Can TLS and IPsec be used together?
Summary
Contents
- 1 Summary
- 2 Main Thought
- 3 Main Thought
- 4 Key Points
- 5 1. Main Thought
- 6 2. Main Thought
- 7 3. Main Thought
- 8 4. Main Thought
- 9 5. Main Thought
- 10 6. Main Thought
- 11 7. Main Thought
- 12 8. Main Thought
- 13 Questions and Answers
- 13.1 1. Question: Can TLS and IPsec be used together?
- 13.2 2. Question: What is the difference between IPsec and TLS?
- 13.3 3. Question: Does VPN use IPsec or TLS?
- 13.4 4. Question: What types of encryption can be utilized with IPsec?
- 13.5 5. Question: What protocol is used with IPsec?
- 13.6 6. Question: Does TLS perform tunneling?
- 13.7 7. Question: What is the best encryption for IPsec?
- 13.8 8. Question: Does VPN use TLS?
- 13.9 9. Question: Do you need TLS with VPN?
- 13.10 10. Question: What is the most secure mode for IPsec?
- 13.11 11. Question: What are the protocols used by IPsec?
- 13.12 12. Question: What are the disadvantages of IPsec?
- 13.13 13. Question: Is TLS considered a VPN?
- 13.14 14. Question: Is TLS an encrypted tunnel?
In this article, I will explore the relationship between TLS and IPsec, their differences, and their use in VPNs. I will also discuss the encryption methods used by IPsec and the protocols it relies on. Additionally, I will address common questions related to the use of TLS and IPsec in VPNs.
Main Thought
TLS and IPsec are both used for establishing secure connections, but they operate at different layers of the OSI model. While IPsec functions at the network layer, TLS operates at the application layer. Despite their differences, both protocols can be used for VPNs.
Main Thought
IPsec has a smaller attack surface compared to TLS. This is because IPsec performs critical security tasks, such as key functions, in a siloed environment within the operating system kernel. In contrast, TLS typically runs in the user space from the application layer.
Key Points
1. Main Thought
Many VPNs use the IPsec protocol suite to establish and run encrypted connections. However, not all VPNs use IPsec. Another protocol commonly used in VPNs is SSL/TLS, which operates at a different layer in the OSI model.
2. Main Thought
IPsec utilizes both asymmetric and symmetric encryption for secure data transfer. Asymmetric encryption involves a public key for encryption and a private key for decryption, while symmetric encryption uses the same key for both encryption and decryption.
3. Main Thought
The three main protocols comprising IPsec are Authentication Header (AH), Encapsulating Security Payload (ESP), and Internet Key Exchange (IKE).
4. Main Thought
TLS creates a secure tunnel for data sent over a TCP connection. It encrypts all data to provide a more secure protocol across the Internet. TLS is commonly used in VPNs to add an additional layer of security for web users.
5. Main Thought
The Advanced Encryption Standard (AES) is considered the strongest encryption algorithm available for IPsec. AES encryption keys can have lengths of 128, 192, or 256 bits, and it offers faster performance compared to 3DES encryption.
6. Main Thought
SSL VPNs, which rely on the TLS protocol, allow authenticated users to establish secure connections to internal HTTP and HTTPS services. SSL VPNs can be accessed via standard web browsers or client applications.
7. Main Thought
The combination of data authentication and encryption makes TLS a good fit for VPN services that aim to protect Layer 4 data. VPNs create a virtual network on top of physical data flows.
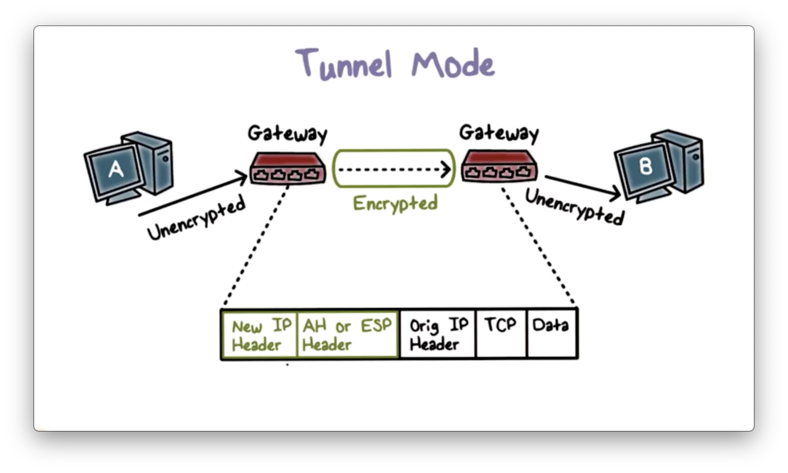
8. Main Thought
IPsec tunnel mode provides a more secure connection because it encapsulates the entire original packet within an additional IP header. This offers better security compared to IPsec transport mode, where only the payload is encrypted.
