Can TLS be used for VPN?
Summary
Contents
In this article, we will explore the relationship between VPNs (Virtual Private Networks) and TLS (Transport Layer Security), and understand how they work together to provide secure and encrypted connections. We will also address common questions regarding the use of TLS in VPNs.
Main Thought
TLS, which replaced the older SSL (Secure Sockets Layer) protocol, is commonly used in VPNs as a means of encrypting client-server communications. While SSL is an outdated term, it is still used interchangeably with TLS in conversations about VPN security.
Key Points
1. The Use of TLS in VPNs
Many VPNs rely on the TLS protocol to establish secure connections for remote access. By using TLS, authenticated users can securely connect to internal HTTP and HTTPS services through web browsers or client applications, providing a layer of protection.
2. IPsec vs. TLS in VPNs
While many VPNs use the IPsec protocol suite for encrypted connections, some VPNs use SSL/TLS protocols instead. These protocols operate at different layers of the OSI model, providing different levels of security for VPN communications.
3. The Functioning of TLS Tunnel VPNs
In a TLS tunnel VPN, the Transport Layer Security protocol encrypts all data transmitted over the TCP connection. By doing so, the TLS tunnel enhances security and privacy for data sent from clients to servers, offering a more secure protocol for VPN connections.
4. The Significance of TLS in VPNs
Combining data authentication and encryption, TLS plays a vital role in VPN services to ensure privacy and data integrity. VPNs create virtual networks on top of physical data flows, allowing data packets to move through encrypted tunnels, evading potential snooping and safeguarding against unauthorized access.
5. The Relationship between SSL and VPNs
While VPNs and HTTPS both provide encryption for data protection, they serve different purposes and should not be regarded as exclusive to one another. For increased privacy and security, it is recommended to use both HTTPS and VPNs, particularly when using public or insecure networks.
Questions and Answers
1. Can TLS and IPSec be used together?
Yes, TLS and IPsec can be used together to provide confidentiality and integrity in communications. Both technologies offer encryption to enhance data security.
2. What type of encryption does VPN use?
There are two types of encryption used in VPNs: symmetric and asymmetric encryption. Symmetric encryption uses a shared key between two parties, while asymmetric encryption involves public and private keys.
3. What is the difference between SSL and TLS?
SSL is an older technology that provides a secure and encrypted communication channel. TLS is the upgraded version of SSL, fixing vulnerabilities and authenticating more efficiently while still supporting encryption.
4. How to set up a TLS tunnel VPN?
To set up a TLS tunnel VPN, select the desired connection method and configure the settings accordingly.
5. What is the difference between OpenVPN and TLS?
OpenVPN creates a virtual tunnel between devices and a VPN server using TLS encryption. TLS is a protocol that secures web traffic using certificates and keys.
6. Is VPN more secure than TLS?
VPN and TLS serve different purposes, with VPNs providing a higher level of security by encrypting all data traffic. TLS, on the other hand, secures communications between applications. It is recommended to use both for enhanced security.
We hope this article has shed light on the relationship between VPNs and TLS and answered your questions regarding their use together for secure and encrypted connections. By understanding the role of TLS in VPNs, you can make informed decisions about your online privacy and security.
Does VPN use TLS or SSL
SSL was replaced several years ago by Transport Layer Security (TLS), but the term "SSL" is still in common use for referring to the protocol. In addition to encrypting client-server communications in web browsing, SSL can also be used in VPNs.
Which VPN uses TLS
SSL VPNs rely on the TLS protocol, which has replaced the older SSL protocol, to secure remote access. SSL VPNs enable authenticated users to establish secure connections to internal HTTP and HTTPS services via standard web browsers or client applications that enable direct access to networks.
Does VPN use IPsec or TLS
Many VPNs use the IPsec protocol suite to establish and run these encrypted connections. However, not all VPNs use IPsec. Another protocol for VPNs is SSL/TLS, which operates at a different layer in the OSI model than IPsec.
