield your data from prying eyes, and comply with security and privacy regulations.
Do I need a VPN in 2023
We strongly recommend using a good VPN for everyday use as well as for work, particularly if your work involves handling sensitive information. At CNET, we rigorously test each virtual private network across major platforms to find the ones that provide exceptional privacy, reliability, speed and value.
Why should you not always use a VPN
Why shouldn't I use a VPN A VPN might reduce your connection speed even if your internet service provider isn't throttling your speed; Using a VPN on mobile will increase your mobile data usage; Using a VPN is considered an offense in some countries, and you can get fined or even be incarcerated for it.
Is there a downside to VPN
One reason why you may not want to use a VPN is because it could slow down your internet connection speed significantly. There are several factors that affect your internet speeds when using a VPN, including the fact that a VPN encrypts your data and routes it through different servers, which slows down the process.
What is the safest VPN type
What is the most secure VPN protocol Lightway, IKEv2, L2TP, and OpenVPN are all secure protocols, but the title of the most secure VPN protocol should go to Lightway, which uses wolfSSL, a well-established cryptography library that is FIPS 140-2 validated—which means it has been rigorously vetted by third parties.
How secure is ZeroTier
When you submit sensitive information via the website, your information is protected both online and offline. Wherever we collect sensitive information such as names, addresses, billing credentials, and phone numbers, that information is encrypted and transmitted to us in a secure way.
Why you shouldn’t use VPN all the time
Why shouldn't I use a VPN A VPN might reduce your connection speed even if your internet service provider isn't throttling your speed; Using a VPN on mobile will increase your mobile data usage; Using a VPN is considered an offense in some countries, and you can get fined or even be incarcerated for it.
What happens if I don’t use a VPN
Without a VPN, your ISP can see what sites you visit, how long you're on them, and information about your devices. Many ISPs share far more data than their customers expect, including their browsing history and location data, a recent FTC report revealed.
Is there a downside to using a VPN
One reason why you may not want to use a VPN is because it could slow down your internet connection speed significantly. There are several factors that affect your internet speeds when using a VPN, including the fact that a VPN encrypts your data and routes it through different servers, which slows down the process.
What happens if I dont use VPN
Governments, advertisers, and hackers can sometimes try to monitor your web browsing history. Without a virtual private network (VPN), your internet service provider (ISP) may record your online activity and sell it to the highest bidder.
Should you leave your VPN on all the time on your phone
The short answer is: Yes, you should keep your VPN on at all times. By encrypting the traffic that you send and receive, VPNs can prevent your personal data from being intercepted by third parties. This data includes your web browsing history, physical location, IP address, and more.
Do iPhones have built in VPN
There's no built-in VPN, but you can add free VPN configuration for iPhones in your phone settings: Select Settings. Select General. Choose VPN & Device Management.
What is the difference between firewall and ZTNA
Traditional firewalls work at a network level. Once you authenticate a remote user, they are free to access network resources. It can be difficult to limit the resources a user may access without complex firewall rules and convoluted network setups. ZTNA solutions instead work on an application level.