Questions and Answers
1. Question: Can TLS and IPsec be used together?
Answer: Yes, TLS and IPsec can be used together. While they function at different layers of the OSI model, both protocols can be used in VPNs to establish secure connections.
2. Question: What is the difference between IPsec and TLS?
Answer: The main difference lies in their operation at different layers of the OSI model. IPsec functions at the network layer, while TLS operates at the application layer. Additionally, IPsec has a smaller attack surface compared to TLS.
3. Question: Does VPN use IPsec or TLS?
Answer: Many VPNs use the IPsec protocol suite for establishing encrypted connections. However, not all VPNs utilize IPsec. Some VPNs use SSL/TLS, which operates at a different layer of the OSI model.
4. Question: What types of encryption can be utilized with IPsec?
Answer: IPsec utilizes both asymmetric and symmetric encryption. Asymmetric encryption involves a public key and a private key, while symmetric encryption uses the same key for both encryption and decryption.
5. Question: What protocol is used with IPsec?
Answer: The three main protocols comprising IPsec are Authentication Header (AH), Encapsulating Security Payload (ESP), and Internet Key Exchange (IKE).
6. Question: Does TLS perform tunneling?
Answer: Yes, TLS creates a tunnel that encrypts all data sent over the TCP connection. This provides a more secure protocol across the Internet and adds an additional layer of security for data transmission.
7. Question: What is the best encryption for IPsec?
Answer: AES (Advanced Encryption Standard) is considered the strongest encryption algorithm for IPsec. AES encryption keys can have lengths of 128, 192, or 256 bits. AES offers better performance compared to 3DES.
8. Question: Does VPN use TLS?
Answer: SSL VPNs rely on the TLS protocol to establish secure connections for remote access. TLS enables authenticated users to connect to internal HTTP and HTTPS services using standard web browsers or client applications.
9. Question: Do you need TLS with VPN?
Answer: TLS, with its data authentication and encryption capabilities, is a good fit for VPN services that aim to protect Layer 4 data. VPNs create a virtual network on top of physical data flows.
10. Question: What is the most secure mode for IPsec?
Answer: IPsec tunnel mode is considered more secure as it encapsulates the entire original packet within an additional IP header. This ensures that the entire packet is encrypted, providing stronger security compared to IPsec transport mode.
11. Question: What are the protocols used by IPsec?
Answer: The three main protocols used by IPsec are Authentication Header (AH), Encapsulating Security Payload (ESP), and Internet Key Exchange (IKE).
12. Question: What are the disadvantages of IPsec?
Answer: IPsec can have compatibility issues with some network devices and applications, which may lead to interoperability problems. Additionally, IPsec can impact network performance due to the overhead of encryption and decryption of IP packets.
13. Question: Is TLS considered a VPN?
Answer: TLS VPNs are usually clientless and do not require separate software for connections and access control. They work seamlessly with most modern websites, adding another layer of cybersecurity for web users.
14. Question: Is TLS an encrypted tunnel?
Answer: Yes, the TLS tunnel encrypts all data sent over the TCP connection. This provides a more secure protocol and enables the encryption of all data sent from a client to a server.
Can TLS be used with IPsec
IPsec and SSL/TLS function at different layers of the OSI model, but both can be used for VPNs.
What is the difference between IPsec and TLS
IPsec has a smaller attack surface*.
IPsec's critical security tasks (such as functions that use keys) are performed in a siloed environment within the operating system kernel, while TLS typically runs in the user space from the application layer.
Does VPN use IPsec or TLS
Many VPNs use the IPsec protocol suite to establish and run these encrypted connections. However, not all VPNs use IPsec. Another protocol for VPNs is SSL/TLS, which operates at a different layer in the OSI model than IPsec.
What two different types of encryption can be utilized with IPsec
IPSec uses asymmetric and symmetric encryption to provide speed and security during data transfer. In asymmetric encryption, the encryption key is made public while the decryption key is kept private. Symmetric encryption uses the same public key for encrypting and decrypting data.
What protocol is used with IPsec
The three main protocols comprising IPsec are: Authentication Header (AH), Encapsulating Security Payload (ESP), and Internet Key Exchange (IKE).
Does TLS perform tunneling
The Transport Layer Security (TLS) tunnel encrypts all data sent over the TCP connection. The TLS tunnel provides a more secure protocol across the Internet, gives the MFT IBM i Platform Server product the capability to encrypt all the data sent from a client to a server.