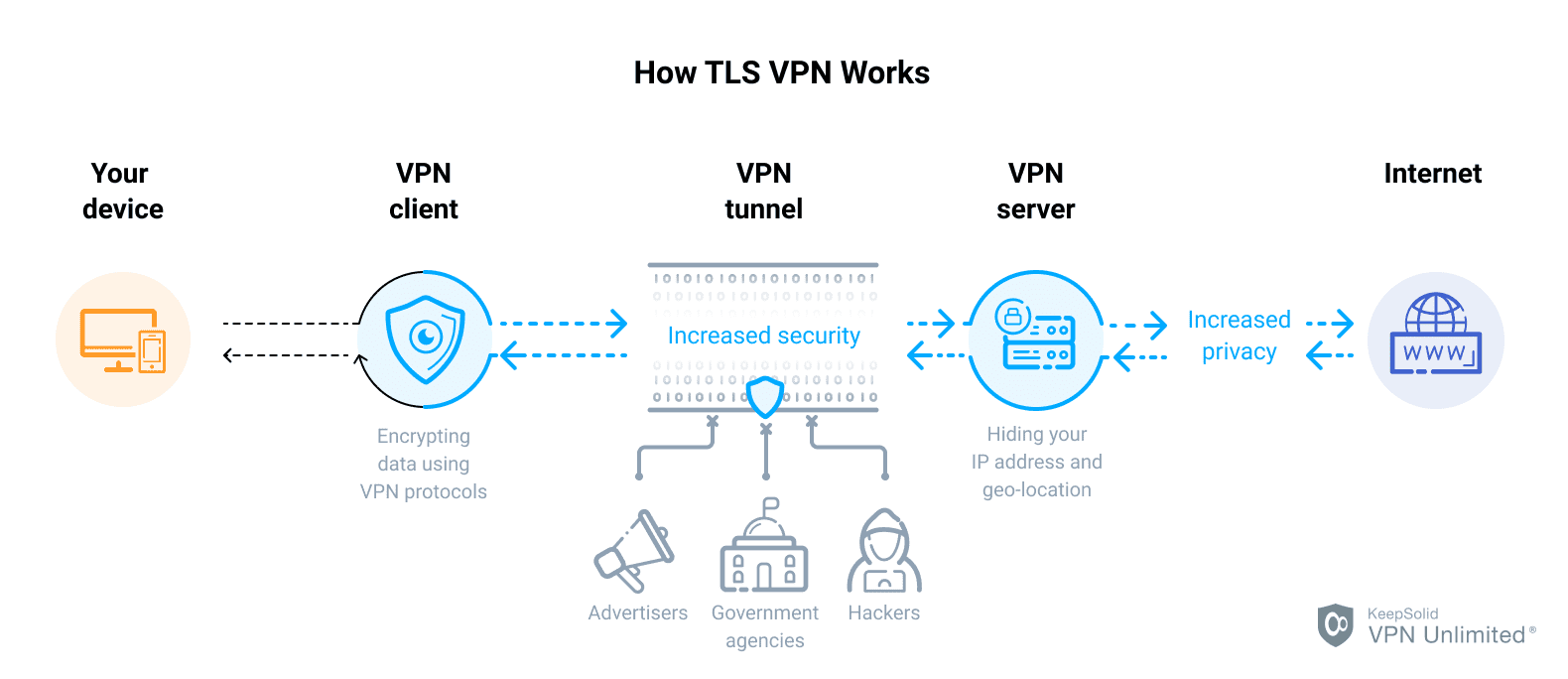
How does TLS tunnel VPN work
The Transport Layer Security (TLS) tunnel encrypts all data sent over the TCP connection. The TLS tunnel provides a more secure protocol across the Internet, gives the MFT IBM i Platform Server product the capability to encrypt all the data sent from a client to a server.
Do I need TLS on VPN
The combination of data authentication and encryption also makes TLS a good fit for VPN services, that protect Layer 4 data. A Virtual Private Network (VPN) is a service that creates a virtual network on top of physical data flows. Data packets move through encrypted tunnels that wrap payloads in unbreakable code.
Do I need SSL if I have VPN
The bottom line is that, although VPN and HTTPS can protect your data through encryption, they shouldn't be regarded as exclusive. In other words, not only is it good to combine HTTPS and VPN for increased privacy protection, but it's also recommended that you do so, especially on public, insecure networks.