What is the best encryption for IPsec
AES (Advanced Encryption Standard) — AES is the strongest encryption algorithm available. Fireware can use AES encryption keys of these lengths: 128, 192, or 256 bits. AES is faster than 3DES.
Does VPN use TLS
How SSL VPNs work. SSL VPNs rely on the TLS protocol, which has replaced the older SSL protocol, to secure remote access. SSL VPNs enable authenticated users to establish secure connections to internal HTTP and HTTPS services via standard web browsers or client applications that enable direct access to networks.
Do you need TLS with VPN
The combination of data authentication and encryption also makes TLS a good fit for VPN services, that protect Layer 4 data. A Virtual Private Network (VPN) is a service that creates a virtual network on top of physical data flows.
What is the most secure mode for IPsec
The main advantage of IPsec tunnel mode is that it creates a secure connection between two endpoints by encapsulating packets in an additional IP header. Tunnel mode also provides better security over transport mode because the entire original packet is encrypted.
What are the 3 main protocols that IPSec uses
The three main protocols comprising IPsec are: Authentication Header (AH), Encapsulating Security Payload (ESP), and Internet Key Exchange (IKE).
What are the disadvantages of IPSec
Disadvantages of IPSec
Compatibility issues: IPSec can have compatibility issues with some network devices and applications, which can lead to interoperability problems. Performance impact: IPSec can impact network performance due to the overhead of encryption and decryption of IP packets.
Is TLS considered a VPN
TLS VPNs are usually clientless. There is no need for separate software to establish connections and control access. This style of VPN also works with HTTP, allowing it to work seamlessly with most modern websites. It functions in the background, adding another cybersecurity barrier for web users.
Is TLS an encrypted tunnel
The Transport Layer Security (TLS) tunnel encrypts all data sent over the TCP connection. The TLS tunnel provides a more secure protocol across the Internet, gives the MFT IBM i Platform Server product the capability to encrypt all the data sent from a client to a server.
Which 3 types of authentication can be used for IPsec site to site VPNs
The three main protocols comprising IPsec are: Authentication Header (AH), Encapsulating Security Payload (ESP), and Internet Key Exchange (IKE).
Is IPsec more secure than SSL
Once a user is logged into the network, SSL takes the upper hand in security. SSL VPNs work by accessing specific applications whereas IPsec users are treated as full members of the network. It's therefore easier to restrict user access with SSL.
Which is more secure TLS or IPsec
IPsec is more resistant to DoS attacks because it works at a lower layer of the network. TLS uses TCP, making it vulnerable to TCP SYN floods, which fill session tables and cripple many off-the-shelf network stacks.
Does TLS protect against IP spoofing
Use of secure protocols: By authenticating the sender's identity, protocols such as Secure Sockets Layer (SSL) and Transport Layer Security (TLS) can help prevent IP spoofing.
Why use TLS over IPsec
SSL/TLS VPN products protect application traffic streams from remote users to an SSL/TLS gateway. In other words, IPsec VPNs connect hosts or networks to a protected private network, while SSL/TLS VPNs securely connect a user's application session to services inside a protected network.
Do VPNs use SSL or TLS
Although they kept the name of their original Secure Sockets Layer (SSL) protocol, today's SSL VPNs use the more secure Transport Layer Security (TLS) protocol.
Is IPSec more secure than SSL
Once a user is logged into the network, SSL takes the upper hand in security. SSL VPNs work by accessing specific applications whereas IPsec users are treated as full members of the network. It's therefore easier to restrict user access with SSL.
Which VPN protocol is best for IPSec
IKEv2/IPsec provides a strong connection over mobile devices and allows users to switch between networks without risking their security. This makes it the most stable VPN protocol for mobile devices. Bypassing firewalls and restrictions.
What is the biggest limitation of IPsec
As a result, all traffic will be dropped by FW1. Thus, meeting each policy's corresponding requirements may lead to conflicts. Additionally, one of the biggest disadvantages of IPsec is its complexity. Although IPsec's flexibility makes it popular, it can also be confusing.
Why not to use IPsec
Disadvantages of IPSec
Compatibility issues: IPSec can have compatibility issues with some network devices and applications, which can lead to interoperability problems. Performance impact: IPSec can impact network performance due to the overhead of encryption and decryption of IP packets.
Is VPN more secure than TLS
HTTPS only encrypts the data that travels between a browser and a website, while a VPN encrypts all data before it even leaves your device, including data on apps and websites that don't have HTTPS protection. VPNs generally use more advanced encryption methods.