Do I need TLS in a VPN
VPNs use a variety of security encryption protocols to protect your data from start to finish. One of the protocols used is Transport Layer Security (TLS). TLS is a cryptographic protocol that provides privacy and data integrity between two communicating applications.
Does NordVPN use TLS
With SSL/TLS encryption, your data is much safer – anyone snooping on your traffic can now only see scrambled data. These days, most websites use HTTPS. NordVPN uses it too!
Can TLS and IPSec be used together
Absolutely. In fact, I'm posting this answer using both IPSec (via VPN) and TLS (via HTTPS). As you noted, the technologies are similar as they both provide confidentiality and integrity on communications.
What type of encryption does VPN use
There are two types of VPN encryption: symmetric and asymmetric. Symmetric encryption uses a single key shared between two parties, while asymmetric encryption has public and private keys.
What is the difference between SSL and TLS
Transport Layer Security (TLS) is the upgraded version of SSL that fixes existing SSL vulnerabilities. TLS authenticates more efficiently and continues to support encrypted communication channels.
How to set up TLS tunnel VPN
And then click to select it. Now click on the pencil icon associated with the connection method.
What is the difference between OpenVPN and TLS
OpenVPN works by creating a virtual tunnel between your device and a VPN server using TLS encryption. TLS is a protocol that secures web traffic using certificates and keys.
What is difference between SSL and TLS
SSL is technology your applications or browsers may have used to create a secure, encrypted communication channel over any network. However, SSL is an older technology that contains some security flaws. Transport Layer Security (TLS) is the upgraded version of SSL that fixes existing SSL vulnerabilities.
Is VPN more secure than TLS
HTTPS only encrypts the data that travels between a browser and a website, while a VPN encrypts all data before it even leaves your device, including data on apps and websites that don't have HTTPS protection. VPNs generally use more advanced encryption methods.
Are VPNs always encrypted
Are VPNs always encrypted Yes, VPNs are always encrypted. In fact, the definition of a VPN is an encrypted tunnel that connects your computer to a network, typically a public network.
Can I use TLS instead of SSL
At present, all SSL certificates are no longer in use. TLS certificates are the industry standard. However, the industry continues to use the term SSL to refer to TLS certificates. TLS certificates have iterated upon SSL certificates and improved them over time.
Can you use TLS without SSL
Without an SSL certificate, a website's traffic can't be encrypted with TLS. Technically, any website owner can create their own SSL certificate, and such certificates are called self-signed certificates.
Do hackers use TLS
CRIME attack
An attacker can use a malicious JavaScript code to inject guesses into the TLS stream, and then measure the size of the compressed ciphertext to infer the plaintext.
Does TLS encrypt IP
A primary use case of TLS is encrypting the communication between web applications and servers, such as web browsers loading a website. TLS can also be used to encrypt other communications such as email, messaging, and voice over IP (VoIP).
What is the strongest encryption for VPN
Security. OpenVPN and WireGuard are protocols that can offer the most robust encryption and the highest level of security. OpenVPN uses an AES 256-bit encryption key, widely used by top-tier entities, such as NASA and the military.
What is the best encryption for site to site VPN
Based on these facts, you should choose based on security requirements and compatibility on your customer gateway. However, we recommend AES-256.
Is TLS preferred over SSL
TLS is an updated, more secure version of SSL. We still refer to our security certificates as SSL because it's a more common term, but when you buy SSL from DigiCert, you get the most trusted, up-to-date TLS certificates.
How do I set up TLS protocol
Google ChromeOpen Google Chrome.Click Alt F and select Settings.Scroll down and select Show advanced settingsScroll down to the Network section and click on Change proxy settingsSelect the Advanced tab.Scroll down to Security category, manually check the option boxes for Use TLS 1.0,Use TLS 1.1 and Use TLS 1.2.
How to setup TLS encryption
To enable encryption to an endpoint node, toggle the TLS Enablement switch to On. The Navigator application then attempts to establish an encrypted connection. If the host servers are properly configured with a Digital Certificate, this certificate is passed back to the Navigator application.